Cert Errors on All my Domain Controllers
Windows 2012 R2 Domain Controllers
I am getting cert errors on all my Domain Controllers
Event Id 6 13 64 etc
I have a Windows 2012 R2 server as my Cert Server.
On there all the certs have expired.
In the failed Request section all them listed
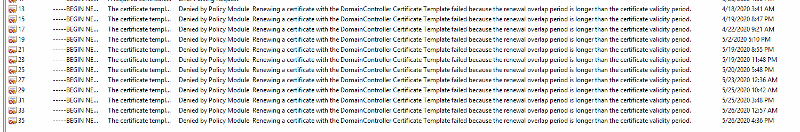
I can revoke them but not create any new ones very strange
Any ideas?
I am getting cert errors on all my Domain Controllers
Event Id 6 13 64 etc
I have a Windows 2012 R2 server as my Cert Server.
On there all the certs have expired.
In the failed Request section all them listed
I can revoke them but not create any new ones very strange
Any ideas?
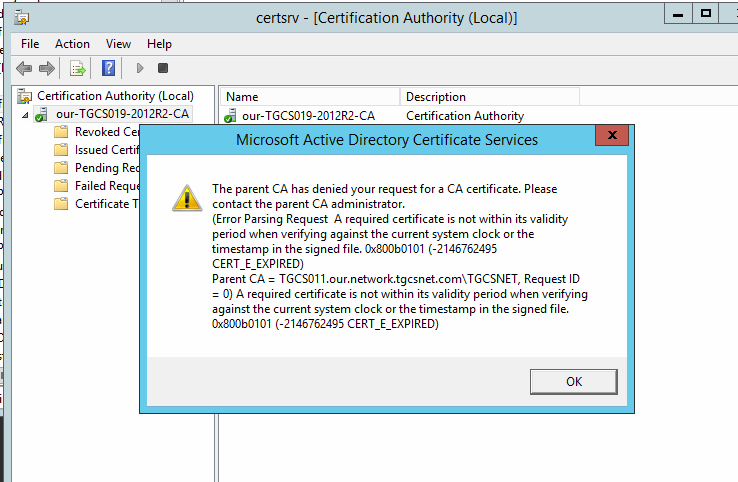
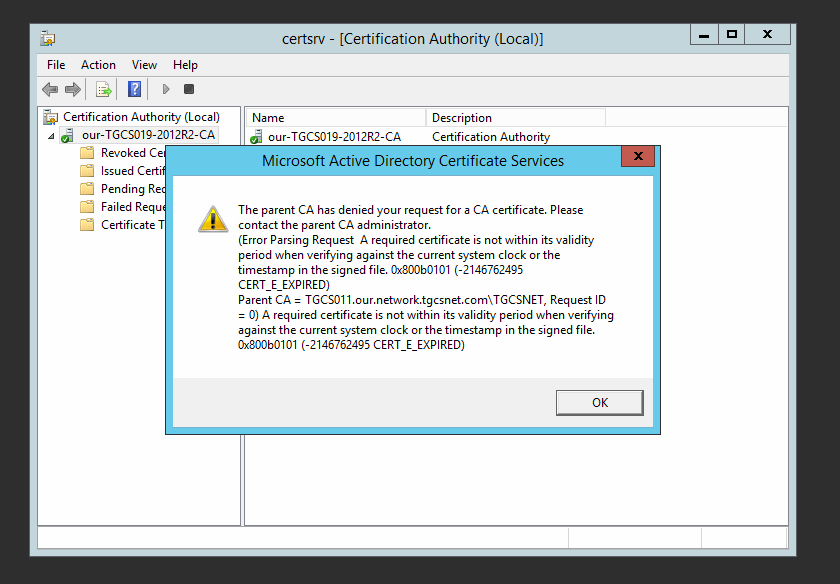
To make it clearer the issue is the certificate you are requesting is for a duration outside the current validity of the CA's cert.
I.e. Your root CA certificate expiration is Jan 2021.
The Dcs are trying to renew their certificate for one year.
May 2021. The error points that a certificate can not be issued till may 2021 because the root certificate is not valid until then.
I.e. Your root CA certificate expiration is Jan 2021.
The Dcs are trying to renew their certificate for one year.
May 2021. The error points that a certificate can not be issued till may 2021 because the root certificate is not valid until then.
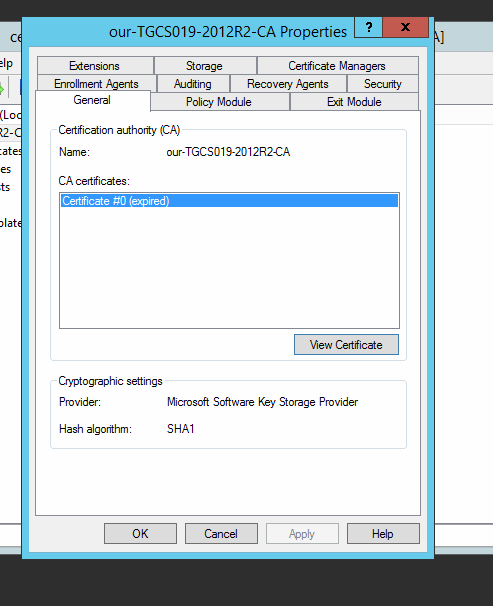
Get properties for the CA, you are lookin in the wrong place.
