Bitlocker decryption
We have few computers on which Bitlocker is running and hard drive is encrypted, but there is no key for them, is there a way to go past the screen where it ask for key? then I can decrypt it from control panel.
Is there a way to decrypt it from CMD? Can it be done through AD?
Thanks, Usman
Is there a way to decrypt it from CMD? Can it be done through AD?
Thanks, Usman
You mentioned AD so I suppose these are Domain Joined. The Domain Admin could have the right to decrypt.
ASKER
yes they are all on the domain. We can boot the computer but the first screen we see is to enter the bitlocker key, which we dont have.
Can we decrypt these computers through CMD or Active directory? or any software?
thanks.
Can we decrypt these computers through CMD or Active directory? or any software?
thanks.
No - the domain administrator does not have "rights" to decrypt - that is not how bitlocker works.
When computers are domain joined, it is good practice to store the Bitlocker recovery key against the computer object in AD.
You will need to install the bitlocker plug-in, then look at the computer object in ADUC - it will appear similar to this - the bitlocker tab only shows up if you have the bitlocker extension installed.
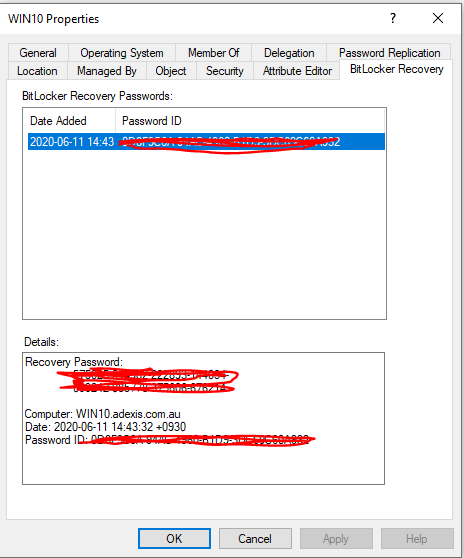
if the tab isnt there - install the extension.
if the tab shows up but there is no entry - it has not been stored in AD.
Unless you have the recovery key elsewhere (such as USB drive or written down), the data on your drive is not recoverable.
When computers are domain joined, it is good practice to store the Bitlocker recovery key against the computer object in AD.
You will need to install the bitlocker plug-in, then look at the computer object in ADUC - it will appear similar to this - the bitlocker tab only shows up if you have the bitlocker extension installed.
if the tab isnt there - install the extension.
if the tab shows up but there is no entry - it has not been stored in AD.
Unless you have the recovery key elsewhere (such as USB drive or written down), the data on your drive is not recoverable.
@Hayes
Does a Demoted User (such as a Domain User) has the right to Access such info stored in AD provided it has been set?
Does a Demoted User (such as a Domain User) has the right to Access such info stored in AD provided it has been set?
No, a regular user does not have access to the recovery key stored in AD. Domain admins have access to the keys stored in AD, and permissions to view them can be delegated to other groups.
https://theitbros.com/config-active-directory-store-bitlocker-recovery-keys/
https://theitbros.com/config-active-directory-store-bitlocker-recovery-keys/
Hence my assumption "The Domain Admin could have the right to decrypt" is correct.
ASKER
Read the page at the link I posted earlier. https://theitbros.com/config-active-directory-store-bitlocker-recovery-keys/
I includes instructions on setting a GPO to get new BitLocker deployments to store their keys in AD. It also includes steps on how to get a system that is currently running with BitLocker to store the keys in AD.
I includes instructions on setting a GPO to get new BitLocker deployments to store their keys in AD. It also includes steps on how to get a system that is currently running with BitLocker to store the keys in AD.
The computer does not boot, so it won't backup its key now, no matter what you do. Find the last admin, say "thank you".
Make yourself familiar with the Bitlocker GPOs, one of them makes the machine backup its recovery password at encryption time. For those already encrypted, use a script to backup the key, before they run into the same problem.
But to be clear: what is being asked for, a recovery password, a password or a PIN? If the recovery password is being asked for, you might be able to leave it. Else, you can only look for the person who knows the password/PIN.
