Safeguarding your Emails in an Email Server
How to protect your email on a mail server from the mail administrator who may be snooping in and reading your emails.
Is there like a vpn encryption service for the Microsoft Exchange Mail Server and the Outlook Client?
Is there like a vpn encryption service for the Microsoft Exchange Mail Server and the Outlook Client?
ASKER
I added encryption to my internal emails for those who have a digital signature, will this help? Will this allow only the recipient to read the emails?
Define "I added encryption to my internal emails for those who have a digital signature"..... using what?
ASKER
I went in outlook and entered the "Trust Center Settings" and I enabled encryption in the "email security section".
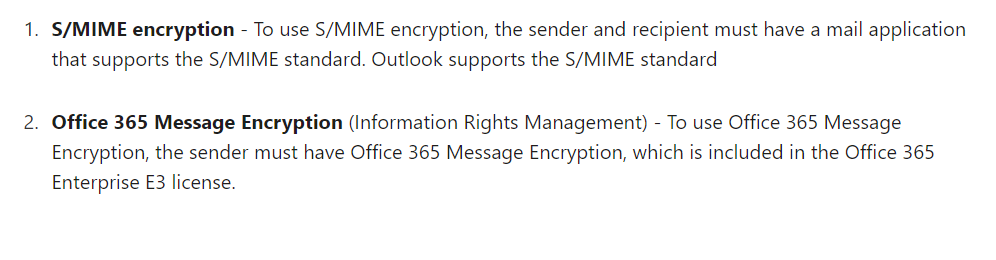
ok, so you are likely using O365 IRM - https://support.office.com/en-us/article/encrypt-email-messages-373339cb-bf1a-4509-b296-802a39d801dc
Does that sound right? do you know if your mailbox is in O365 at the backend ?
Does that sound right? do you know if your mailbox is in O365 at the backend ?
only those messages sent and received with encryption enabled.
The roles a person has on the exchange server can be limited.
an untrusted person should not be given keys to access all resources, shoukd not be an admin.
Do the encrypted messages sent to you prompt for a pass phrase before you can view the message, or are decrypted ...
Is the certificate purchased by you, or created by the exchange server, fo sin CA?
The roles a person has on the exchange server can be limited.
an untrusted person should not be given keys to access all resources, shoukd not be an admin.
Do the encrypted messages sent to you prompt for a pass phrase before you can view the message, or are decrypted ...
Is the certificate purchased by you, or created by the exchange server, fo sin CA?
ASKER
No...there is no pass phrase provided prior to being able to open up the email......if the people you are sending it to has a digital signature and key which is provided to them because they are apart of the directory, they have the ability to open it up.
The administrator on your server will still be able to view these messages - either by adding him/herself to have full access over your mailbox, or using Ediscovery and selecting to search non-indexed items.
https://docs.microsoft.com/en-us/exchange/policy-and-compliance/ediscovery/ediscovery?view=exchserver-2019
Again.... as i have said, and arnold has said.... if the admin is not trust-worthy - there are no good solutions for you here.... unless you have some sort of control over this persons access - to ensure they are not a "god" level admin - then what you are after is difficult, if not impossible.
https://docs.microsoft.com/en-us/exchange/policy-and-compliance/ediscovery/ediscovery?view=exchserver-2019
Again.... as i have said, and arnold has said.... if the admin is not trust-worthy - there are no good solutions for you here.... unless you have some sort of control over this persons access - to ensure they are not a "god" level admin - then what you are after is difficult, if not impossible.
One is, the communication must have been encrypted
The copy in the sent if set to keep copy, would likely not be encrypted .
If you have an admin that goes through others emails without cause, you should address that directly versus trying to work around it.
If you gave multiple admin's one that deals as an AD sevurity who then manages which rights the mail server admin has..
Consider it this an office building administrator who has access to all office keys, to then try to curb ...
Note a persistent snooper who has keys can circumvent what you are trying to do.
All incoming, outgoing messages can be forwarded/ by the admin. Without impacting the sender or recipient.
The copy in the sent if set to keep copy, would likely not be encrypted .
If you have an admin that goes through others emails without cause, you should address that directly versus trying to work around it.
If you gave multiple admin's one that deals as an AD sevurity who then manages which rights the mail server admin has..
Consider it this an office building administrator who has access to all office keys, to then try to curb ...
Note a persistent snooper who has keys can circumvent what you are trying to do.
All incoming, outgoing messages can be forwarded/ by the admin. Without impacting the sender or recipient.
ASKER
There is no work around? I mean VPN safeguards your internet activity from even your ISP. We can't safeguard emails?
Do you manage AD access tights, group membership?
You can limit what the mail administrator has access to.
You can setup auditing on your systems that generate notifications as well as Jung splunk or other tools that collect these logs and make them searchable.
If you are subject to regulatory compliance ....
