Fred P.
asked on
Active Directory Certificate Services Migration
Hi,
We currently have an AD infrastructure with 4 old (2012 non r2) and 4 new (2019) DC's.
On one of the old DC's there is the certificate authority installed which needs to be removed because of the decommissioning of the old DC's. Based on the certs that are inside, it's only used for auto enrollment. I see computer certificates mostly for desktops, and the 'default' certificates that are requested by DC's (Kerberos, Directory email, Domain controller certs)
I have set up a separate Server 2019 VM that will be used as certificate authority. So the CA infra needs to be moved from a 2012 to a 2019 (with different server names/IP's).
I read through this documentation:
Most articles state that a server name change is not possible, while some say it's possible.
Also it seems that in 2012r2 some internal changes have been made to ADCS DB, so the straight migration is not possible.
I'm not sure how to continue... Should I try to do the migration, or is it easier to setup a new CA from scratch and make all clients request a new certificate?
But in that second scenario, how do I configure that AD uses the new certificate store instead of the old one?
Thanks!
Fred
We currently have an AD infrastructure with 4 old (2012 non r2) and 4 new (2019) DC's.
On one of the old DC's there is the certificate authority installed which needs to be removed because of the decommissioning of the old DC's. Based on the certs that are inside, it's only used for auto enrollment. I see computer certificates mostly for desktops, and the 'default' certificates that are requested by DC's (Kerberos, Directory email, Domain controller certs)
I have set up a separate Server 2019 VM that will be used as certificate authority. So the CA infra needs to be moved from a 2012 to a 2019 (with different server names/IP's).
I read through this documentation:
- https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-r2-and-2008/ee126170(v=ws.10)
