Backup Exec Catalogs tapes but shows no Data Sets to restore.
Our Windows Server 2012 STD R2 was hacked and randomware installed. We lost everything. Luckily we have it all backup to tape.
The problem is we were running Backup Exec 2014. I have now reinstalled the server with tried both the Trial versions of BE 2014.1 and and BE 20.6 as we lost our software and license info on that server. The tape inventory and catalog ran successfully. It shows the tapes with the data on them and the servers that the data was backed up from.The catalog how ever show not data sets to restore.
We have tried a few different evening backup tapes and they all do the same. I have tried a number of different solutions I found on the net but nothing seems to work.
See images below.
How can we restore the data from the tapes?
Is there another Backup program we can try that will read the tapes.
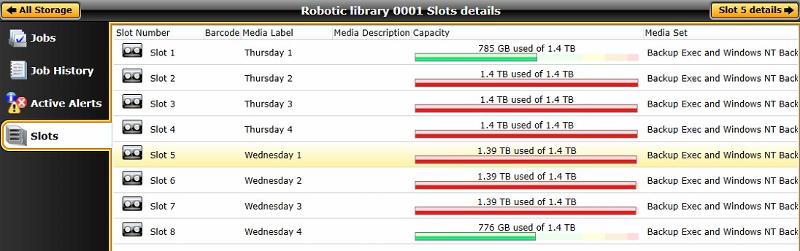
The problem is we were running Backup Exec 2014. I have now reinstalled the server with tried both the Trial versions of BE 2014.1 and and BE 20.6 as we lost our software and license info on that server. The tape inventory and catalog ran successfully. It shows the tapes with the data on them and the servers that the data was backed up from.The catalog how ever show not data sets to restore.
We have tried a few different evening backup tapes and they all do the same. I have tried a number of different solutions I found on the net but nothing seems to work.
See images below.
How can we restore the data from the tapes?
Is there another Backup program we can try that will read the tapes.


ASKER
Hi Arnold
Thanks. If there was an encryption key then that is lost from the ransomware attack.
Any way around that?
Thanks. If there was an encryption key then that is lost from the ransomware attack.
Any way around that?
No. It had to have been exported before and stored away.
Depending on whether the tape library was triggered to reinitialize tapes.
Depending on whether the tape library was triggered to reinitialize tapes.
ASKER
Ok so we seem to have made some progress and have a catalog running on 8 backup tapes which hold +/-12TB.
The catalog has been running for 14 hours and currently shows a byte count 4.56MB 0.00MB/per minute.
How long should a catalog like this usually take to run?
The catalog has been running for 14 hours and currently shows a byte count 4.56MB 0.00MB/per minute.
How long should a catalog like this usually take to run?
Which tape library usin use? Sas/FC connectors, multiple drives?
ASKER
HP Storageworks 1/8 G2 Tape Autoloader with one LTO drive. SAS connection to server.
Catalog ran for 22 Hours. I could see it reading the data when I looked at the active job log, but once completed still shows no data sets to restore from.
Catalog ran for 22 Hours. I could see it reading the data when I looked at the active job log, but once completed still shows no data sets to restore from.
Do you have offline tapes from before the attack?
Have you been able to determine the source of the attack, I.e. Came in as an attachment, or an intrusion ?
Have you been able to determine the source of the attack, I.e. Came in as an attachment, or an intrusion ?
ASKER
I do have other tapes from before the attack but had the same issue with those.
The attack was an Intrusion. I caught the guy in process as I was kicked off the server when he got on and he kept kicking me off every time was able to kick him off. Eventually I got a window where I could change the IP address of the server and he could not get back on, but the ransomware was already spreading fast by that stage and nothing I could do.
The attack was an Intrusion. I caught the guy in process as I was kicked off the server when he got on and he kept kicking me off every time was able to kick him off. Eventually I got a window where I could change the IP address of the server and he could not get back on, but the ransomware was already spreading fast by that stage and nothing I could do.
Do you know whether the setting for the writing to the tape include data protection, encryption? If that is a possibility, than without the key all the tapes are of little use to you.
ASKER
That I am not sure of. I don;t think so unless it is a standard part of the BE2014 installation.
I did read that if your data is encrypted and you haven't loaded a file with the key they you will be prompted for the passphrase, which I have not.
I did read that if your data is encrypted and you haven't loaded a file with the key they you will be prompted for the passphrase, which I have not.
Do you know whether it went through all the tapes, or is it still on the first tape?
What was the backup scheme, full monthly, differential/incremental daily with different systems scheduled at different times to distribute bandwidth over a week or .....
What was the backup scheme, full monthly, differential/incremental daily with different systems scheduled at different times to distribute bandwidth over a week or .....
ASKER
It is a full backup that takes all 4 tapes.
if a full backup unless and until it catalogs them all it might not be ready to present a list.
unfamiliar when a windows host whether you can look at raw data ...the issue with the system, it is unclear if and when the backup ran.
unfamiliar when a windows host whether you can look at raw data ...the issue with the system, it is unclear if and when the backup ran.
ASKER
Thanks for all the advice Arnold. We have purchased full licensing from Veritas and will seek Tech Support from them.
Should they be able to get the backups restored, which I would expect them to do so as they must have come across this issue before in many years of selling and supporting this product, then I will post the solution here if I am able to.
Should they be able to get the backups restored, which I would expect them to do so as they must have come across this issue before in many years of selling and supporting this product, then I will post the solution here if I am able to.
Good luck.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for all the tips and feedback.
https://www.veritas.com/support/en_US/article.100014505