Remove Search Active Directory feature
I want to remove/grey out the "Search Active Directory" feature when you browse the network in my AD domain.
OR
I want to secure my active directory tree from regular domain users to NOT allow them to add any user to my AD groups using the "Search Active Directory" feature.
OR
I want to secure my active directory tree from regular domain users to NOT allow them to add any user to my AD groups using the "Search Active Directory" feature.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
They are NOT part of the "Account Operators" group.Then they cannot create or edit anything in AD. They can only browse AD. This is the expected behavior. So you shouldn't be concerned at all.
Before I do the group policy is there anything else I can try or check??I am not aware of anything else. If you want to prevent users from browsing the tree, just configure the policy.
ASKER
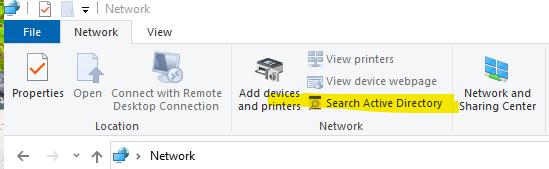
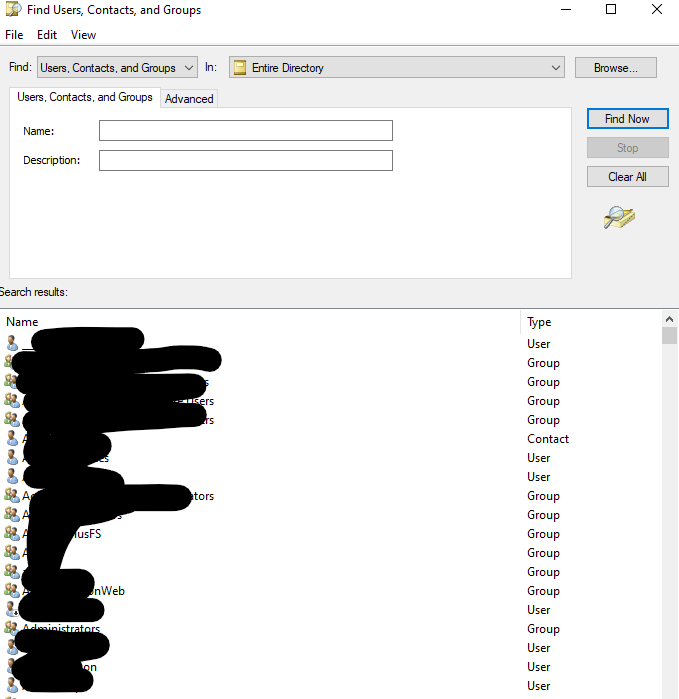
Well they could once the clicked on the network and then click the "Search Active Directory" they then clicked the "Find Now" button this would populate all the AD users and groups. Then they just doubled clicked one of the groups and got the existing users in the group and were able to add or remove users. The only one I checked they couldn't add or removed and the buttons were grayed out were for example the "Domain Admins" group.
What users are we talking about? Users with some privilidges? Local admins? If you are regular user, you have only read permissions so you can only browse the tree.
ASKER
These are regular users or Domain User with no privileges and they can browse and add or remove users to AD groups. I have tried the policy and that has worked.
Great! So the issue resolved?
ASKER
With the policy yes, but wanted to see where I could limit a regular domain user from doing these changes with AD permissions.
Open one of these groups in AD and go to the Security tab. What permissions do Authenticated Users or Domain Users have? They should have only Read, Send To and Read phone and mail options.
ASKER
Authenticated Users have Allow: Read, Send to, Read Exchange Information, Read Exchange Personal Information, Read phone and mail options, and Special permissions (grey-out).
Can you post screenshots? If I click on Search Active Directory, this is what I get:
User - I can see only the General, Address and Business tabs and I cannot change anything
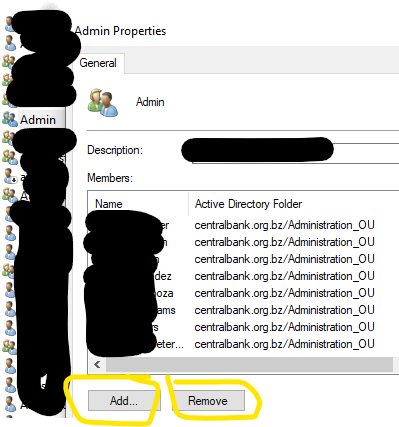
Group - I can see just the General tab. The "Add" and "Remove" buttons are grayed-out.