- https://techcommunity.microsoft.com/t5/itops-talk-blog/step-by-step-migrating-the-active-directory-certificate-service/ba-p/697674
- https://petri.com/migrate-restore-windows-server-2012-r2-certification-authority-to-new-server
Most articles state that a server name change is not possible, while some say it's possible.
Also it seems that in 2012r2 some internal changes have been made to ADCS DB, so the straight migration is not possible.
I'm not sure how to continue... Should I try to do the migration, or is it easier to setup a new CA from scratch and make all clients request a new certificate?
But in that second scenario, how do I configure that AD uses the new certificate store instead of the old one?
Thanks!
Fred
ASKER
Great! Thanks for the feedback!
How does that work? How do the clients/AD 'know' which of the 2 CA's to use?
all the clients should sort themselves out.
How does that work? How do the clients/AD 'know' which of the 2 CA's to use?
sorry - assuming the CA's are in "enterprise" mode - they are AD integrated. Then when you set auto-enroll on the cert templates - and have auto-enroll set within group policy (which it sounds like you already have) - then clients will read the certs they should auto-enroll from AD.....
based on this part of your initial question
Go into your existing templates on the existing CA and have a look for the auto-enroll permission.... and then check your GP's for the auto-enroll setting..... ill bet you that its there.
based on this part of your initial question
Based on the certs that are inside, it's only used for auto enrollment. I see computer certificates mostly for desktops, and the 'default' certificates that are requested by DC's (Kerberos, Directory email, Domain controller certs)
it sounds very much like auto-enroll has been used to distribute these certs.... you sure as hell wouldn't do that manually!
Go into your existing templates on the existing CA and have a look for the auto-enroll permission.... and then check your GP's for the auto-enroll setting..... ill bet you that its there.
