Kaushal K
asked on
Class B Network Setup Help
I am setting up a new sonicwall and class B IP scheme as we are running out of IP's in our existing network setup using class C network. I have no intention of using any existing routers. Therefore this will be completely new setup and I want to use Class B IP scheme. I am looking for some help in understanding and a guidance on how to go about setting this up on my sonicwall tz570 appliance. I am novice to intermediate at this, so please be patient and forgive my ignorance or silly questions. Thank you
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
change to /22 (255.255.252.0) gives you 1,022 addresses
ASKER
so changing SM only will give me 1022 IP's?
ASKER
also, if I want to stay clear from 192.168.0.x because most household routers have, then. I am thinking in long term and in future, if I want to implement VPN
so changing SM only will give me 1022 IP's?yes...you can use subnet calculator to help
https://www.calculator.net/ip-subnet-calculator.html
if I want to stay clear from 192.168.0.x because most household routers have, then. I am thinking in long term and in futurei put that as an example since i don't know what you are using now
if you are using that address space then you can change it; subnet mask is the simplest but probably good idea to change (though probably more work) to avoid conflicts
ASKER
OK. So according to your comment above and subnet calculator, if I go with
201.168.0.1/16 with subnet 255.255.0.0, I would get about 65,534 usable hosts. I am just trying to understand. Obviously, this is too extreme in regards to hosts.
So then, I can just assign static IP's to devices in any form, example:
50 devices on 201.168.0.5-55
100 devices on 201.168.7.1-101
.... and so on?
Correct me if I am wrong.
201.168.0.1/16 with subnet 255.255.0.0, I would get about 65,534 usable hosts. I am just trying to understand. Obviously, this is too extreme in regards to hosts.
So then, I can just assign static IP's to devices in any form, example:
50 devices on 201.168.0.5-55
100 devices on 201.168.7.1-101
.... and so on?
Correct me if I am wrong.
unless you're completely divorced from the internet the 201168.x.x space is owned by someone as these are ublic routable addresseses
use 172.16.x.x or 10.x..x.x ranges
use 172.16.x.x or 10.x..x.x ranges
Don't think Class A/B/C, think of subnet and how many clients it allows. As Seth has shown, you can go between Class B (/16) and Class C (/24) and all should work if you get enough IP addresses.
How many devices are you really looking to allow? Consider whether they should be in different subnets, allocated by the DHCP server or by VLANs. Do all of the devices need access to the same resources (other than internet access)? If not, consider segregating them.
How many devices are you really looking to allow? Consider whether they should be in different subnets, allocated by the DHCP server or by VLANs. Do all of the devices need access to the same resources (other than internet access)? If not, consider segregating them.
ASKER
At least 200 devices are handheld scanners which uses our 15 AP's throughout our warehouse. There are 35 security camera's. 15 printers throughout the facility. 15 office computers. 65 warehouse computers. 15 remote employees who use remote paid service to access our resources (would prefer VPN access to them, eventually). I would guess 30 miscellaneous devices on premise that attach to AP's.
We have no windows servers or any servers for that matter.
These are approximates. Except for warehouse computers, I would like to have all other devices on same subnet so that it can be centrally managed and administered, unless there are other options, which I am open to.
We have no windows servers or any servers for that matter.
These are approximates. Except for warehouse computers, I would like to have all other devices on same subnet so that it can be centrally managed and administered, unless there are other options, which I am open to.
if I want to stay clear from 192.168.0.x because most household routers have, then. I am thinking in long term and in futureUsing 192.168.x.x is widely used and I would stick with it. If you want to avoid the above, you can use for instance the 192.168.200.0 network.
I would like to have all other devices on same subnet so that it can be centrally managed and administered, unless there are other options, which I am open to.They can be managed and they can be in different networks at the same time.
To get more IP addresses, you can use mask /23 or /22 which give you more IP addresses.
Another option I prefer and I would go for is splitting your devices into multiple networks. For instance, I would use 192.168.100.0 /24 for scanners, 192.168.101.0 /24 for computers and mobile devices, 192.168.102.0 /24 for cameras, printers, and other devices, etc.
Class A/B/C/ networking is so... 1990'; as several mentioned before adjust your netmask.
Also if you use one of the 192.168.x.y networks and adjust the netmask to /16 you just occupy all the 192.168 subnets.
There is a huge disadvantage to big networks in one netrange.
All systems are talking in their LAN with broadcast traffic (ARP, DHCP f.e.) meaning ALL systems in the LAN get bothered and are possibly responding.