The root CA is self signed.
In the left pane, right click on the second item from the top and get properties.
You shoukd see the cert there that you can renew.
The root CA is self signed.
In the left pane, right click on the second item from the top and get properties.
You shoukd see the cert there that you can renew.
Right-click on the certificate, does it give you an option to renew?
ASKER
Arnold,
Right click is not an option on that general tab only the view certificate button
Right click is not an option on that general tab only the view certificate button
B if you get back to where you were, when you right click, did it give you an option to generate a new self signed cert?
Renew, self signed. Not to be submitted.
You may have to use a certutil.
The issue might be because the certificate expired.
Renew, self signed. Not to be submitted.
You may have to use a certutil.
The issue might be because the certificate expired.
See https://serverfault.com/questions/647345/generate-new-self-signed-ca-for-windows-2012-ca
Remember if you use new key, you would need to republish the new cert in the GPO..
Remember if you use new key, you would need to republish the new cert in the GPO..
Renew CA Certificate
Do you have an offlibe toot CA server.
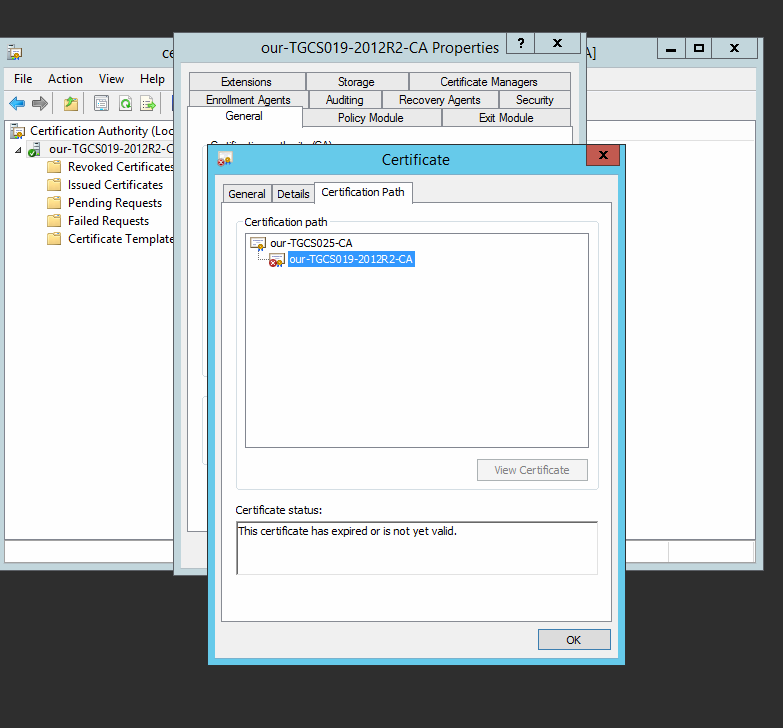
In the certificate view, pkease look at the certification path. Is the certificate here sel
Where is our-TCGS025-CA? This one is the root CA that signed/issued the certificate that has expired.
Is this an issuing CA role?
In the certificate view, pkease look at the certification path. Is the certificate here sel
Where is our-TCGS025-CA? This one is the root CA that signed/issued the certificate that has expired.
Is this an issuing CA role?
Our-TGCS025-CA is your root CA, possibly commonly offline unless needed as in this case to renew an intermediate CA
ASKER
Can I just create a new CA Root Cert? If so what is the best method?
That may cause other issues.
Root ca (usually offlibe)
Issuing CA, certificate signed by the root CA
All clients get certs from issuing CA
Root ca (usually offlibe)
Issuing CA, certificate signed by the root CA
All clients get certs from issuing CA
ASKER
That server does not exist any longer and it was an old exchange server never used as a cert server
I did install a cert from GoDaddy for my exchange 2010 back then The CA Root I do not recall how it was created.
I would like my Cert Server to be the one who issues the certs
Has to be a way to do this but as I said I am not a cert expert
Thanks
I did install a cert from GoDaddy for my exchange 2010 back then The CA Root I do not recall how it was created.
I would like my Cert Server to be the one who issues the certs
Has to be a way to do this but as I said I am not a cert expert
Thanks
You could try during the CA renewal, do not point it to TGCSNET and see if it has another option dealing with where the root is.
Parent CA two or three images before.
Parent CA two or three images before.
