TECHNO.IT
asked on
Deploying a Server Farm or Data Center Firewall
I'm working on a solution as a vendor over deployment model for Palo Alto NGFW with following interest
- To control and inspect the traffic from between users and servers
- To protect DMZ web servers sourcing from internet.
I put together a fairly current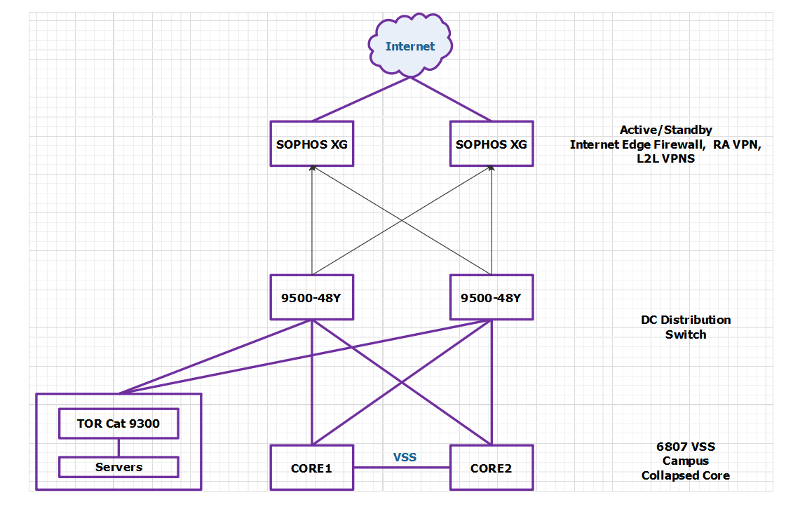 network design. At the moment we have two internet boundry firewall handling ingress/egress NAT, VPN connections
network design. At the moment we have two internet boundry firewall handling ingress/egress NAT, VPN connections
So I am looking for advise validated design and suggestions where to install the new firewall pair in the path as mentioned above.
- To control and inspect the traffic from between users and servers
- To protect DMZ web servers sourcing from internet.
I put together a fairly current
 network design. At the moment we have two internet boundry firewall handling ingress/egress NAT, VPN connections
network design. At the moment we have two internet boundry firewall handling ingress/egress NAT, VPN connectionsSo I am looking for advise validated design and suggestions where to install the new firewall pair in the path as mentioned above.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for the valuable suggestion. I would appreciate if you support the explanation with a simple diagram to just ensure I am understanding in context.
You have favorite free online network diagramming tool?
ASKER
I use Microsoft Paint for demo purposes :)
ASKER
Hi kevinhsieh
Any further help ?
Any further help ?
ASKER
I have multiple TOR access switches, just for sake of simplicity
We dont have seperate core switches in Server Farm, TOR are directly connected to campus core. VLANs and SVI terminated on Core.
We want to deploy seperate cores as well in DC.
We dont have seperate core switches in Server Farm, TOR are directly connected to campus core. VLANs and SVI terminated on Core.
We want to deploy seperate cores as well in DC.
Are your ToR switches in VSS or equivalent? The firewalls can be anywhere you can get L2 connectivity from the servers to the firewalls. No SVI on the switches, just L2. Use the FW as your gateway for your "DMZ" machines. FW then routes back to the rest of the network using same physical interfaces (router on a stick), or different interfaces.
Are you planning physical or virtual firewalls?
ASKER
Physical firewalls
Physically you want to connect the Palo Alto to a pair of switches where you have LACP from the Palo Alto to the switches. That allows you to fail a switch without failing over the firewall.
ASKER
So basically I would do these setup.
I can connect Internet Firewalls ( SOPHOS XG) and Palo Alto to the same data center core switches.
Servers will sit behind the PAN firewalls as a gateway and L3 interfaces on it
Enterprise core would have default route for south-north direction traffic to DC Core switches to access servers and internet. DC core switches will have default route to XG.
DC core switches would also learn DC routes via dyanmic routing protcol between DC Core and PAN Firewall
Please give suggestions if anything is wrong with above setup.
I can connect Internet Firewalls ( SOPHOS XG) and Palo Alto to the same data center core switches.
Servers will sit behind the PAN firewalls as a gateway and L3 interfaces on it
Enterprise core would have default route for south-north direction traffic to DC Core switches to access servers and internet. DC core switches will have default route to XG.
DC core switches would also learn DC routes via dyanmic routing protcol between DC Core and PAN Firewall
Please give suggestions if anything is wrong with above setup.
DC Core switches are not on the diagram. Other than that, I would say that it looks good to me so far.
ASKER
9500-48Y are the DC core switches shown in the diagram.
ASKER
Internet edge firewalls should to Enterprise Core or Data Center ? Any thoughts ?
Internet edge firewalls should be as close to the Internet as possible, and be connected to whatever hardware provides appropriate bandwidth and multi-chassis LACP connections. I certainly wouldn't want to burn a 10G switch port on a 1G interface, for example.
ASKER
I meant Inside interface for firewalls should connect to LAN core or DC Core/Distribution ?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Core would have default route to internet firewalls and DC routes will be learned through DC Core.

ASKER
- We are deploying a firewall in the data center to control access from the south to north.
- To implement DMZ DC for Web Servers.
I would appreciate if you can share a simple diagram for your deployment, it will be very helpful. Basically my objectives are mentioned above.