Also note that it was mandatory to print or save the recovery key. It has to exist somewhere.
Make yourself familiar with the Bitlocker GPOs, one of them makes the machine backup its recovery password at encryption time. For those already encrypted, use a script to backup the key, before they run into the same problem.
But to be clear: what is being asked for, a recovery password, a password or a PIN? If the recovery password is being asked for, you might be able to leave it. Else, you can only look for the person who knows the password/PIN.
Also note that it was mandatory to print or save the recovery key. It has to exist somewhere.
the only problem with saving the recovery key is that the default location is the users documents folder which by default is on the system drive. Makes saving the recovery key there irrelevant
That's wrong, David. Try it out, the system will not allow to save on c.
You need to start the command prompt or powershell as an Administrator. Then run the following to get the key:
manage-bde -protectors c: -get
manage-bde -protectors c: -get
perhaps because my documents folder is located elsewhere led me astray when I saw the default location being the documents folder
ASKER
I am trying first to make the script work then I can look at troubleshooting the issues why its not saving the Bitlocker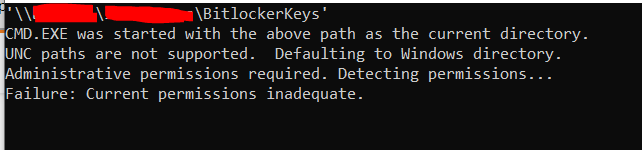 key under each computer account ID.Bitlocker batch script seems to be working fine, as it shows Bitlocker drive encryption is enabled.
key under each computer account ID.Bitlocker batch script seems to be working fine, as it shows Bitlocker drive encryption is enabled.
The recovery key for Bitlocker only runs when its run as an administrator, but when its run as a normal user, it gives an error which is attached. How can I make recovery key batch script to run through group policy as an account which has admin rights on laptops?
thanks
The recovery key for Bitlocker only runs when its run as an administrator, but when its run as a normal user, it gives an error which is attached. How can I make recovery key batch script to run through group policy as an account which has admin rights on laptops?
thanks
Run it as GPO startup script, that will use the system account.
Wait... you are showing us a command line screenshot of what?
Startup scripts run invisible, that cannot be what you show. So if that startup script fails, it will have another reason.
To find out, run the script as systerm visibly , account using
psexec -s -i script
(download psexec, first, and add a line to the end of your script that reads
pause
so that it doesn't close on its own).
Startup scripts run invisible, that cannot be what you show. So if that startup script fails, it will have another reason.
To find out, run the script as systerm visibly , account using
psexec -s -i script
(download psexec, first, and add a line to the end of your script that reads
pause
so that it doesn't close on its own).
ASKER
Administrative permissions required. Detecting permissions...
Failure: Current permissions inadequate.
Failure: Current permissions inadequate.
ASKER
'\\server\folder\BKeys'
CMD.EXE was started with the above path as the current directory.
UNC paths are not supported. Defaulting to Windows directory.
Administrative permissions required. Detecting permissions...
Failure: Current permissions inadequate.
CMD.EXE was started with the above path as the current directory.
UNC paths are not supported. Defaulting to Windows directory.
Administrative permissions required. Detecting permissions...
Failure: Current permissions inadequate.
ASKER
The batch script I am using;
manage-bde -protectors -get c: -type RecoveryPassword >"\\server\folder\BKeys\%computername%.txt"
This is not working as a startup script or Schedule task, but when I run as admin it does work.
I found the below script;
https://stackoverflow.com/questions/1894967/how-to-request-administrator-access-inside-a-batch-file
What changes I have to do to run it on windows 10 OS? would it run as a batch script or VB script and as a Schedule task?
thanks.
manage-bde -protectors -get c: -type RecoveryPassword >"\\server\folder\BKeys\%computername%.txt"
This is not working as a startup script or Schedule task, but when I run as admin it does work.
I found the below script;
https://stackoverflow.com/questions/1894967/how-to-request-administrator-access-inside-a-batch-file
What changes I have to do to run it on windows 10 OS? would it run as a batch script or VB script and as a Schedule task?
thanks.