ASKER
I will try to generate a new one tomorrow
Look at the link I posted that deals with using certutil to generate a self signed cert.
note you would need to import it. then you would need to use the public certificate (without the private key) and load it into the GPO where you distribute your PKI policy
Or the CA's cert will not be trusted and errors will be generated for untrusted issuer....
note you would need to import it. then you would need to use the public certificate (without the private key) and load it into the GPO where you distribute your PKI policy
Or the CA's cert will not be trusted and errors will be generated for untrusted issuer....
ASKER
Arnold
In the article I found these two command
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
In the article I found these two command
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>certutil -setreg ca\csp\cnghashalgorithm sha256
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\our-TGCS019-2012R2-CA\csp:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\our-TGCS019-2012R2-CA\csp:
Old Value:
CNGHashAlgorithm REG_SZ = sha256
CNGHashAlgorithm REG_SZ = sha256
New Value:
CNGHashAlgorithm REG_SZ = sha256
CertUtil: -setreg command completed successfully.
The CertSvc service may need to be restarted for changes to take effect.
CNGHashAlgorithm REG_SZ = sha256
CertUtil: -setreg command completed successfully.
The CertSvc service may need to be restarted for changes to take effect.
C:\Windows\system32>net stop certsvc && net start certsvc
The Active Directory Certificate Services service is stopping.
The Active Directory Certificate Services service was stopped successfully.
The Active Directory Certificate Services service is stopping.
The Active Directory Certificate Services service was stopped successfully.
The Active Directory Certificate Services service is starting.
The Active Directory Certificate Services service was started successfully.
The Active Directory Certificate Services service was started successfully.
C:\Windows\system32>
after
and renew CA certificate. During prompt select to generate a new key pair.
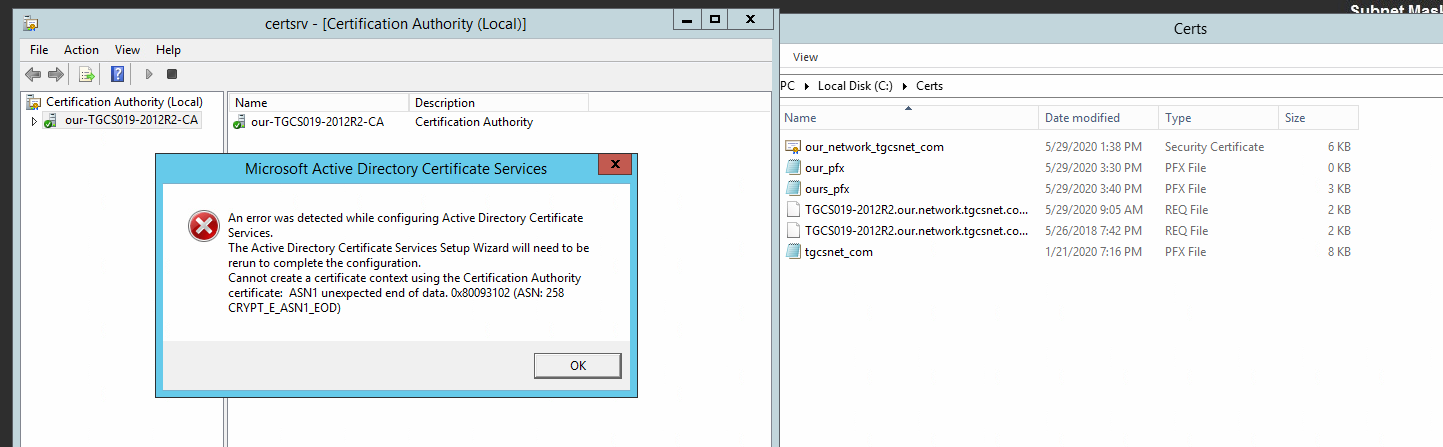
Tried that and still same errors as above access denied.
what if I remove the Active Directory Certificate Services
And then reinstall it that process creates the new ca root during setup
Thoughts?
when you try to generate the CA with a new KEY, are you still letting it point to TGCSNET as the parent CA?
What are the other options in the drop down?
Three should be an option to point to self
What are the other options in the drop down?
Three should be an option to point to self
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Aarnold
I am so confused at this point.
Yes I have no way to get the original server back online and running the physical box is no longer here.
The article only shows you to backup the cert then uninstall then restore it. I do not want to restore this I want to create a whole new CA Root cert how can that be done
I am so confused at this point.
Yes I have no way to get the original server back online and running the physical box is no longer here.
The article only shows you to backup the cert then uninstall then restore it. I do not want to restore this I want to create a whole new CA Root cert how can that be done
Create a new VM, install the CA role as an offline CA, use the renewal note the images for the request and have this new root CA sign it. As well as use the new Cas public certificate to add it into the GPO to push as trusted issuer.
The certificate was last renewed last year.
Do you have a backup of the former root ca?
Do you have a backup of the former root ca?
A separate offline root CA ..
Another option is if you can get OpenSSL or have. Line bo with OpenSSL, to use OpenSSL as the CA authority and then ign the request from this issuing CA......
Another option is if you can get OpenSSL or have. Line bo with OpenSSL, to use OpenSSL as the CA authority and then ign the request from this issuing CA......