ASKER
Hi,
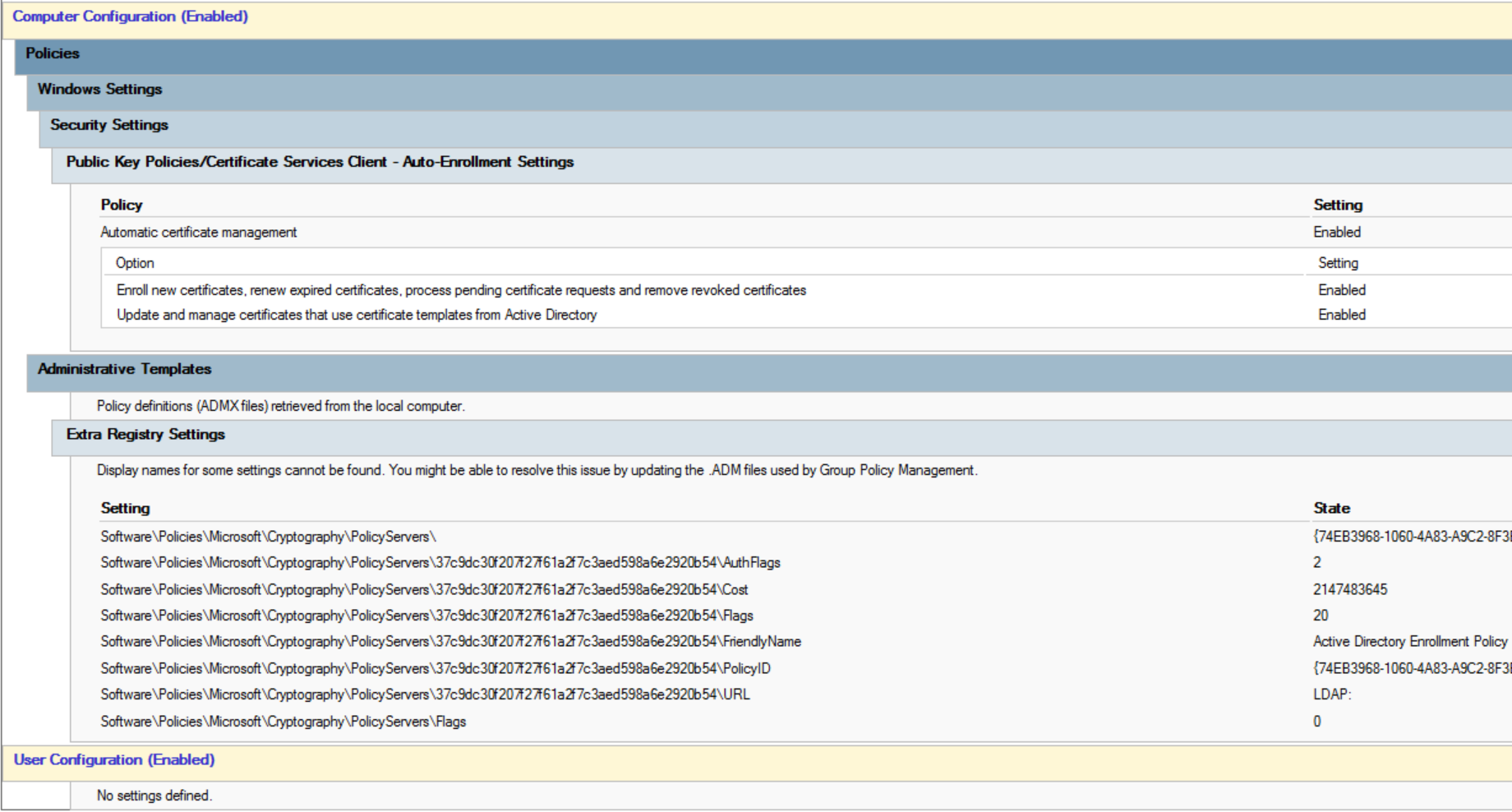
yes, it's indeed in enterprise mode. I also have the GPO in place:
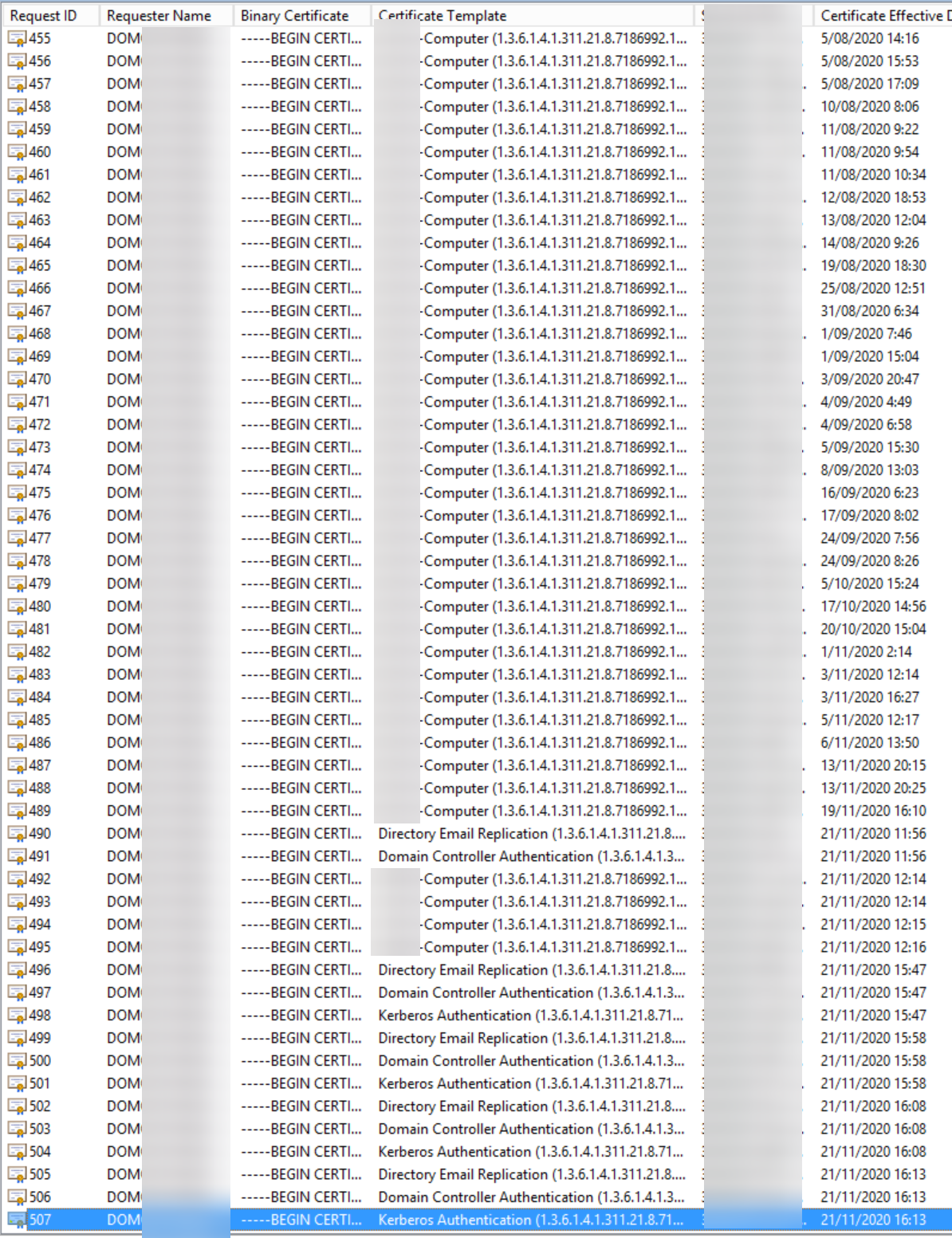
Sorry for the confusion, I didn't set this up myself. I checked again, and I can see these certs issued:
So only the -computer ones are a custom template. Checking that template I see it's published to AD:
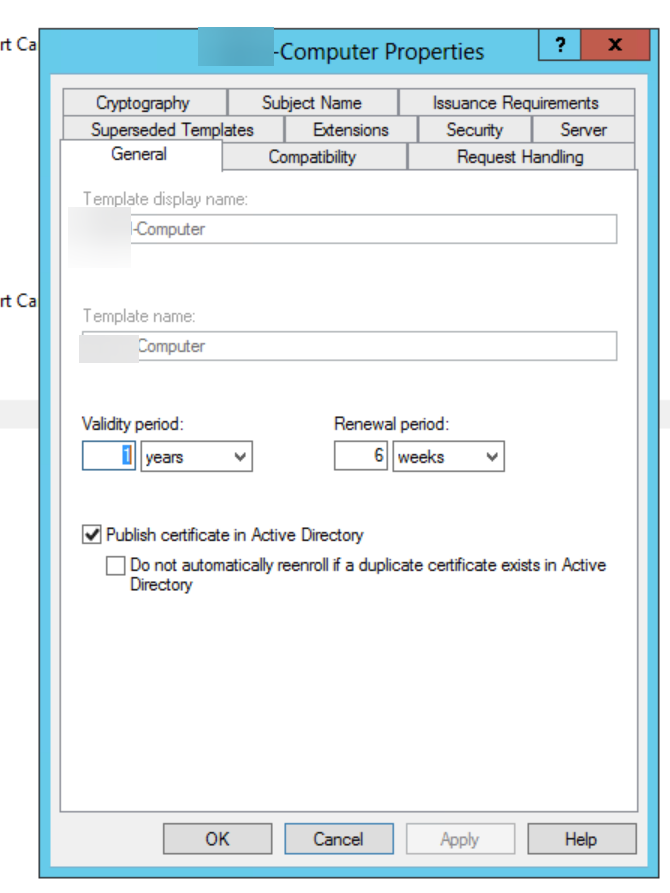
does that mean, once the new CA is setup, I need to unmark 'publish certificate in AD' on the old CA, and that way all clients will use the new one instead of the old one to request the cert?
Should I use the same CA name and export/import the PK to the new one, or can/should I use a new one?
Thanks again, appreciate it!
yes, it's indeed in enterprise mode. I also have the GPO in place:

Sorry for the confusion, I didn't set this up myself. I checked again, and I can see these certs issued:

So only the -computer ones are a custom template. Checking that template I see it's published to AD:

does that mean, once the new CA is setup, I need to unmark 'publish certificate in AD' on the old CA, and that way all clients will use the new one instead of the old one to request the cert?
Should I use the same CA name and export/import the PK to the new one, or can/should I use a new one?
Thanks again, appreciate it!
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Given the usages you talked about - it will be quite simple to setup the new CA from scratch.
Simply setup the new CA.... configure the cert templates you want for auto-enrollment (which you can copy from the existing CA if you want like for like) and all the clients should sort themselves out.
You can run the old/new CA side-by-side and therefore ensue all is good before the decommission of the old CA.
You've checked the key thing - the cert usages.... so if your confident that you have covered all the usage scenarios and covered off auto-enrollment to the new CA - your in a good position to get cracking on it.