Broadcasts are restricted to their own LAN ==> creating multiple small LAN's reduce this amount of overhead a lot.
Possibly there are security benefits as well if the LAN;s are separated by firewalls, at least some control on what device can access what other device can be controled.
esp. if things like clusters are used a LAN can be overwhelmed as at least some of the cluster protocols are broadcast traffic. With Windows clusters ALL traffic going to the cluster is in effect a multicast stream in the LAN. So each Windows Cluster should be in it's own LAN, well separated from all other systems.
Also if you use one of the 192.168.x.y networks and adjust the netmask to /16 you just occupy all the 192.168 subnets.
There is a huge disadvantage to big networks in one netrange.
All systems are talking in their LAN with broadcast traffic (ARP, DHCP f.e.) meaning ALL systems in the LAN get bothered and are possibly responding.
Broadcasts are restricted to their own LAN ==> creating multiple small LAN's reduce this amount of overhead a lot.
Possibly there are security benefits as well if the LAN;s are separated by firewalls, at least some control on what device can access what other device can be controled.
esp. if things like clusters are used a LAN can be overwhelmed as at least some of the cluster protocols are broadcast traffic. With Windows clusters ALL traffic going to the cluster is in effect a multicast stream in the LAN. So each Windows Cluster should be in it's own LAN, well separated from all other systems.
ASKER
I don't mind splitting the network however, how would I access devices on different network from central location.
For example if printers are on different network (192.168.201.x), how would I access those peripherals from my computer (192.168.200.x)?
For example if printers are on different network (192.168.201.x), how would I access those peripherals from my computer (192.168.200.x)?
Routing will deal with it.
ASKER
I guess my next question is, using 192.168.x.x or any other scheme with /22 or /23, I would be getting 254 IP addresses in each network?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Example:
You have ranges 192.168.100.0 /24 and 192.168.101.0 /24 so you make one big network 192.168.100.1-192.168.101.254 with mask /23.
You have ranges 192.168.100.0 /24 and 192.168.101.0 /24 so you make one big network 192.168.100.1-192.168.101.254 with mask /23.
/32 = 1 address (host only special case)
/31 = Special P2P case (adjusted from illegal to this) according to comment from Pedrag Jovic and https://tools.ietf.org/html/rfc3021
/30 = 2 addresses
/28 = 14 addresses
/26 = 62 addresses
/24 = 254 addresses
/23 = 510 addresses
/22 = 1022 addresses
/21 = 2046 addresses
/16 = 65534 addresses
The /31 case might require fidling with interface settings as converting it from a "broadcast type -> point 2 point.
That does need to be supported with higher level scripting on linux firewalls f.e.
The /31 case cannot be imposed on broadcast type networks on linux. (an ethernet adapter refuses to set -broadcast )
Exactly. I was talking about available addresses with the mask /23. The network then will be 192.168.100.0 /23 as you wrote.
ASKER
I will need to actually see these schemes in action in fw configuration.
You can probably create an unsused VLAN interface or use an unused port and test with that. Als creating routes should not pose a problem.
and setup a network with a differing netmask. if your firewall has trouble with CIDR notation (/xx) then translate it to a netmask.
and setup a network with a differing netmask. if your firewall has trouble with CIDR notation (/xx) then translate it to a netmask.