ASKER
No that server is long gone as is the backup for that
I will build a new Windows 2019 server and install the CA on it
I will build a new Windows 2019 server and install the CA on it
ASKER
I have a Windows 2019 Server with OpenSSL installed
How do I use openssl to create certs?
How do I use openssl to create certs?
Install win2019 core, add the role to minimize resource consumption. Not joined that can be kept offline.
Possibly change the issuing CAs certificate duration from 1 year to three....
Possibly change the issuing CAs certificate duration from 1 year to three....
ASKER
Should I then uninstall the role on my existing cert server?
Look at the openssl commands only.
Note the self sign cert hs to be used Bd publiched in GPO to make it trusted.
https://networklessons.com/uncategorized/openssl-certification-authority-ca-ubuntu-server
Note the certificate is valid for 10 years.
Make sure to backup and keep the private key. This way you can .... At no time reuse it to ..
Note the self sign cert hs to be used Bd publiched in GPO to make it trusted.
https://networklessons.com/uncategorized/openssl-certification-authority-ca-ubuntu-server
Note the certificate is valid for 10 years.
Make sure to backup and keep the private key. This way you can .... At no time reuse it to ..
No, keep the existing as the issuing CA. And use a trusted OpenSSL CA as the signer of the one you hve.
ASKER
Should I install openssh on that Windows 2012 R2 server which is my cert server
Completely up to you, unrelated, not a requirement for OpenSSL.
What prompted the question?
What prompted the question?
ASKER
You said to use openssl commands
ASKER
Arnold,
I have an ubuntu server running on my network
I can install openssl on that one create a new cert then copy it to my cert server correct?
I have an ubuntu server running on my network
I can install openssl on that one create a new cert then copy it to my cert server correct?
ASKER
Arnold
I have a rapberry PI on my network that would be a better idea
Openssl is already on that host
Thoughts?
I have a rapberry PI on my network that would be a better idea
Openssl is already on that host
Thoughts?
It does not really matter where the OpenSSL is.
It's use is just to sign the cert of the issuing CA.
Just make sure you backup the private key so that you can use it ......
It's use is just to sign the cert of the issuing CA.
Just make sure you backup the private key so that you can use it ......
ASKER
Not sure why you used the same name as the CA..
This will be
You needed to run the renew CA on the current server.
Get the CSR and have it signed by the .
If that is what you did, import the resulting certificate which should complete the renewal.
This will be
You needed to run the renew CA on the current server.
Get the CSR and have it signed by the .
If that is what you did, import the resulting certificate which should complete the renewal.
ASKER
Arnold
How to I convert the private key and signed cert to a PFX file?
Then import to the CA ? I see no import option on the interface.
Found this method did not work
root@raspberrypi:~/ca/requests# openssl pkcs12 -inkey our_network.pem -in cert_server.csr -export -out our_pfx.pfx
Enter pass phrase for our_network.pem:
unable to load certificates
root@raspberrypi:~/ca/requests#
How to I convert the private key and signed cert to a PFX file?
Then import to the CA ? I see no import option on the interface.
Found this method did not work
root@raspberrypi:~/ca/requests# openssl pkcs12 -inkey our_network.pem -in cert_server.csr -export -out our_pfx.pfx
Enter pass phrase for our_network.pem:
unable to load certificates
root@raspberrypi:~/ca/requests#
resign the csr from before using the sha256 option.
https://stackoverflow.com/questions/25421399/ecdsa-sign-using-openssl-without-asn1-encoding-the-hash
https://stackoverflow.com/questions/25421399/ecdsa-sign-using-openssl-without-asn1-encoding-the-hash
Something else might be at issue.
the text of the certificate when viewed in notepad/text editor has the format
--begin certificate --
--end certificate --
you also may have to import the OPENSSL CA certificate as trusted CA on this system.
https://stackoverflow.com/questions/25421399/ecdsa-sign-using-openssl-without-asn1-encoding-the-hash
https://stackoverflow.com/questions/25421399/ecdsa-sign-using-openssl-without-asn1-encoding-the-hash
Something else might be at issue.
the text of the certificate when viewed in notepad/text editor has the format
--begin certificate --
--end certificate --
you also may have to import the OPENSSL CA certificate as trusted CA on this system.
ASKER
You posted the same link twice is that correct?
Which option should I use
Sample command line would be nice
Which option should I use
Sample command line would be nice
I m uncertain why the first ASN1 error came up, in terms of whether the certificate was with an issue.
Try with both to see which certificate will import without an error.
The two options covered I. The link is to ign using sha256 ....
Did you add the public certificate of the OpenSSL CA as a trusted CA to your server?
Try with both to see which certificate will import without an error.
The two options covered I. The link is to ign using sha256 ....
Did you add the public certificate of the OpenSSL CA as a trusted CA to your server?
