2008 Certificate CA Server - Upgrade, Toss, Azure?
We have an Old Windows 2008 R2 VM that has a CA installed on it.
It has been giving out <domain>\<Machine>$ and <domain>\<User> Certs.
Nothing else on the Machine. I've never been a Fan of Upgrading Servers vs Fresh installs. There are no Certs on here besides the ones that it gave to the PCs and Users. No Special Templates or anything. I May have used it for an Exchange Server, though have a Wildcard Cert for that now.
What is best to replace this CA. Do I need to replace it?
Thanks!
It has been giving out <domain>\<Machine>$ and <domain>\<User> Certs.
Nothing else on the Machine. I've never been a Fan of Upgrading Servers vs Fresh installs. There are no Certs on here besides the ones that it gave to the PCs and Users. No Special Templates or anything. I May have used it for an Exchange Server, though have a Wildcard Cert for that now.
What is best to replace this CA. Do I need to replace it?
Thanks!
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
No... Went to 2012R2, then to 2016... Not jumping on the 2019 bandwagon for a little while yet...
ASKER
Yeah, I just didn't want to jump through all of the incremental upgrades and then end up with a PC that's been patched several times with lots of leftovers laying around.
Possible I'm just remembering the old Upgrade Days that it was a pain and left tons of crap around?
THanks!
Possible I'm just remembering the old Upgrade Days that it was a pain and left tons of crap around?
THanks!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Although I would not upgrade a heavily used server, a server only running CA services is much less likely to have upgrade issues...
ASKER
It is only running CA Services, though Seems like a waste. It used to be more, though we removed all of its other used. I was hoping to put the new CA on a Different Server, new Name, new IP, new Everything.
Thanks!
Thanks!
Virtualize... Every license of 2016 or higher lets you run 2 virtual servers on the hardware...
It is virtualized.
I think the another server, means new physical host.
or new OS version.
I think the another server, means new physical host.
or new OS version.
ASKER
Virtualize... Every license of 2016 or higher lets you run 2 virtual servers on the hardware...Ha, is there an option to NOT Virtualize? We are Running on a Hyper-V Cluster at the moment and are moving to an ESXi Cluster. In prepairing to 'Migrate' the services in the Hyper-V Cluster to the ESXi Cluster are are trying to pair-down the resources. The Existing Win2008R2 CA is a VM.
I think I might add a second CA and just start pointing to it like Arnold mentioned and then when no one is pointing to the old one, remove it.
With a CA Expiration Date of: Thursday, November 10, 2022 10:52:58 AM Will I need to Keep it around that long, or once I get everything pointed to the new one I should be okay? Assuming I can get all of the PCs to re-certificate themselves and create new certs for our couple internal uses.
look at adjusting your PKI setup
ROOT CA VM almost always offline.
then have two VMS that are issueing CAs whose certs are signed/issued by the Root CA.
the root CA need only be brought back to renew its own cert, and sign the issuing CA;s CERTs every five years or so.....
this way the systems/users have two redundant Issueing CAs to whom to send requests ....'
When is the oldest Client Issued certificaste expires?
While the CA's cert expires in two years, your issued certs might only be valid for one year from issue..
You should use the issued cert expiration date as the determinant when to cut it over.
You can unpublish the 2008 CA from being available while publishing the new CA for any new certs.
ROOT CA VM almost always offline.
then have two VMS that are issueing CAs whose certs are signed/issued by the Root CA.
the root CA need only be brought back to renew its own cert, and sign the issuing CA;s CERTs every five years or so.....
this way the systems/users have two redundant Issueing CAs to whom to send requests ....'
When is the oldest Client Issued certificaste expires?
While the CA's cert expires in two years, your issued certs might only be valid for one year from issue..
You should use the issued cert expiration date as the determinant when to cut it over.
You can unpublish the 2008 CA from being available while publishing the new CA for any new certs.
ASKER
look at adjusting your PKI setup
ROOT CA VM almost always offline.
then have two VMS that are issueing CAs whose certs are signed/issued by the Root CA.
the root CA need only be brought back to renew its own cert, and sign the issuing CA;s CERTs every five years or so.....
this way the systems/users have two redundant Issuing CAs to whom to send requests ....'
Whoa, going from one CA, which I didn't think was really used, to having 3 CAs? Can the CA Still be installed on a DC?
Looks like PCs are renewing today, so March 11, 2021
When is the oldest Client Issued certificaste expires?
While the CA's cert expires in two years, your issued certs might only be valid for one year from issue..
You should use the issued cert expiration date as the determinant when to cut it over.
You can unpublish the 2008 CA from being available while publishing the new CA for any new certs.
So as long as the New_CA has a Root CA Cert from Old_CA Installed, it can validate the Old_CA Certs and with AD Pointing to New_CA, new Cert Requests will go to New_CA.
Thanks again!
yes, but a ca installed on a DC would usually be seen as an enterprise CA.