CIDR = Netmask
/32 = 255.255.255.255
/31 = 255.255.255.254
/30 = 255.255.255.252
/28 = 255.255.255.240
/25 = 255.255.255.128
/24 = 255.255.255.0
/23 = 255.255.254.0
/22 = 255.255.252.0
/21 = 255.255.248.0
etc.ASKER
yes, sonicwall does not have a CIDR notation option. i will have to translate it, which shouldn't be a problem.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
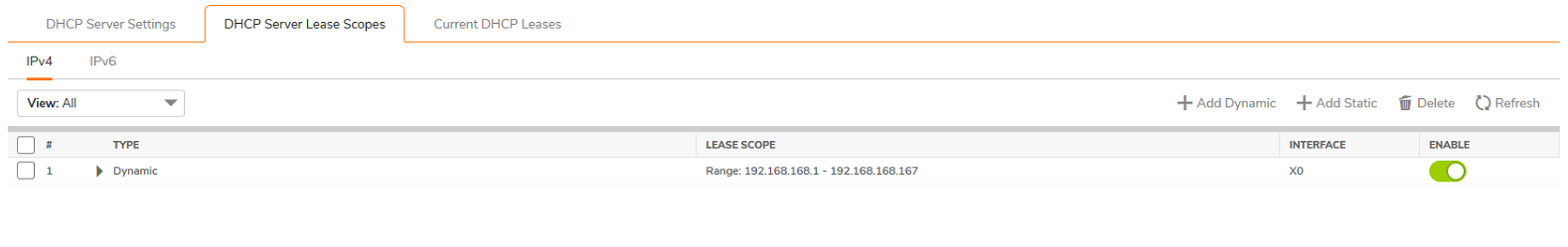
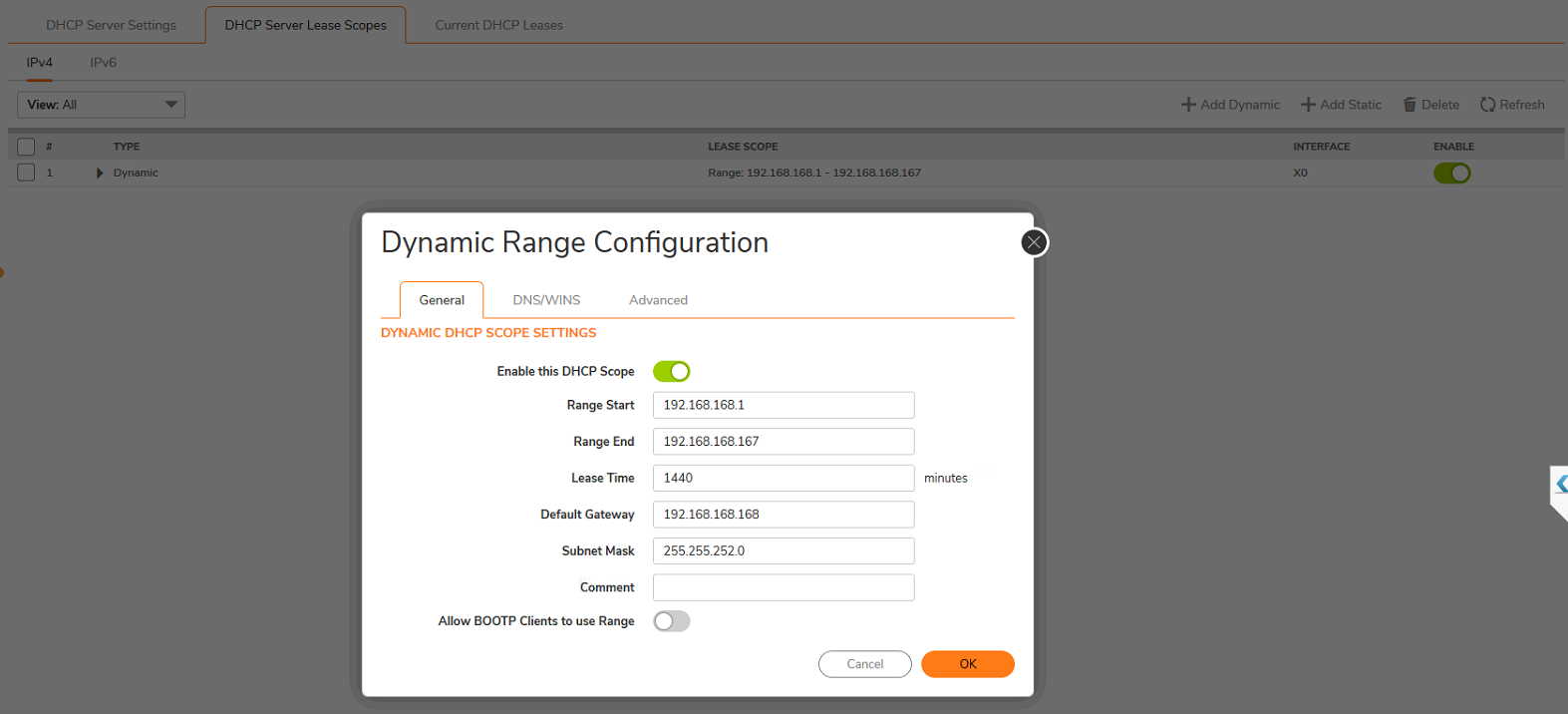
Ok so you enlarged from 192.168.168.0/24 -> 192.168.168.0/22 which translates to:
So you can change the address range up to those addresses.
Problem is: any system between 192.168.168.168-192.168.168.254 will need to be updated manual for the netmask and will need a reservation / exclusing from the DHCP range.