ASKER
Arnold
my ca/requests folder
root@raspberrypi:~/ca/requests# ls
cert_server.csr our_network.pem our.network.pem our_network_tgcsnet_com.pem our_pfx.pfx ours_pfx.pfx
root@raspberrypi:~/ca/requests#
openssl dgst -sha256 -binary -out data.sha256 data.txt
after you can sign it:
However the signature is still in ASN.1 format. To receive r and s values of signature use openssl asn1parse:
Are these the commands I should run? which files should I use ?
Thanks
my ca/requests folder
root@raspberrypi:~/ca/requests# ls
cert_server.csr our_network.pem our.network.pem our_network_tgcsnet_com.pem our_pfx.pfx ours_pfx.pfx
root@raspberrypi:~/ca/requests#
openssl dgst -sha256 -binary -out data.sha256 data.txt
after you can sign it:
openssl pkeyutl -sign -inkey private.pem -in data.sha256 -out data.sigHowever the signature is still in ASN.1 format. To receive r and s values of signature use openssl asn1parse:
openssl asn1parse -inform DER -in data.sigAre these the commands I should run? which files should I use ?
Thanks
ASKER
Arnold
I tried this
root@raspberrypi:~/ca/requests# openssl dgst -sha256 -binary -out data.sha256 our_network.pem
root@raspberrypi:~/ca/requests# openssl pkeyutl -sign -inkey our_network.pem -in data.sha256 -out data.sig
Enter pass phrase for our_network.pem:
root@raspberrypi:~/ca/requests# openssl asn1parse -inform DER -in data.sig
Error in encoding
3069621456:error:0D07207B:asn1 encoding routines:ASN1_get_object:header too long:asn1_lib.c:157:
root@raspberrypi:~/ca/requests#
I tried this
root@raspberrypi:~/ca/requests# openssl dgst -sha256 -binary -out data.sha256 our_network.pem
root@raspberrypi:~/ca/requests# openssl pkeyutl -sign -inkey our_network.pem -in data.sha256 -out data.sig
Enter pass phrase for our_network.pem:
root@raspberrypi:~/ca/requests# openssl asn1parse -inform DER -in data.sig
Error in encoding
3069621456:error:0D07207B:asn1 encoding routines:ASN1_get_object:header too long:asn1_lib.c:157:
root@raspberrypi:~/ca/requests#
here is the question:
The files you created to setup the CA
you adjusted as suggested?
The below is the command that relies on your openssl.conf being configured to refer to the files for your CA It is part of the first link on setting up your own CA.
This is the step when you use your own OpenSSL CA to sign requests
.pem suffix deals with the formating of the requests and responses meaning they are in human redable, base64 encoded versus the other option DER which is a binary format. PEM is the common ....
openssl ca -in your_windows_issuing_CA.cs
Then you would use the TGCSCA_certificate.cert with the import CA certificate on the windows side.
The certificate will match the key used to generate the CSR in the RENEW CA certificate step.
If you try to import a certificate not matching the key, perhaps that is what the error meant.
usually openssl includes all the tools to setup your own CA.
at times it is in /etc/pki/misc
The files you created to setup the CA
you adjusted as suggested?
The below is the command that relies on your openssl.conf being configured to refer to the files for your CA It is part of the first link on setting up your own CA.
This is the step when you use your own OpenSSL CA to sign requests
.pem suffix deals with the formating of the requests and responses meaning they are in human redable, base64 encoded versus the other option DER which is a binary format. PEM is the common ....
openssl ca -in your_windows_issuing_CA.cs
Then you would use the TGCSCA_certificate.cert with the import CA certificate on the windows side.
The certificate will match the key used to generate the CSR in the RENEW CA certificate step.
If you try to import a certificate not matching the key, perhaps that is what the error meant.
usually openssl includes all the tools to setup your own CA.
at times it is in /etc/pki/misc
ASKER
Arnold
openssl ca -in your_windows_issuing_CA.csr -out TGCSCA_certificate.cert
Where do I get this file from your_windows_issuing_CA.csr ?????
openssl ca -in your_windows_issuing_CA.csr -out TGCSCA_certificate.cert
Where do I get this file from your_windows_issuing_CA.csr ?????