You could backup CA then restore CA.....
The concern, issue deals with templates, etc.
Before the one renews today, look at changing the Cert template for computer certs to a shorter window i.e. three months instead of the current year.
backup CA and restart the CA data onto the new CA is an option though checking whether it has a range of version to version..
IMHO, first thing, I would do is to reduce the duration for which new certs are issued to users, computers to three months.....
You could backup CA then restore CA.....
The concern, issue deals with templates, etc.
Before the one renews today, look at changing the Cert template for computer certs to a shorter window i.e. three months instead of the current year.
backup CA and restart the CA data onto the new CA is an option though checking whether it has a range of version to version..
IMHO, first thing, I would do is to reduce the duration for which new certs are issued to users, computers to three months.....
ASKER
You could backup CA then restore CA.....Though if I do this, I had thought that the Server name needed to be the same as the old CA? or was it the fact that it was on the DC, that I could not backup/Restore?
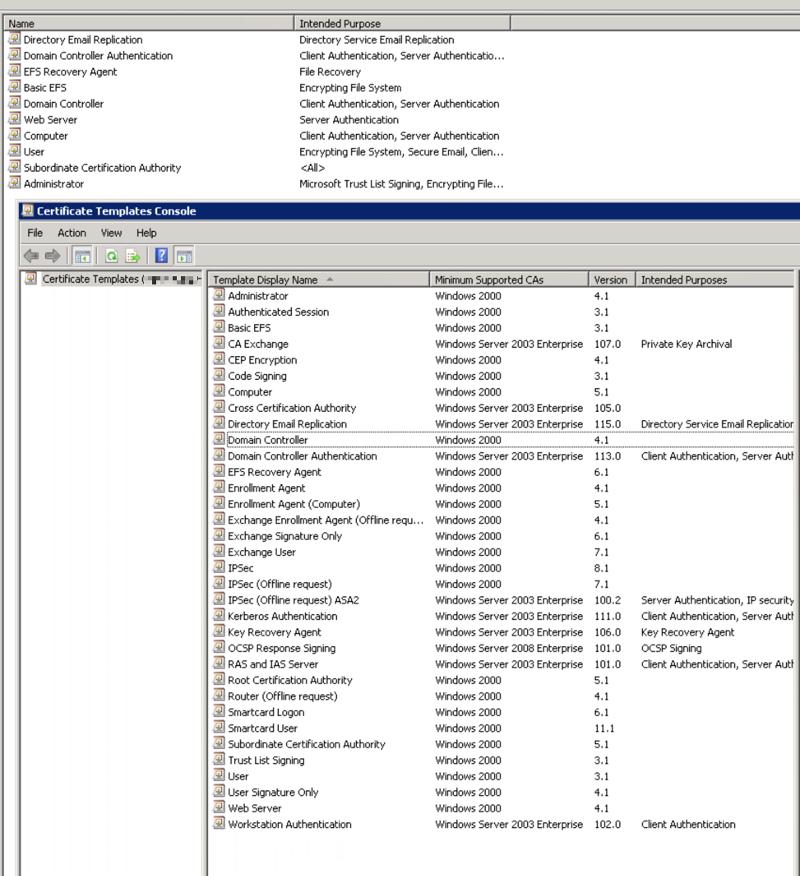
The concern, issue deals with templates, etc.Here are the Templates installed on the CA, I don't think I have ever modified any of them. When I look at the properties of the template in the Console (where it lists all of them) I cannot Edit the Validity Period on the "Computer" Template. I can on some others, but many are greyed out.
The issue with CA on DC, the CA has to be removed before a DC can be demoted/replaced...
See if the following helps on the term of duration
https://social.technet.microsoft.com/wiki/contents/articles/1102.how-to-changeextend-the-expiration-date-of-certificates-that-are-issued-by-a-windows-server-2008-or-a-windows-server-2003-certificate-authority.aspx
let me check on the other....
See if the following helps on the term of duration
https://social.technet.microsoft.com/wiki/contents/articles/1102.how-to-changeextend-the-expiration-date-of-certificates-that-are-issued-by-a-windows-server-2008-or-a-windows-server-2003-certificate-authority.aspx
let me check on the other....
ASKER
This is kind of exactly what I was thinking...
Step-By-Step: Migrating The Active Directory Certificate Service From Windows Server 2008 R2 to 2019
I don't see anything in there about the Machine names being different. They went from a WS2018 to WS2019 Server name.
I should be able to try this out.
Thoughts?
Step-By-Step: Migrating The Active Directory Certificate Service From Windows Server 2008 R2 to 2019
I don't see anything in there about the Machine names being different. They went from a WS2018 to WS2019 Server name.
I should be able to try this out.
Thoughts?
The issue with CA on DC, the CA has to be removed before a DC can be demoted/replaced...
See if the following helps on the term of duration
https://social.technet.microsoft.com/wiki/contents/articles/1102.how-to-changeextend-the-expiration-date-of-certificates-that-are-issued-by-a-windows-server-2008-or-a-windows-server-2003-certificate-authority.aspx
let me check on the other..