The folder needs to be writeable for the domain group "domain computers". Make sure to grant write but no read access and your startup script and/or scheduled task, running as system account will both work
ASKER
Thanks, I tried it, still the same error.
BitLocker Drive Encryption: Configuration Tool version 10.0.19041
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
ERROR: An attempt to access a required resource was denied.
Check that you have administrative rights on the computer.
So domain computers should have write and list folder access only? any other resource group I should add for this folder? I have included the group everyone, but that didnt made any difference.
What are the resource groups which should have access for this folder? thanks.
BitLocker Drive Encryption: Configuration Tool version 10.0.19041
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
ERROR: An attempt to access a required resource was denied.
Check that you have administrative rights on the computer.
So domain computers should have write and list folder access only? any other resource group I should add for this folder? I have included the group everyone, but that didnt made any difference.
What are the resource groups which should have access for this folder? thanks.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Please correct me if i am wrong, my schedule task batch script should look like this?
@echo off
%windir%\admin\BEK manage-bde -protectors -add c: -sk \\server\BitlockerKeys\%computername% && md %windir%\admin\BEK
manage-bde -protectors -get c: -type RecoveryPassword >"\\server\BitlockerKeys\%computername%.txt"
@echo off
%windir%\admin\BEK manage-bde -protectors -add c: -sk \\server\BitlockerKeys\%computername% && md %windir%\admin\BEK
manage-bde -protectors -get c: -type RecoveryPassword >"\\server\BitlockerKeys\%computername%.txt"
You give no feedback on my comment. Obviously, you should verify permissions and compare to the icacls output above, because if they were like the above, saving the bek file would work.
Save the bek file using the script right from my article.
If you want a recovery key, save it to AD using
Save the bek file using the script right from my article.
If you want a recovery key, save it to AD using
for /f "tokens=1,2" %%a in ('manage-bde -protectors -get C: -Type recoverypassword ^| findstr ID') do manage-bde -protectors -adbackup c: -id %%bASKER
Apologies for late reply, i tried suggestions but it didnt worked.
I have decided to go with MBAM, will post separate question for it.
thanks.
I have decided to go with MBAM, will post separate question for it.
thanks.
It's hard to work with you, if you don't answer in a timely fashion. Please try to answer as soon as possible.
If you could as well provide errors instead of vague "it didn't work", we could get somewhere.
If you could as well provide errors instead of vague "it didn't work", we could get somewhere.
ASKER
ok, will try my best, if I cant see any errors, i cant report back.
i have posted question with subject;
i have posted question with subject;
"MBAM not recording keys in SQL Database"
thanks
"if I cant see any errors, i cant report back"
Ok, but the command
for /f "tokens=1,2" %%a in ('manage-bde -protectors -get C: -Type recoverypassword ^| findstr ID') do manage-bde -protectors -adbackup c: -id %%b
will wither succeed or throw an error, so what error do you see? Be aware that if you are not using this as batch file but manually, you will have to change the syntax to single %:
Ok, but the command
for /f "tokens=1,2" %%a in ('manage-bde -protectors -get C: -Type recoverypassword ^| findstr ID') do manage-bde -protectors -adbackup c: -id %%b
will wither succeed or throw an error, so what error do you see? Be aware that if you are not using this as batch file but manually, you will have to change the syntax to single %:
for /f "tokens=1,2" %a in ('manage-bde -protectors -get C: -Type recoverypassword ^| findstr ID') do manage-bde -protectors -adbackup c: -id %bASKER
I will use it as a batch file, in the group policy to execute at startup, is that ok?
Also if i use this script, i dont have to configure any specific settings under group policy for bitlocker encryption?
Also if i use this script, i dont have to configure any specific settings under group policy for bitlocker encryption?
ASKER
Recovery password will get stored under AD Bitlocker recovery tab?
Yes of course... we talked about this, see above (?)
Startup script will work, scheduled task will work. Why haven't you tried that?
Startup script will work, scheduled task will work. Why haven't you tried that?
If a Microsoft account is used for login, the key may be stored in the account.