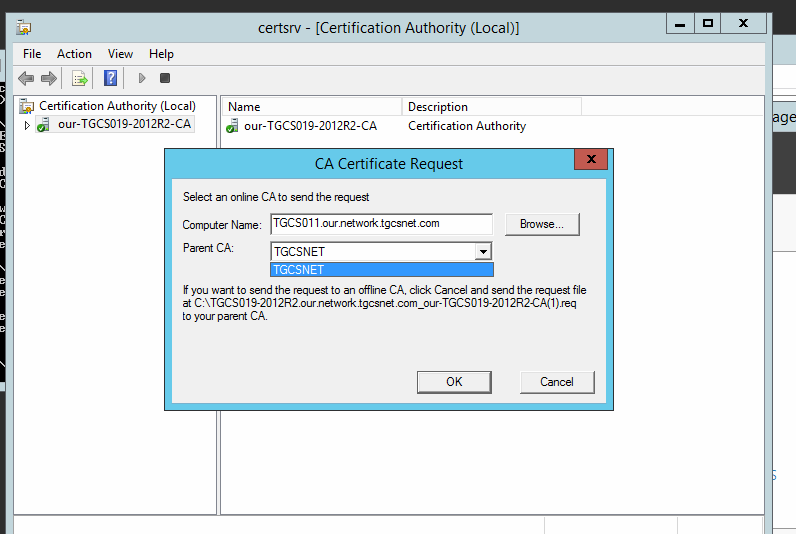
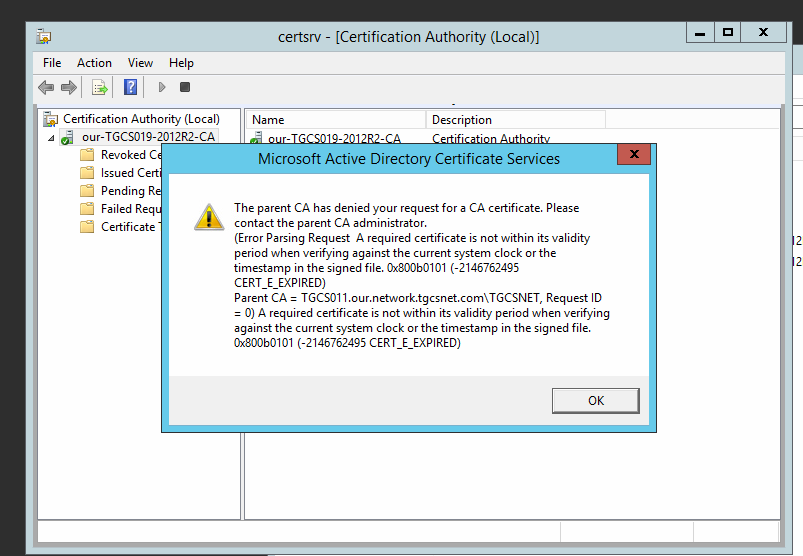
Ft his is the result of runningtherenew CA certificate Interface, note thebottomofyour posted image into what parent CA to subit the renewal request.
The bottom,
C:\........
The bottom,
C:\........
The CSR to sign is:
One step before submitting CSR for automatic processing to a CA
https://filedb.experts-exchange.com/incoming/2020/05_w22/1461305/1590757566590.png
Not sure of Themis better to access the image you posted.
One step before submitting CSR for automatic processing to a CA
https://filedb.experts-exchange.com/incoming/2020/05_w22/1461305/1590757566590.png
Not sure of Themis better to access the image you posted.
ASKER
Thomas, please see the image, the file location is stated right there above the buttons.
C:\TGCS......... IF you need to submit it to an offlibe CA
Once generated, signed, you would then import CA certificate.
C:\TGCS......... IF you need to submit it to an offlibe CA
Once generated, signed, you would then import CA certificate.
ASKER
Arnold
I see what you are showing now ok I coped to file to my RaspberryPi server and ran this
root@raspberrypi:~/ca/requests# ls
cert_server.csr data.sha256 data.sig our_network.pem our.network.pem our_network_tgcsnet_com.pem our_pfx.pfx ours_pfx.pfx TGCS019-2012R2.our.network.tgcsnet.com_our-TGCS019-2012R2-CA.req
root@raspberrypi:~/ca/requests# openssl ca -in TGCS019-2012R2.our.network.tgcsnet.com_our-TGCS019-2012R2-CA.req -out TGCSCA_certificate.cert
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for /root/ca/private/cakey.pem:
Check that the request matches the signature
Signature ok
The mandatory countryName field was missing
root@raspberrypi:~/ca/requests#
THe mandatory countryName field was missing?????
I see what you are showing now ok I coped to file to my RaspberryPi server and ran this
root@raspberrypi:~/ca/requests# ls
cert_server.csr data.sha256 data.sig our_network.pem our.network.pem our_network_tgcsnet_com.pem our_pfx.pfx ours_pfx.pfx TGCS019-2012R2.our.network.tgcsnet.com_our-TGCS019-2012R2-CA.req
root@raspberrypi:~/ca/requests# openssl ca -in TGCS019-2012R2.our.network.tgcsnet.com_our-TGCS019-2012R2-CA.req -out TGCSCA_certificate.cert
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for /root/ca/private/cakey.pem:
Check that the request matches the signature
Signature ok
The mandatory countryName field was missing
root@raspberrypi:~/ca/requests#
THe mandatory countryName field was missing?????
Unedited the OpenSSL.conf file and change the requirements from match to optional.
This was covered. In the CA setup link.
The default CA setting, profile is to match so if your CA certificate's location does not match the information you used in the subordinate CA info when created, it will as it has kicked it out, rejected.
Once you modify the OpenSSL.conf as noted rerun and it should go through.
This was covered. In the CA setup link.