Do you suspect that that is what is occurring or know for certain?
You can limit what the mail administrator has access to.
You can setup auditing on your systems that generate notifications as well as Jung splunk or other tools that collect these logs and make them searchable.
If you are subject to regulatory compliance ....
Do you suspect that that is what is occurring or know for certain?
In a business environment anything you do that uses company resources belongs to the company. as for using a vpn it doesn't hide the setup of the van tunnel and if they captured the data they can replay everything. They are the ultimate man in the middle.
ASKER
Just curious, what can they use to capture data packets in a van tunnel? They may be able to see when you enter and exit nodes of a vpn but if it is encrypted, how can they play it back?
I'm interested.
I'm interested.
IMHO, discussing a VPN in this context side tracks the issue.
Consider this, you have a vault where all documents are stored. A person charged with receiving the documents and placing them in bibs for access by company officials is suspected of perusing through the documents.
No matter what sevurity measures, mechanism you implement for transferring documents in I.e. armored car, lick and key courier, etc. when it gets to the vault the person will have to receive it. On the other side, each user has to go through additional sevurity doors, scanners to get to the vault to access the document.
Point being a person with access, such as admin, if they are untrustworthy, they should not be in a trusted position.
Consider this, you have a vault where all documents are stored. A person charged with receiving the documents and placing them in bibs for access by company officials is suspected of perusing through the documents.
No matter what sevurity measures, mechanism you implement for transferring documents in I.e. armored car, lick and key courier, etc. when it gets to the vault the person will have to receive it. On the other side, each user has to go through additional sevurity doors, scanners to get to the vault to access the document.
Point being a person with access, such as admin, if they are untrustworthy, they should not be in a trusted position.
VPN IS NOT APPLICABLE IN A SITUATION SUCH AS YOUR QUESTION RAISES.
it is a diversion.
it is a diversion.
only if you and the recipient have outside of the email channel. or if you write your messages and then encrypt them and then attach the encrypted blob will your email be secure. Even if he admin could get access to your computers certificate store anyone outside of you two will only know that you sent or received an email from the other party and the size was the size of the attachment There is a lot of information that can be surmised just using traffic analysis.
ASKER
How is the email attached with an encrypted blob?
The blob is encrypted data that only the recipient can decrypt, see. In such a situation even you will not be able to view the data if the original us not saved.
What is your role?
Trying to make sure I am not providing info to a user who is trying to circumvent company policy under a pretext.
What is your role?
Trying to make sure I am not providing info to a user who is trying to circumvent company policy under a pretext.
ASKER
I am a user. I am not circumventing company policy however, I wish to safeguard my email correspondence. Do you have a link providing information regarding this, blob? Is this sort of like Base64 hash?
mate - your talking about two different things in this thread now.
Encryption of the email content and encryption to the channel while transmitting the email. They are two totally different things.
and with this comment, you draw a very long bow
There are plenty of things that can be done to "safeguard" email.... but you are trying to specifically protect email content from a person who has god access over the email system.... the people that implement these "safeguards"....
Encryption of the email content and encryption to the channel while transmitting the email. They are two totally different things.
and with this comment, you draw a very long bow
"There is no work around? I mean VPN safeguards your internet activity from even your ISP. We can't safeguard emails? "
There are plenty of things that can be done to "safeguard" email.... but you are trying to specifically protect email content from a person who has god access over the email system.... the people that implement these "safeguards"....
Look at desktop pgp.
It is un encryption. Using individual and unique keys.
Base64 is an encoding not an encryption.
Are you familiar with any spy novel, movie.
safeguard your correspondence from whom?
It is un encryption. Using individual and unique keys.
Base64 is an encoding not an encryption.
Are you familiar with any spy novel, movie.
safeguard your correspondence from whom?
ASKER
Desktop PGP - interesting......encrypts the whole computer.
What spy novel movies you are referring to?
What spy novel movies you are referring to?
This question seems a bit off track.
1) You're original question is how to protect email from snooping administrators.
You can't. Best policy is to compensate/pay an administrator well, so there's no reason for them to be snooping to steal data.
2) Regards encryption. For this to work requires both sender + recipient to share keys, which is complex.
If you're really interested in end-to-end message encryption, close this question + open a 2nd question discussing how to encrypt email.
Hint: For working encryption, you'll use something like S/MIME.
1) You're original question is how to protect email from snooping administrators.
You can't. Best policy is to compensate/pay an administrator well, so there's no reason for them to be snooping to steal data.
2) Regards encryption. For this to work requires both sender + recipient to share keys, which is complex.
If you're really interested in end-to-end message encryption, close this question + open a 2nd question discussing how to encrypt email.
Hint: For working encryption, you'll use something like S/MIME.
The point is PGP, GNUPG, and similar will encrypt a document using the recipients Public key that you MUST have.
