TPM error on devices - automation to resolve
Im trying to automate a manual process where we have a TPM issue on machines and bitlocker is suspending. We have resolved the workflow on how to do the individual parts but to work through it means allot of manual checking and shifting computers between OU's and manually running scripts. Looking for some help;
Step 0: Use SCCM to run script against a "Validation OU"
Step 1: Checking TPM (Ready) and Disk Status (GPT) and output to file
Powershell
Get-Disk | Out-File -FilePath "\\server\reports\DiskStatus\$env:computername.txt"
Get-TPM | Out-File -FilePath "\\server\reports\TPMStatus\$env:computername.txt"
This outputs 2 files that look like:
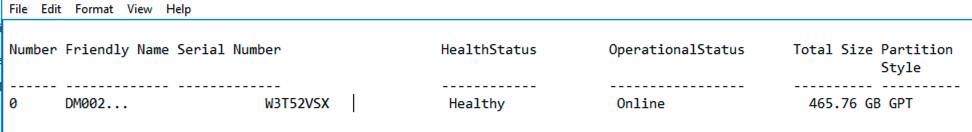
Disk Status - Filename is computer name and looking at disk partition style eq "GPT"
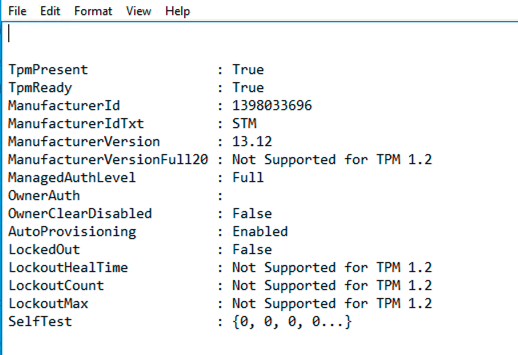
 TPM Status - Filename is computer name and have script to create summary CSV for status
TPM Status - Filename is computer name and have script to create summary CSV for status
 Step 2: Computers with GPT and TPM ready are moves from validation OU to DisableDG OU
Step 2: Computers with GPT and TPM ready are moves from validation OU to DisableDG OU
Step 3: Unencrypt Bitlocker drive and Disable Device guard
Powershell
# Check if the disk is fully decrypted
if ((Get-BitLockerVolume -MountPoint "C:").VolumeStatus -ne "FullyDecrypted") {
disable-BitLocker -MountPoint "C:"
}
# Check if the DG/CG is already disabled
$value = Get-ItemProperty -Path HKLM:\System\CurrentControlSet\Control\DeviceGuard -Name "EnableVirtualizationBasedSecurity" -ErrorAction SilentlyContinue
if ($value -ne 1) {
# exit 2627
}
#Disable DeviceGuard using DGreadiness tool
\\server\reports\DisableDG-CG\dgreadiness_v3.7\DG_Readiness_Tool_v3.7.ps1 -disable -autoreboot
New-Item -Path “\\server\reports\DeviceGuardActioned\" -Name "$($env:COMPUTERNAME).txt" -ItemType "file" -Value "DeviceGuardActioned"
#Restart-Computer
Get-CimInstance –ClassName Win32_DeviceGuard –Namespace root\Microsoft\Windows\DeviceGuard | Out-File -FilePath “\\server\reports\DeviceGuardStatus\$env:computername.txt"
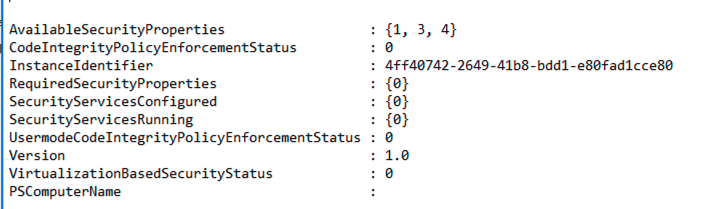
This outputs a files that look like: Checks that DeviceGuard is disabled
SecurityServicesRunning : {0}
 Step 4: Computers with Device Guard Disabled are moved from DisableDG OU to EnableBitlocker OU
Step 4: Computers with Device Guard Disabled are moved from DisableDG OU to EnableBitlocker OU
Step 5: Group Policy will enable Bitlocker, check status
Powershell
Get-BitLockerVolume -MountPoint "C:" | Out-File -FilePath "\\server\reports\BitlockerStatus\$env:computername.txt"
Step 6: Computers with Bitlocker enabled are then moved back into the normal workstation OU
My problem is when the results are exported into a single file, I am struggling to then script the searching of the status's in each file, pull the computer name and move them into the correct OU. So the next step can begin. We are basically going through each file one by one and then manually adding them to a CSV a then running a script on that CSV to move OU.
