Where Do I Put RDP Certificates to Avoid This Pesky Error?
I need to resolve an issue that's been frustrating me for a long time now.
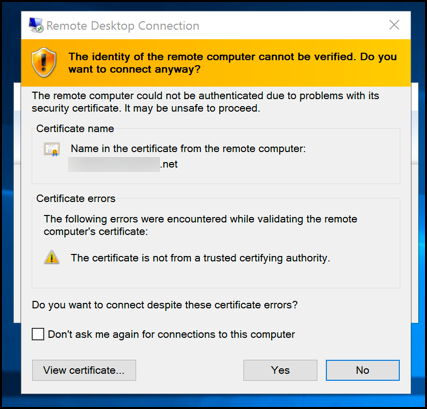
I've got a small network that I use RDP to login to and whenever I sign-in to a server I get an error:
"The remote computer could not be authorized due to problems with its security certificate. It may be unsafe to proceed. The certificate is not from a trusted certifying authority."
I have created a Self-Signed Certificate using myself as a CA. I can get this to work for sites in IIS, but not for logging into servers on my network.
I have placed the CA Root certificate in the "Trusted Root Certificate Authorities" folder on both the Server I'm logging into and my local Windows machine.
I've put a PFX version of the Certificate in the "Personal" -> "Certificates" folder.
I've put a PFX version of the Certificate in the "Remote Desktop" -> "Certificates" folder.
What am I missing here? Where do I put in the TLS Certificate and Root CA?
I've got a small network that I use RDP to login to and whenever I sign-in to a server I get an error:
"The remote computer could not be authorized due to problems with its security certificate. It may be unsafe to proceed. The certificate is not from a trusted certifying authority."

I have created a Self-Signed Certificate using myself as a CA. I can get this to work for sites in IIS, but not for logging into servers on my network.
I have placed the CA Root certificate in the "Trusted Root Certificate Authorities" folder on both the Server I'm logging into and my local Windows machine.
I've put a PFX version of the Certificate in the "Personal" -> "Certificates" folder.
I've put a PFX version of the Certificate in the "Remote Desktop" -> "Certificates" folder.
What am I missing here? Where do I put in the TLS Certificate and Root CA?
The thumbprint can be set up in Group Policy and so long as the certificate is a trusted third party without the need for any Intermediates work it will just work.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks guys! I appreciate the quick responses:
@arnold - I've used OpenSSL to generate a CA .PEM and variousl keys, all the way down to a PFX for transport. I basically followed these directions: https://deliciousbrains.com/ssl-certificate-authority-for-local-https-development/ - Essentially creating myself as a CA. These are the certificates I'd like to use. You are essentially suggesting importing the PEM key into 'Trusted Root Certification Authorities' -> 'Certificates' and this is done on my local machine, is that correct? Would there be any other certificates or location to stick them using the Certificates snap-in?
@Philip - I'm intrigued by the GPO. Which Group Policy are you suggesting specifically? I'm not in a place to purchase a third-party cert so I'm sorta stuck with this self-signed method using the link I mentioned above.
@McKnife - When I use the full name of the machine, this works.
@arnold - I've used OpenSSL to generate a CA .PEM and variousl keys, all the way down to a PFX for transport. I basically followed these directions: https://deliciousbrains.com/ssl-certificate-authority-for-local-https-development/ - Essentially creating myself as a CA. These are the certificates I'd like to use. You are essentially suggesting importing the PEM key into 'Trusted Root Certification Authorities' -> 'Certificates' and this is done on my local machine, is that correct? Would there be any other certificates or location to stick them using the Certificates snap-in?
@Philip - I'm intrigued by the GPO. Which Group Policy are you suggesting specifically? I'm not in a place to purchase a third-party cert so I'm sorta stuck with this self-signed method using the link I mentioned above.
@McKnife - When I use the full name of the machine, this works.
ASKER
Thanks guys! All your suggestions are great and since I'm accessing just a handful of servers, the local solution of adding to TRA works for me.
View certificateID.
You may have to use a tool like openssl to get the cert that you can then use to add.
I personally if this is not a public RDS server and is just there for you, just go with it.
What is the issue you have with error?
A self signed certificate is only trusted by the one who generated and is fully aware of it.
The alternative is you are to buy and repeatedly pay to renew a certificate that is signed by a trusted public ca.