The resulting encrypted document is then attached to an email you said recipient.
historical record on the Inigma machine. to decode you have to have the recipients key.
The point is in simple straight forward you take the latin character set You mask which letter is which, one to one mapping.
Public
a -> G
b -> Z
.
.
.
your key to decrypt the message is
G ->a
Z->b
The other side has a similar thing.
The digital public key is much more complex to get the private key from the public one.
but the mechanism is the same.
you take the message apply the cipher which scrambles the message into gibberish that only the person with the proper key can reverse.
The resulting encrypted document is then attached to an email you said recipient.
historical record on the Inigma machine. to decode you have to have the recipients key.
The point is in simple straight forward you take the latin character set You mask which letter is which, one to one mapping.
Public
a -> G
b -> Z
.
.
.
your key to decrypt the message is
G ->a
Z->b
The other side has a similar thing.
The digital public key is much more complex to get the private key from the public one.
but the mechanism is the same.
you take the message apply the cipher which scrambles the message into gibberish that only the person with the proper key can reverse.
ASKER
I am convinced now that you can't protect yourself from the inside. Understood.
only GPG/PGP or S/mime will actually prevent the text from being decoded, if and only if the keys are handled by the client software rather than on the server. the email should not be readable in the webmail in that case.
this does not encode all the mail headers not obfuscate the smtp transaction itself so basic information such as sender and recipient will still be available.
also note that all of the above can be brute forced or broken in multiple ways if folks have enough time and knowledge. but this is likely way over the head of an exchange administrator.
other than that, there is no way an admin can be forbidden to access the email. any vendor pretending that is either a scammer or plain incompetent. your admins need admin privileges in order to do their jobs.
basically email is unsafe, but you can build some security over email. and do not expect any alternative to be any better. encryption/decryption should happen at your level. once that is the case, the transfer media does not matter much.
this does not encode all the mail headers not obfuscate the smtp transaction itself so basic information such as sender and recipient will still be available.
also note that all of the above can be brute forced or broken in multiple ways if folks have enough time and knowledge. but this is likely way over the head of an exchange administrator.
other than that, there is no way an admin can be forbidden to access the email. any vendor pretending that is either a scammer or plain incompetent. your admins need admin privileges in order to do their jobs.
basically email is unsafe, but you can build some security over email. and do not expect any alternative to be any better. encryption/decryption should happen at your level. once that is the case, the transfer media does not matter much.
I've been thinking about your question.
Reading between the lines (guessing at the real problem).
You likely have multiple admins with access to all mail files.
In other words, you can be trusted, then some/many other admins can't be trusted.
If I were in this situation, I'd likely use Dovecot (not Exchange) for more control over actual message storage, then use a format like encrypted, compressed, mdbox to make reading messages for anyone (except you) very difficult.
Maybe there's some way to do this using Exchange.
With Dovecot, this type of setup is trivial. The only challenge being you'll have to safeguard the encrypt/decrypt key + if this key is lost no one will ever be able to access/decrypt any mail again.
Generally a copy of the key is kept by at least 2x people, along with 1x+ copies archived offsite.
Reading between the lines (guessing at the real problem).
You likely have multiple admins with access to all mail files.
In other words, you can be trusted, then some/many other admins can't be trusted.
If I were in this situation, I'd likely use Dovecot (not Exchange) for more control over actual message storage, then use a format like encrypted, compressed, mdbox to make reading messages for anyone (except you) very difficult.
Maybe there's some way to do this using Exchange.
With Dovecot, this type of setup is trivial. The only challenge being you'll have to safeguard the encrypt/decrypt key + if this key is lost no one will ever be able to access/decrypt any mail again.
Generally a copy of the key is kept by at least 2x people, along with 1x+ copies archived offsite.
ASKER
Thank you David. Dovecot seems to be an interesting solution.
If not mistaken, dovecot is just an IMAP server you would need something else to such as an mta postfix...
no go.
the email will reach dovecot unencrypted if it was sent unencrypted so the admin will obviously be able to read them.
the mailcrypt plugin is only meaningful to encrypt data at rest assuming dovecot runs in a different location from the storage. the keys are known to both dovecot and the admin. there is no way past that.
we make difficult things possible. but impossible is impossible, and such approaches will only result in a scam or loss of your time. on the other hand, pgp and s/mime do quite a decent encryption job. use them.
the email will reach dovecot unencrypted if it was sent unencrypted so the admin will obviously be able to read them.
the mailcrypt plugin is only meaningful to encrypt data at rest assuming dovecot runs in a different location from the storage. the keys are known to both dovecot and the admin. there is no way past that.
we make difficult things possible. but impossible is impossible, and such approaches will only result in a scam or loss of your time. on the other hand, pgp and s/mime do quite a decent encryption job. use them.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
the goal is to prevent the exchange admin from reading the email.
encrypting the email is both an obvious solution and a pain to implement in many cases.
a VPN has no relation with the topic unless someone can demonstrate how to use a VPN to prevent a mail admin from snooping the email that transit on his own server.
note that apps such as deltachat and thunderbird support autocrypt which helps a lot with the setup.
encrypting the email is both an obvious solution and a pain to implement in many cases.
a VPN has no relation with the topic unless someone can demonstrate how to use a VPN to prevent a mail admin from snooping the email that transit on his own server.
note that apps such as deltachat and thunderbird support autocrypt which helps a lot with the setup.