Powershell: To run against file to move OU
#Check if file is empty
if((Get-Content "\\server\reports\Process-TPM\status-computers.txt") -eq $Null){
exit
}
# Specify path to the text file with the computer account names.
$computers = Get-Content \\server\reports\Process-TPM\status-computers.txt
# Specify the path to the OU where computers will be moved.
$TargetOU = "OU=aa.validation,OU=devices,DC=domain,DC=com"
ForEach( $computer in $computers){
Get-ADComputer $computer |
Move-ADObject -TargetPath $TargetOU
}
#Movefile to Archive Location once processed
move-item -path \\server\reports\Process-TPM\status-computers.txt -destination \\server\reports\Process-TPM\ArchiveLog\status-computers.txt
#Create a new File
New-Item -ItemType "file" -Path "\\server\reports\Process-TPM\status-computers.txt"
#rename moved file
rename-item -path \\server\reports\Process-TPM\ArchiveLog\status-computers.txt -newname status-Computers$(get-date -format "yyyyMMdd").txt
Step 0: Use SCCM to run script against a "Validation OU"
Step 1: Checking TPM (Ready) and Disk Status (GPT) and output to file
Powershell
Get-Disk | Out-File -FilePath "\\server\reports\DiskStatus\$env:computername.txt"
Get-TPM | Out-File -FilePath "\\server\reports\TPMStatus\$env:computername.txt"
This outputs 2 files that look like:
Disk Status - Filename is computer name and looking at disk partition style eq "GPT"
 TPM Status - Filename is computer name and have script to create summary CSV for status
TPM Status - Filename is computer name and have script to create summary CSV for status Step 2: Computers with GPT and TPM ready are moves from validation OU to DisableDG OU
Step 2: Computers with GPT and TPM ready are moves from validation OU to DisableDG OUStep 3: Unencrypt Bitlocker drive and Disable Device guard
Powershell
# Check if the disk is fully decrypted
if ((Get-BitLockerVolume -MountPoint "C:").VolumeStatus -ne "FullyDecrypted") {
disable-BitLocker -MountPoint "C:"
}
# Check if the DG/CG is already disabled
$value = Get-ItemProperty -Path HKLM:\System\CurrentControlSet\Control\DeviceGuard -Name "EnableVirtualizationBasedSecurity" -ErrorAction SilentlyContinue
if ($value -ne 1) {
# exit 2627
}
#Disable DeviceGuard using DGreadiness tool
\\server\reports\DisableDG-CG\dgreadiness_v3.7\DG_Readiness_Tool_v3.7.ps1 -disable -autoreboot
New-Item -Path “\\server\reports\DeviceGuardActioned\" -Name "$($env:COMPUTERNAME).txt" -ItemType "file" -Value "DeviceGuardActioned"
#Restart-Computer
Get-CimInstance –ClassName Win32_DeviceGuard –Namespace root\Microsoft\Windows\DeviceGuard | Out-File -FilePath “\\server\reports\DeviceGuardStatus\$env:computername.txt"
This outputs a files that look like: Checks that DeviceGuard is disabled
SecurityServicesRunning : {0}
 Step 4: Computers with Device Guard Disabled are moved from DisableDG OU to EnableBitlocker OU
Step 4: Computers with Device Guard Disabled are moved from DisableDG OU to EnableBitlocker OUStep 5: Group Policy will enable Bitlocker, check status
Powershell
Get-BitLockerVolume -MountPoint "C:" | Out-File -FilePath "\\server\reports\BitlockerStatus\$env:computername.txt"
Step 6: Computers with Bitlocker enabled are then moved back into the normal workstation OU
My problem is when the results are exported into a single file, I am struggling to then script the searching of the status's in each file, pull the computer name and move them into the correct OU. So the next step can begin. We are basically going through each file one by one and then manually adding them to a CSV a then running a script on that CSV to move OU.
Powershell: To run against file to move OU
#Check if file is empty
if((Get-Content "\\server\reports\Process-TPM\status-computers.txt") -eq $Null){
exit
}
# Specify path to the text file with the computer account names.
$computers = Get-Content \\server\reports\Process-TPM\status-computers.txt
# Specify the path to the OU where computers will be moved.
$TargetOU = "OU=aa.validation,OU=devices,DC=domain,DC=com"
ForEach( $computer in $computers){
Get-ADComputer $computer |
Move-ADObject -TargetPath $TargetOU
}
#Movefile to Archive Location once processed
move-item -path \\server\reports\Process-TPM\status-computers.txt -destination \\server\reports\Process-TPM\ArchiveLog\status-computers.txt
#Create a new File
New-Item -ItemType "file" -Path "\\server\reports\Process-TPM\status-computers.txt"
#rename moved file
rename-item -path \\server\reports\Process-TPM\ArchiveLog\status-computers.txt -newname status-Computers$(get-date -format "yyyyMMdd").txt
ASKER
we have found that when TPM warning puts bitlocker is suspended state. if we then enable again 48 hours later again it is suspended. hardware vendor (dell and Acer) as same happening on both models advised to use DeviceGuard readiness tool to disable DeviceGuard then re-encrypt HDD and then after encryption enable DeviceGuard only using readiness tool. we have tested and this process resolved the issue (22 days and counting) but the process is laborious and trying to automation. I just struggling with the powershell
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
When a TPM "acts up", I would resolve the TPM problem, remove the TPM bitlocker protector (if needed) and re-create it. Never would I have to decrypt.