Or need to migrate to the high end of the 192.168.171.168 ... addresses.
Which ten also means adjusting the default GW.
$ ipcalc 192.168.168.0/22
Address: 192.168.168.0 11000000.10101000.101010 00.00000000
Netmask: 255.255.252.0 = 22 11111111.11111111.111111 00.00000000
Wildcard: 0.0.3.255 00000000.00000000.000000 11.11111111
=>
Network: 192.168.168.0/22 11000000.10101000.101010 00.00000000
HostMin: 192.168.168.1 11000000.10101000.101010 00.00000001
HostMax: 192.168.171.254 11000000.10101000.101010 11.11111110
Broadcast: 192.168.171.255 11000000.10101000.101010 11.11111111
Hosts/Net: 1022 Class C, Private InternetSo you can change the address range up to those addresses.
Problem is: any system between 192.168.168.168-192.168.168.254 will need to be updated manual for the netmask and will need a reservation / exclusing from the DHCP range.
Or need to migrate to the high end of the 192.168.171.168 ... addresses.
Which ten also means adjusting the default GW.
ASKER
Just an FYI. To access local Sonicwall on the web interface is 192.168.168.168. Therefore this was the default. I prefer not to use 192.168.xxx.xxx. What are my options?
choose any of the RFC1918 address subnets https://tools.ietf.org/html/rfc1918.
10.0.0.0/8
172.16.0/12
192.168.0.0/16
Try to avoid 192.168.0.0/22 & 192.168.252.0/22 as they are used a lot makeing an interconnection using VPN quite an interesting experience.
same for 172.12.0.0/22 or 10.0.0.0/22 use some random nets in the middle. If you need to connect to larger networks they will use those large addresses.
i just don't understand by not 192.168.x.x effectively there is NO difference between addresses.... 1.1.1.1 is as useful as 2.2.2.2 or 192.168.168.168....
10.0.0.0/8
172.16.0/12
192.168.0.0/16
Try to avoid 192.168.0.0/22 & 192.168.252.0/22 as they are used a lot makeing an interconnection using VPN quite an interesting experience.
same for 172.12.0.0/22 or 10.0.0.0/22 use some random nets in the middle. If you need to connect to larger networks they will use those large addresses.
i just don't understand by not 192.168.x.x effectively there is NO difference between addresses.... 1.1.1.1 is as useful as 2.2.2.2 or 192.168.168.168....
ASKER
I am just trying to understand the address space to use with possibility of future growth vpn access where home ip should not conflict with business lan ip space (am i correct in saying so?)
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
routing is an option for multiple subnet or vlan's. my question is: will i just be able to see the routed network (in other words just ping OR will i be able to access devices and computers on other subnet's/across subnets?
if i am able to access devices and peripherals across subnet through routing setup, then I am all for dividing groups/computers/departments on different subnet as it will make it easy to manage and less traffic congestion.
(i hope my question is making sense?)
if i am able to access devices and peripherals across subnet through routing setup, then I am all for dividing groups/computers/departments on different subnet as it will make it easy to manage and less traffic congestion.
(i hope my question is making sense?)
ASKER
More questions: So if, for now, I expand my ip address range for 192.168.0.x /24 to 192.168.0.x /23, according to the calculator, I get a range of 192.168.0.1 - 192.168.1.254.
My question is, once all devices reach 192.168.0.1-252 (or max), does the next device automatically go to 192.168.1.xx giving me a total of 512 on a /23 subnet and will I be able to see all devices from 192.168.0.x to 192.168.1.x without adding anything in routing table?
Thanks
My question is, once all devices reach 192.168.0.1-252 (or max), does the next device automatically go to 192.168.1.xx giving me a total of 512 on a /23 subnet and will I be able to see all devices from 192.168.0.x to 192.168.1.x without adding anything in routing table?
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Great. we only have one machine at present which is Cisco router. We have no servers, etc, etc but over 300 desktop and wireless devices. So, I believe if I change the mask to /23 on my Cisco router for now, I should be good. Correct?
Yes enlarging the subnet will allow 510 devices to reach each other (one of those devices is the router used as default GW). (2 addresses / network are unusable in IPv4).
With a router you can still ping , and reach other systems... (ie your are able to reach google..., that is a routed connection, it is routed across various parties at that).
For enlarging:
You need to change the netmask on ALL devices in the network. So on the CISCO, in DHCP, and on all static systems. (AP's, routers, printers, ... etc.)
during the migration expect unavailability of some systems that are not converted to systems that are converted.