Certificates are not validated per se on each access. AS long as your OLD CA's Cert is listed as trusted. and if there is a CRL that is published and is accessible with the certs not revoked, the internal systems will issued certs as valid.
at this point you are trying to buy yourself time.
if you revoke a cert, the client ight be triggered to renew and if you have a different set of available published CAs it will request a cert from it versus from the old..
If you could test whether revoking a cert on a test system will force it to renew/get a new cert ...
See if the following helps on the term of duration
https://social.technet.microsoft.com/wiki/contents/articles/1102.how-to-changeextend-the-expiration-date-of-certificates-that-are-issued-by-a-windows-server-2008-or-a-windows-server-2003-certificate-authority.aspx
let me check on the other..
Certificates are not validated per se on each access. AS long as your OLD CA's Cert is listed as trusted. and if there is a CRL that is published and is accessible with the certs not revoked, the internal systems will issued certs as valid.
at this point you are trying to buy yourself time.
if you revoke a cert, the client ight be triggered to renew and if you have a different set of available published CAs it will request a cert from it versus from the old..
If you could test whether revoking a cert on a test system will force it to renew/get a new cert ...
they can have different names, otherwise they can not be running and online at the same time.
ASKER
they can have different names, otherwise they can not be running and online at the same time.
Looks like the Host name can be different, but the FriendlyName of the CA needs to be the same. My Old CA and Hostname are the same. It's not the right CA Friendly Name.
Thank you for stepping in here... Current CA is working, though I installed it back in 2006 to Support SCEP for Cisco VPN, which is no longer used.
Though Since I have installed the CA, the Domain PCs, Servers, DCs and some users have been issued Certificates from the 2008R2 CA. I'm not Specifically using them for anything. The CA was installed on an Old DC and we have not demoted the DC it because of the CA. I'm fine with a Completely new 2019 Server with a new CA. The old CA and old CA Host name are the same and I would love to change them Both.
I was thinking of:
- Setup a new 2019, set it as the default new Enterprise CA,
- Add Old CA's public cert to the new Enterprise CA Trusted List of CAs.
- Configure the new Enterprise CA with CRL,
- Reconfigure GPO to submit Requests to the new Enterprise CA.
- Renew certs against new Enterprise CA
- Wait for old Certs to Expire/Force Machines/Users to renew.
- Remove old 2008R2 CA Server
You already have the second item, the existing CA's cert is already trusted inside so not sure why you need to add it.
You do not need to add the OLD CA's you need to add the NEW CA;s Cert into the PKI system as another trusted CA.
Then you would configure the NEW CA as the destination CA from which clients obtain certs.
If you can test with one system following the NEW CA's Enrollment GPO is setup. On the old CA revoke the computer certificate to see whether once revoked the computer via the enrollment GPO will attempt to renew/obtain a new Certificate from the new CA.
The friendly name can be anything.
Possibly not place the CA on a DC.
If you do use an offline CA and setup a CRL, make sure to publish the CRL on a system that remains active, in the newer systems, you can use DFS-replication to have a hot copy of the CRL on multiple systems and served through IIS on each system.
This way while the ROOT CA is offline the issuing CA's can issue certs and have their OWN CRL published ot the common location....
You do not need to add the OLD CA's you need to add the NEW CA;s Cert into the PKI system as another trusted CA.
Then you would configure the NEW CA as the destination CA from which clients obtain certs.
If you can test with one system following the NEW CA's Enrollment GPO is setup. On the old CA revoke the computer certificate to see whether once revoked the computer via the enrollment GPO will attempt to renew/obtain a new Certificate from the new CA.
The friendly name can be anything.
Possibly not place the CA on a DC.
If you do use an offline CA and setup a CRL, make sure to publish the CRL on a system that remains active, in the newer systems, you can use DFS-replication to have a hot copy of the CRL on multiple systems and served through IIS on each system.
This way while the ROOT CA is offline the issuing CA's can issue certs and have their OWN CRL published ot the common location....
No comment has been added to this question in more than 21 days, so it is now classified as abandoned.
I have recommended this question be closed as follows:
Split:
-- 'Scott Silva' (https:#a43045671)
-- 'arnold' (https:#a43045754)
If you feel this question should be closed differently, post an objection and the moderators will review all objections and close it as they feel fit. If no one objects, this question will be closed automatically the way described above.
seth2740
Experts-Exchange Cleanup Volunteer
I have recommended this question be closed as follows:
Split:
-- 'Scott Silva' (https:#a43045671)
-- 'arnold' (https:#a43045754)
If you feel this question should be closed differently, post an objection and the moderators will review all objections and close it as they feel fit. If no one objects, this question will be closed automatically the way described above.
seth2740
Experts-Exchange Cleanup Volunteer
ASKER
That really seems wrong (-;