Uncertain about VLAN routing in this Wireless scenario.
I have been able to set VLANS in L2 and L3 Switches, but have no experience when it comes to configuring correctly VLANS when Wireless AP's are involved as part of the topology.
Scenario:
I can configure the WLAN SSID and VLAN in Hivemanager and the isolation works as expected. Ditto for the L2 Switch VLAN.
What I am struggling with is what properties do I configure on the switch to make sure traffic from each VLAN'd SSID is routed correctly in the L2 switch?
The Switch port map looks something like this
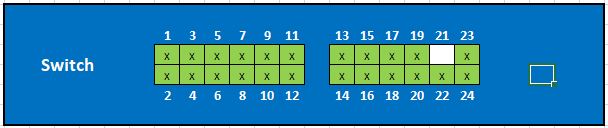 Ports 01-08 POE to the Aerohive AP's (No VLAN config yet)
Ports 01-08 POE to the Aerohive AP's (No VLAN config yet)
Ports 09-10 IoT devices (VLAN ID 22 - Ports Tagged)
Ports 11-16, 20-24
Port2 17-19 Reserved for new system (VLAN ID 66 - Ports Tagged)
Questions ?
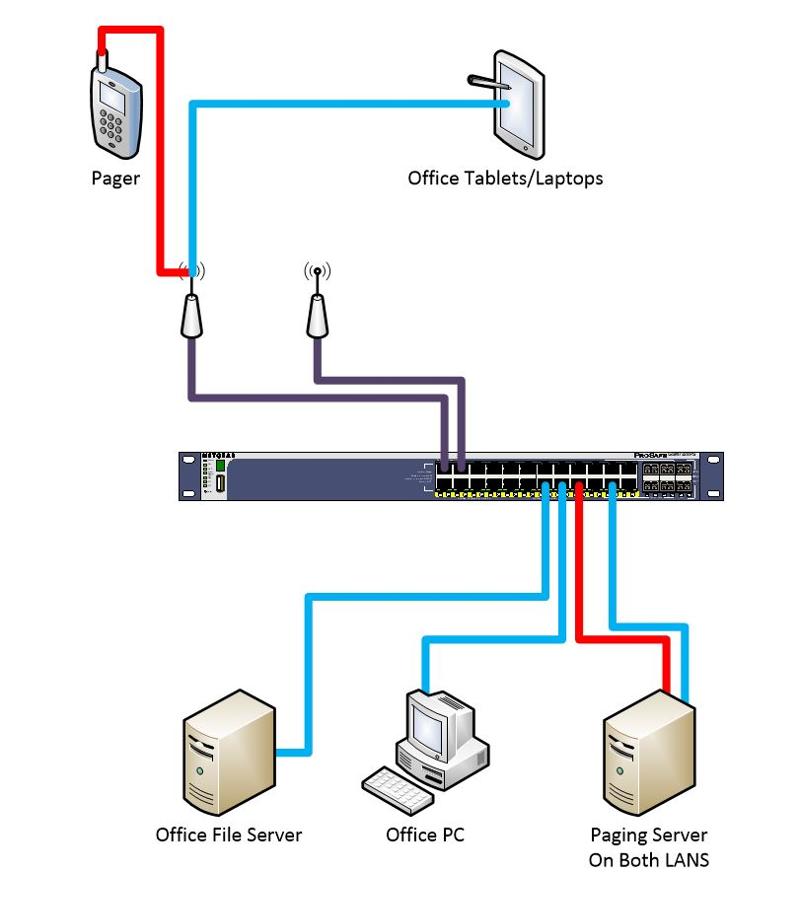
Logic diagram.
Key -
Scenario:
- We have VLANS configured on the L2 switch, which segregates IoT devices from the Business Data Lan (consisting of servers, workstations, tablets etc).
- Existing devices connected to the AP's have no VLAN config set, as it is all managed at the switch.
- A new wireless connected system is being deployed that requires a seperate SSID and seperate VLAN in our Aerohive WLAN. The AP's in this are powered from the same L2 switch as above.
- The switch is a Netgear M4100-24 POE+
I can configure the WLAN SSID and VLAN in Hivemanager and the isolation works as expected. Ditto for the L2 Switch VLAN.
What I am struggling with is what properties do I configure on the switch to make sure traffic from each VLAN'd SSID is routed correctly in the L2 switch?
The Switch port map looks something like this
Ports 09-10 IoT devices (VLAN ID 22 - Ports Tagged)
Ports 11-16, 20-24
Port2 17-19 Reserved for new system (VLAN ID 66 - Ports Tagged)
Questions ?
- Do I have to create a new VLAN for the Data LAN (e.g. VLAN 10), or is PVID an alternate here - assuming my understanding that PVID deals with Traffic that isn't tagged comming into a switch port, and would therefore route traffic not assigned a VLAN ID in their config to a default VLAN
- Place all of the POE ports into both VLAN 66 and the new VLAN 10
- What do I do about the PVID
Logic diagram.
Key -
- Red Line = new Paging System Traffic flow via VLAN
- Blue - Existing Office devices
- Purple - Traffic flow via Multiple assigned VAN's
To add onto what noci mentioned above. You will need to tag the vlans on the switch port that the Access point is connected two only if you are configuring multiple SSID's on it and each SSID in a separate vlan. If not, and you are only using one SSID on the AP and one vlan, then just configure the switchport for untagged with the VLAN the SSID is going to use.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Sorry about the delay on getting back to everyone on this. It's a health care site and once Covid-19 surfaced the place went into lockdown and all projects suspended. They are now coming out of this and will resume.
ASKER
Hi all.
The Nurecall SSID will have its own VLAN, as will any devices related to the Nursecall. The remaining devices (non Nursecall servers/tablets/desktops/printers/etc) will remain on the default VLAN. We have another entrenched product on the site that does not support VLAN's, so this seems the only way to address it. Will this be OK?
The advice being provided looks very inspiring.
The Nurecall SSID will have its own VLAN, as will any devices related to the Nursecall. The remaining devices (non Nursecall servers/tablets/desktops/printers/etc) will remain on the default VLAN. We have another entrenched product on the site that does not support VLAN's, so this seems the only way to address it. Will this be OK?
The advice being provided looks very inspiring.
For L2 you need IEEE 802.1Q settings.
named VLAN (with a tag id) Unmanaged L2 switches cannot handle those. For managed switches they do need to support 802.1q or dot1q.