(because the broadcast address changes...).
Also expect more network load. you can expect 300+ devices ARP requests on ALL interfaces of all systems each minute. The same is true for ALL broadcast traffic. When using Windows Networking all systems will regularly publish UDP broadcasts f.e., UPNP broadcasts traffic, Multicast DNS broadcasts traffic, each system to all others in the same LAN).
(if you would have cut the network in 4 parts f.e. each sub-network would only have seen 75 ARP requests on 75 systems inside the VLAN... ).
With a router you can still ping , and reach other systems... (ie your are able to reach google..., that is a routed connection, it is routed across various parties at that).
For enlarging:
You need to change the netmask on ALL devices in the network. So on the CISCO, in DHCP, and on all static systems. (AP's, routers, printers, ... etc.)
during the migration expect unavailability of some systems that are not converted to systems that are converted.
(because the broadcast address changes...).
Also expect more network load. you can expect 300+ devices ARP requests on ALL interfaces of all systems each minute. The same is true for ALL broadcast traffic. When using Windows Networking all systems will regularly publish UDP broadcasts f.e., UPNP broadcasts traffic, Multicast DNS broadcasts traffic, each system to all others in the same LAN).
(if you would have cut the network in 4 parts f.e. each sub-network would only have seen 75 ARP requests on 75 systems inside the VLAN... ).
Given the changes you'll have to make to all of the devices with static IPs, this may be a good time to revisit how they get their addresses. With some exceptions (servers, routers, switches, etc.), my preference is to use DHCP Reservations to ensure that devices always have the same IP address. I used this primarily for network-connected printers, but consider it anywhere you are presently using a static IP address.
If you follow this approach, next time you need to make IP address changes (and you can expect there to be a "next time"!) you just make the changes to the address reservations in the DHCP server(s) and reboot devices.
If you follow this approach, next time you need to make IP address changes (and you can expect there to be a "next time"!) you just make the changes to the address reservations in the DHCP server(s) and reboot devices.
ASKER
Thanks Comp. Currently I am still trying to configure Subnet and DHCP on SonicWall. As mentioned, I am no expert on this and still struggling with the basics.
ASKER
Setting up different subnet and adding them to routes, will I be able to access and manage devices across different subnets (or just be able to ping them)?
If I can access and manage devices across different subnets, then 90% of my problem will be solved as far as organizing the network architecture.
If I can access and manage devices across different subnets, then 90% of my problem will be solved as far as organizing the network architecture.
Setting up routes should be sufficient....
Ping is an access check on the internet. It sends an ICMP echo request (aka ping) packet and the target will responds for ICMP echo response (aka pong).
That only validates there is a route. (for un firewalled networks that is sufficient to grant access).
So "ONLY" able to ping a system validates it is reachable.
With firewalled networks more elaborate filters can be setup allowing/dis-allowing specific services.
With firewalls you may need to also setup the filters.
Ping is an access check on the internet. It sends an ICMP echo request (aka ping) packet and the target will responds for ICMP echo response (aka pong).
That only validates there is a route. (for un firewalled networks that is sufficient to grant access).
So "ONLY" able to ping a system validates it is reachable.
With firewalled networks more elaborate filters can be setup allowing/dis-allowing specific services.
With firewalls you may need to also setup the filters.
ASKER
correct. I will be setting up filters. but wanted to make sure that setting up routes for different subnets is sufficient to access and manage various services and applications in different subnets from an admin computer?
It should be sufficient. (be aware of on system firewalls that the other ranges are mentioned as trusted).
ASKER
got it
ASKER
Got subnet configured on SonicWall giving me more than enough IP addresses now, in my test environment. The next is routing so that I can test if I am able to see and access devices in different subnet.
Will update soon
Will update soon
ASKER
Came to find out that I did not need routing policy configured as I am not setting up a router behind Sonicwall. Subnetting doesn't require Routing Policy, but rather Access Rules. Access rule has been setup and now I can see and administer devices on different subnet without an issue.
ASKER
All of you have been very helpful, knowledgeable, patient and descriptive. I appreciate everyone's help.
I was able to setup SonicWall the way I have been planning and you guys have been very instrumental. Thank you
I was able to setup SonicWall the way I have been planning and you guys have been very instrumental. Thank you
most important, you have a working setup.
ASKER
Thank you. Will take export config file and then tinker with other features and settings
just setup VLans for different subnets for different devices. so long as your switches support VLans and you can assign a vlan or trunk to the ports.
ASKER