Sonicwall 500V loads Citrix Storefront but apps won't run
We purchased the 500v so our remote users could access our system apps remotely via web only access (not client install needed.) this works great. Loading external website are fine and internal work but are flaky. Most needed is our Citrix xenapp 7.6 applications (word, excel, etc.). Remote users click to open the Citrix bookmark menu which does what is expected and shows users available Citrix apps. When clicking on selected app (word, for example) the app spins as if it would open than does nothing. This does work if the virtual office is launched within the local network environment. Only the remote users have this issue.
ASKER
We are using a sonicwall Secure Mobile appliance 500V. It gets to the store front and displays all the apps. I need to know what route the apps take that they cannot open from that point.
thanks
Wayne
thanks
Wayne
Sonicwall don't recognize the connection attempt from external as done by netscaler-gateway.
From where the sonicwall shoud know to which server (i think you have more than one) the user must be connected?
The only way without netscaler i know, is VPN ... as already explained by Sam Jacobs.
With VPN there are some more firewall-ports...
80 & 443 to Storefront or Loadbalancer
DNS (because the used VDA is listed with the name)
1494 & 2598 TCP&UDP (works without UDP too, but this is more fast ... especially with VPN)
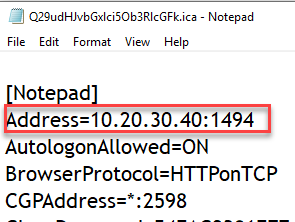
with your problem ... try to capture the launch.ica file.
Within this file you find the servername for the ICA/HDX connection.
From where the sonicwall shoud know to which server (i think you have more than one) the user must be connected?
The only way without netscaler i know, is VPN ... as already explained by Sam Jacobs.
With VPN there are some more firewall-ports...
80 & 443 to Storefront or Loadbalancer
DNS (because the used VDA is listed with the name)
1494 & 2598 TCP&UDP (works without UDP too, but this is more fast ... especially with VPN)
with your problem ... try to capture the launch.ica file.
Within this file you find the servername for the ICA/HDX connection.
@wlasner
Here is a simplified data flow:
When you click on an application, a dynamically-generated ICA file is sent to your PC with the name/IP of the VDA host to connect to.
Your browser will recognize the .ica extension, and send it to the ICA client (Workspace App/Receiver), which must already be installed,
The ICA client will attempt to contact the VDA specified in the ICA file, but will not be able to if any of the following are true:
- you don't have all the necessary ports open,
- it cannot resolve the VDA name/IP in the ICA file, or
- if for any reason it cannot connect to the VDA.
Here is a simplified data flow:
When you click on an application, a dynamically-generated ICA file is sent to your PC with the name/IP of the VDA host to connect to.
Your browser will recognize the .ica extension, and send it to the ICA client (Workspace App/Receiver), which must already be installed,
The ICA client will attempt to contact the VDA specified in the ICA file, but will not be able to if any of the following are true:
- you don't have all the necessary ports open,
- it cannot resolve the VDA name/IP in the ICA file, or
- if for any reason it cannot connect to the VDA.
ASKER
Thank you both. I checked and all ports appear to be set in the firewall. The end user is connected to the SMA500. At that point I believe all connections are internal. As mentioned, access to the storefront is not a problem. accessing the VDA is where it seems to get stuck. Host resolution for the VDA's is configured on SMA500V. I am close to giving up on this project. SW does not seem to have the resources to assist adequately.
Very frustrating.
Very frustrating.
Sorry that you got stuck with the SW. You can get a basic NetScaler VPX 200 for about $1K (last time I checked).
I don't know how many users you need to service, but it's a good practice to have 2 of everything, and load-balance them for HA purposes (in case one of them fails).
I don't know how many users you need to service, but it's a good practice to have 2 of everything, and load-balance them for HA purposes (in case one of them fails).
ASKER
500V, free download and only $600 per year for three years. We only have a bout 20 full time and another 20 part time remote users.
i'm sure netscaler would be less of a headache.
Thanks
Wayne
i'm sure netscaler would be less of a headache.
Thanks
Wayne
ASKER
Hold on - I just discovered the issue. in the 500V I had to force "Native Mode" for the Citrix Access type instead of the HTML5. I would rather user HTML5 as it allow to open in a new window. The native mode does not. Users will exit citrix and close out of the portal.
ASKER
Hi Sam, Citrix is telling me I need an SSL computer cert with private key for each VDA.
Maybe when going through the 500V, but not when going through the NetScaler.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
If you are going to use another method, you will need to:
- Establish a VPN from the user's machine to your local network
- Ensure ports 1494 and 2598 are open to ALL your VDAs
- Ensure that the user can get to all of the VDAs.
You *will* need to install the Workspace App (aka Receiver) client to access Citrix applications.