User - I can see only the General, Address and Business tabs and I cannot change anything
Group - I can see just the General tab. The "Add" and "Remove" buttons are grayed-out.
?
ASKER
Posted the screenshots.
I cannot see any of them.
Thanks. I'll look at it later today.
Right-click on the domain.com in AD -> Properties -> Managed By tab
Right-click on one of your groups in AD -> Properties -> Managed By tab
Is there a user or a group specified? Is the "Manager can update membership list" option ticked?
Also, it might be a nested group issue. Still in AD, find the Domain Admins group, Account Operators group, Administrators group and check members of these groups. Can you see anything related to users in the domain?
Btw. Are we talking about local or domain groups? Because if the user is a member of a local admin group, he can add domain user to local groups.
Right-click on one of your groups in AD -> Properties -> Managed By tab
Is there a user or a group specified? Is the "Manager can update membership list" option ticked?
Also, it might be a nested group issue. Still in AD, find the Domain Admins group, Account Operators group, Administrators group and check members of these groups. Can you see anything related to users in the domain?
Btw. Are we talking about local or domain groups? Because if the user is a member of a local admin group, he can add domain user to local groups.
ASKER
It's weird. Something isn't as should be.
Btw It's not a solution, it's a workaround and it doesn't change the fact that users have permissions to change the membership.
Btw It's not a solution, it's a workaround and it doesn't change the fact that users have permissions to change the membership.
ASKER
Yes, you are correct a workaround, which I have applied for now. Not sure where else to look.
I am running out of ideas now...
You can check if all users or just a few users are able to change the membership... Also if they can change the membership of all groups or just a few groups.
You can check if all users or just a few users are able to change the membership... Also if they can change the membership of all groups or just a few groups.
ASKER
Well like I said before I saw one regular user change one of the Groups. With my regular user I was also able to add or remove to the same group like the user I saw and other groups. The one I tried and couldn't add or remove was to the Domain Admins or Enterprise Admins Groups.
I was able to simulate the same results as you mentioned (a regular user can change membership through Search Active Directory but cannot change members of Domain Admins, Administrator, and groups like these) only if the user was a member of Account Operators.
I would start with that. I am pretty convinced now that all your users (I don't know how) are members of Account Operators.
I would start with that. I am pretty convinced now that all your users (I don't know how) are members of Account Operators.
ASKER
I only have 5 users that are part of the Account Operators group and they are administrators. There are no regular users like my account i used to test.
ao.png
ao.png
Is it possible that somebody delegated control over the OU with groups to certain users? Can you open the properties of one of these groups and check again the whole list of users/groups that have the permissions?
http://woshub.com/delegate-control-active-directory/
Still in AD, open the properties the group you were able to change the membership -> Security tab -> Advanced -> Effective Access tab -> select the test user that was able to change the membership and see all the permissions. Can you post screenshots?
Netwrix Auditor (trial) might help you here.
https://www.netwrix.com/active_directory_auditing.html
http://woshub.com/delegate-control-active-directory/
Still in AD, open the properties the group you were able to change the membership -> Security tab -> Advanced -> Effective Access tab -> select the test user that was able to change the membership and see all the permissions. Can you post screenshots?
Netwrix Auditor (trial) might help you here.
https://www.netwrix.com/active_directory_auditing.html
ASKER
The domain user is not in the list when you click properties and security tab. He is a member of the group and when i did the effective access he has full control. See screenshot.
effectiveaccess.png
effectiveaccess.png
If this is a domain user, this is wrong. He shouldn't have Full Access. That's why he can change the membership.
ASKER
Well I don't know where to check all he has is membership to the group.
Hard to say.
Since you have multiple users that can change the membership, it has to be a group where these permissions are set. You said that the user is a member of Domain Users.
Domain Users group is a member of which group? What permissions are set for this group? Is this group a member of another group? And so on...
Since you have multiple users that can change the membership, it has to be a group where these permissions are set. You said that the user is a member of Domain Users.
Domain Users group is a member of which group? What permissions are set for this group? Is this group a member of another group? And so on...
ASKER
Domain Users group is a member of 2 groups one is a SharePoint group and the other the "Users" group which a builtin group.
The OWS... group is NOT a member of any group.
The builtin Users group is NOT a member of any group.
gpm.png
The OWS... group is NOT a member of any group.
The builtin Users group is NOT a member of any group.
gpm.png

ASKER
Before I do the group policy is there anything else I can try or check??