The default CA setting, profile is to match so if your CA certificate's location does not match the information you used in the subordinate CA info when created, it will as it has kicked it out, rejected.
Once you modify the OpenSSL.conf as noted rerun and it should go through.
ASKER
Arnold.
I thought I made all the changes per the article you sent me.
I attached the file for your review
openssl.cnf
I thought I made all the changes per the article you sent me.
I attached the file for your review
openssl.cnf
ASKER
Arnold,
Everything looks good now
Thank you for all the help
Everything looks good now
Thank you for all the help
No, I modified the openssl.conf file on the CA side to not validate the state, city.
Not sure of which the one before last applies. the config file I was talking about dealt with getting the openSSL CA self-signed certificate issued with the CA designation..
Were you able to add the Certification Authority admin tools?
backup the CA. you can also export the CA's certificate with the private key as a PFX files.
If needed you would be able to use openssl to convert the .pfx file into the .pem format which will have the two
--start private key --
--end private key --
--begin certificate --
--- end certificate ---
and then you would be able to use the openssl to sign/certs.....
glad I could help
Not sure of which the one before last applies. the config file I was talking about dealt with getting the openSSL CA self-signed certificate issued with the CA designation..
Were you able to add the Certification Authority admin tools?
backup the CA. you can also export the CA's certificate with the private key as a PFX files.
If needed you would be able to use openssl to convert the .pfx file into the .pem format which will have the two
--start private key --
--end private key --
--begin certificate --
--- end certificate ---
and then you would be able to use the openssl to sign/certs.....
glad I could help


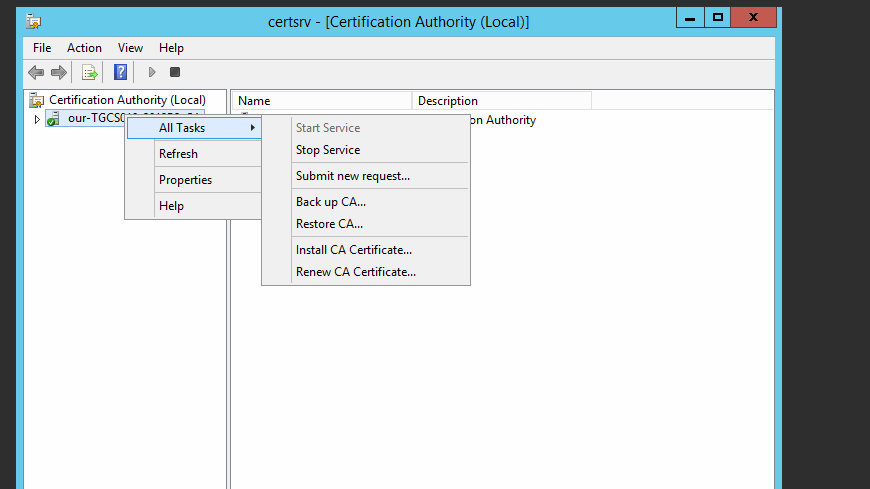
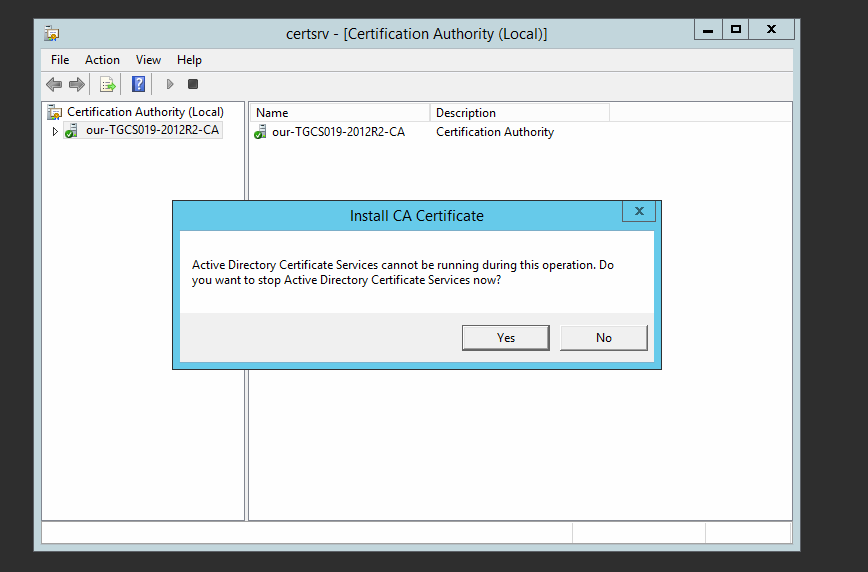
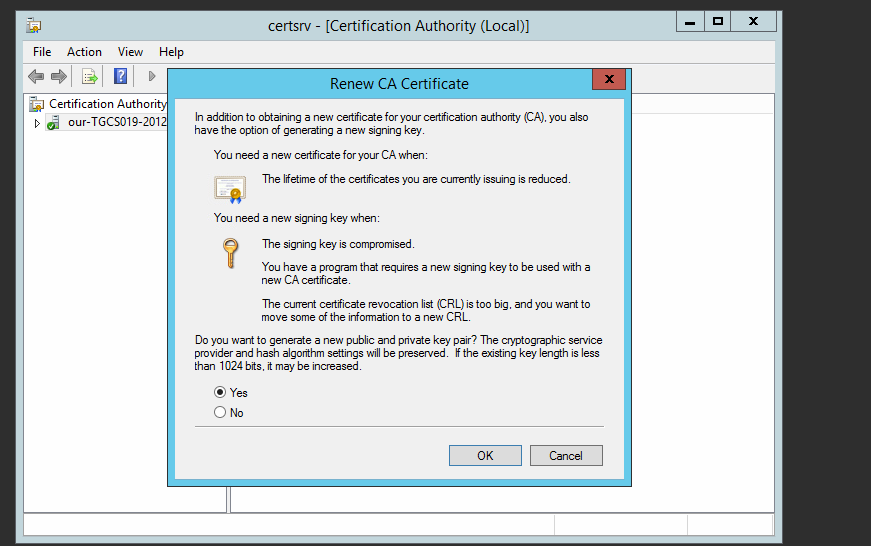
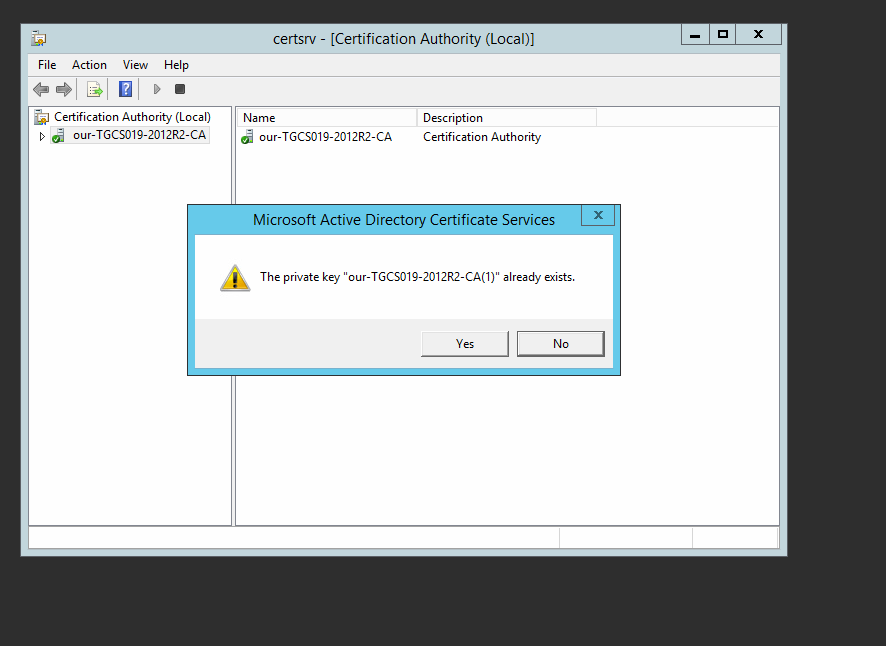
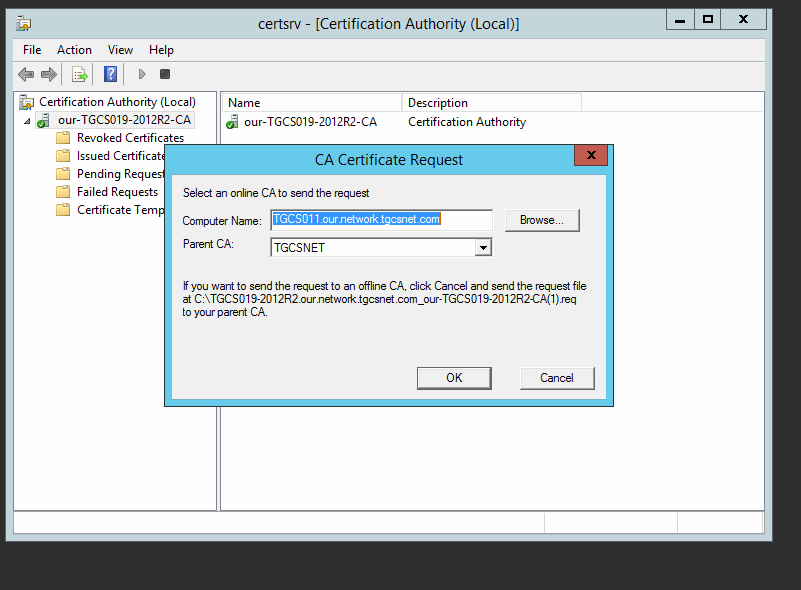

Use the same key.
This is done within the Certificate authrority administrative tool, right click on the existing cert and renew it.
Note if you use a new KEY , you would need to add the public cert of the cert into the GPO to push out.