Skale
asked on
How to fix warning CA2100 for OLEDB connection in C#
Hi,
I need an expert view for the below code;
It gives a warning like on attached picture.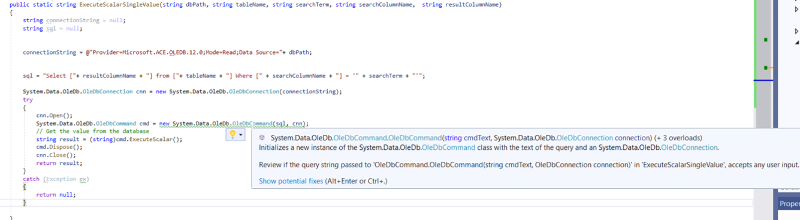
It directs me to this page: https://docs.microsoft.com/en-us/visualstudio/code-quality/ca2100?view=vs-2019
But i couldn't be able to fix that warning.
Any help would be grateful.
I need an expert view for the below code;
public static string ExecuteScalarSingleValue(string dbPath, string tableName, string searchTerm, string searchColumnName, string resultColumnName)
{
string connectionString = null;
string sql = null;
connectionString = @"Provider=Microsoft.ACE.OLEDB.12.0;Mode=Read;Data Source="+ dbPath;
sql = "Select ["+ resultColumnName + "] from ["+ tableName + "] Where [" + searchColumnName + "] = '" + searchTerm + "'";
System.Data.OleDb.OleDbConnection cnn = new System.Data.OleDb.OleDbConnection(connectionString);
try
{
cnn.Open();
System.Data.OleDb.OleDbCommand cmd = new System.Data.OleDb.OleDbCommand(sql, cnn);
// Get the value from the database
string result = (string)cmd.ExecuteScalar();
cmd.Dispose();
cnn.Close();
return result;
}
catch (Exception ex)
{
return null;
}
}It gives a warning like on attached picture.

It directs me to this page: https://docs.microsoft.com/en-us/visualstudio/code-quality/ca2100?view=vs-2019
But i couldn't be able to fix that warning.
Any help would be grateful.
By restructuring your code, e.g. this should work:
p.s. you method name is suboptimal. A scalar is per definition a single value. Thus the name contains a redundant part.
public static string ExecuteScalarSingleValue(string databaseFilename, string tableName, string searchTerm, string searchColumnName, string resultColumnName)
{
const string CONNECTION_STRING = "Provider=Microsoft.ACE.OLEDB.12.0;Mode=Read;Data Source={0}";
const string COMMAND_TEXT = "SELECT [{0}] FROM [{1}] WHERE [{2}] = @searchTerm;";
string connectionString = string.Format(CONNECTION_STRING, databaseFilename);
using (OleDbConnection connection = new OleDbConnection(connectionString)
{
connection.Open();
string commandText = string.Format(COMMAND_TEXT, resultColumnName, tableName, searchColumnName);
using (OleDbCommand command = new OleDbCommand(commandText, connection))
{
command.Parameters.Add(new OleDbParameter("@searchTerm", searchTerm));
return (string)command.ExecuteScalar();
}
}
}p.s. you method name is suboptimal. A scalar is per definition a single value. Thus the name contains a redundant part.
ASKER
Hi ste5an,
Problem continues as on attachment.
@Chris Stanyon you mean there's no additional solution, if you are trust your injection just supress it?
Problem continues as on attachment.
@Chris Stanyon you mean there's no additional solution, if you are trust your injection just supress it?
hmm, what VS version? What target framework? This does not raise this warning:
namespace ConsoleCS
{
using System;
using System.Data.OleDb;
public class Program
{
public static void Main(string[] args)
{
Console.WriteLine(ExecuteScalarSingleValue(@"C:\Temp\myDatabase.accdb", "Table1", "1", "ID", "Payload"));
Console.WriteLine("\nDone.");
Console.ReadLine();
}
public static string ExecuteScalarSingleValue(string databaseFilename, string tableName, string searchTerm, string searchColumnName, string resultColumnName)
{
const string CONNECTION_STRING = "Provider=Microsoft.ACE.OLEDB.12.0;Mode=Read;Data Source={0}";
const string COMMAND_TEXT = "SELECT [{0}] FROM [{1}] WHERE [{2}] = @searchTerm;";
string connectionString = string.Format(CONNECTION_STRING, databaseFilename);
using (OleDbConnection connection = new OleDbConnection(connectionString))
{
connection.Open();
string commandText = string.Format(COMMAND_TEXT, resultColumnName, tableName, searchColumnName);
using (OleDbCommand command = new OleDbCommand(commandText, connection))
{
command.Parameters.Add(new OleDbParameter("@searchTerm", searchTerm));
return (string)command.ExecuteScalar();
}
}
}
}
}ASKER
Hi ste5an, result is same.
I'm using VS2019, .NET4.7.2, Release-Any CPU
I'm using VS2019, .NET4.7.2, Release-Any CPU
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
The suggested code fix for that is to change to using a parameterised query. This removes the risk of SQL injection. On the page you linked to, scroll down and you'll find examples of how to run your query with parameters.
However, you won't be able to use the tableName, searchColumnName or resultColumnName as parameters (that's just not how it works).
Of course, if the method arguments are coming from a know, safe call, then you can just suppress the error and move on.