Much depends on what the security settings for the exchange "admin" are.
What functionality do you want the person to have? The choices you make, will limit what the person can do.
I.e. you can delegate certain rights, but that means when there is an issue, these limits could impact what this person can do, at which time, the issue has to be escalated to the person with the requisite rights.
Look at which rights you assign to this admin.
1) does this admin have rights to add users? or is the admin limited to exchange server management only, no user related access.
To achieve what you want, it sounds you want to limit the exchange admin to only exchange server functions
Noting, that if delegated, the admin who would usually manage the storge space, also includes an option of exporting a specific mailbox into a PST file.
2) as long as the exchange admin has rights to edit properties of user mailboxes, this right makes it possible for the admin to grant their account read send as, rights to any mailbox.
3) auditing of exchange might be a way with a proactive versus retrospective setup that SNMP traps versus processed logs is one way to trigger when an admin account accesses a user mailbox ....
Look at the exchange permissions and see which roles your current exchange admin at issue has and whether you should pare it down to curb their access to achieve what you are after while understanding the implications.
https://docs.microsoft.com/en-us/Exchange/permissions/permissions?view=exchserver-2019#:~:text=In%20Exchange%20Server%2C%20the%20permissions%20that%20you%20grant,a%20set%20of%20mailboxes%2C%20contacts%2C%20and%20distribution%20groups.
What functionality do you want the person to have? The choices you make, will limit what the person can do.
I.e. you can delegate certain rights, but that means when there is an issue, these limits could impact what this person can do, at which time, the issue has to be escalated to the person with the requisite rights.
Look at which rights you assign to this admin.
1) does this admin have rights to add users? or is the admin limited to exchange server management only, no user related access.
To achieve what you want, it sounds you want to limit the exchange admin to only exchange server functions
Noting, that if delegated, the admin who would usually manage the storge space, also includes an option of exporting a specific mailbox into a PST file.
2) as long as the exchange admin has rights to edit properties of user mailboxes, this right makes it possible for the admin to grant their account read send as, rights to any mailbox.
3) auditing of exchange might be a way with a proactive versus retrospective setup that SNMP traps versus processed logs is one way to trigger when an admin account accesses a user mailbox ....
Look at the exchange permissions and see which roles your current exchange admin at issue has and whether you should pare it down to curb their access to achieve what you are after while understanding the implications.
https://docs.microsoft.com/en-us/Exchange/permissions/permissions?view=exchserver-2019#:~:text=In%20Exchange%20Server%2C%20the%20permissions%20that%20you%20grant,a%20set%20of%20mailboxes%2C%20contacts%2C%20and%20distribution%20groups.
<< How to protect your email on a mail server from the mail administrator who may be snooping in >>
VPNs won't be even mildly helpful in this case.
no hard feeling but we cannot let folks be scammed with useless pseudo security layers when they clearly do not apply based on the question.
VPNs provide network-layer security. they produce zero additional security once you reached the connection endpoint (in this case the mail server).
additionally, some ISPs will just reject email that originate from outside their networks including the vpn terminations. so chances are throwing a vpn is entirely useless, and chances are it breaks an otherwise working setup.
btw, personnal vpns provide merely a very limited subset of vpn functionalities and as such should NOT be called vpn services. setting up a full blown VPN at home would merely expose your whole lan to the vpn provider for no reason.
VPNs won't be even mildly helpful in this case.
no hard feeling but we cannot let folks be scammed with useless pseudo security layers when they clearly do not apply based on the question.
VPNs provide network-layer security. they produce zero additional security once you reached the connection endpoint (in this case the mail server).
additionally, some ISPs will just reject email that originate from outside their networks including the vpn terminations. so chances are throwing a vpn is entirely useless, and chances are it breaks an otherwise working setup.
btw, personnal vpns provide merely a very limited subset of vpn functionalities and as such should NOT be called vpn services. setting up a full blown VPN at home would merely expose your whole lan to the vpn provider for no reason.
Have a read of this helpful article - to give some context of what your asking for - https://techcommunity.microsoft.com/t5/exchange-team-blog/protecting-against-rogue-administrators/ba-p/585155
If you have a mail administrator you cannot trust - then there is your problem right there.... trying to find a technical solution to a people issue is not going to work.