Investigate Black-listed Exchange Server
A few days ago, our on-prem Exchange 2016 mail server was blacklisted on about 5 different RBL sites (per mxtoolbox). I reached out to all sites, and requested additional information to determine the root cause. While waiting for their response, what other steps can I perform to track down the root of this evil?
Port 25 is locked down to only allow server access. I also checked the Queue Viewer, but only saw about 21 emails in the queue.
What other steps can be performed?
Port 25 is locked down to only allow server access. I also checked the Queue Viewer, but only saw about 21 emails in the queue.
What other steps can be performed?
I would check the SPF record.
If someone is spoofing the domain, having an SPF record will help reduce that by verifying the source of the message and checking if that is allowed to send for that domain (though the verification part is configured on the receiving domain).
You create it in your public DNS as a TXT record.
https://support.dnsimple.com/articles/spf-record/
If someone is spoofing the domain, having an SPF record will help reduce that by verifying the source of the message and checking if that is allowed to send for that domain (though the verification part is configured on the receiving domain).
You create it in your public DNS as a TXT record.
https://support.dnsimple.com/articles/spf-record/
- One of your users with Outlook might have sent out spam/phishing (or through Outlook without their knowledge).
- One of your other servers has been compromised and is sending out spam/phishing mails
- Bounce misconfigured. You're sending bounce messages to honey pots.
Hope you have SMTP in and outgoing logs on, because you'll need it to trace back what happened when your receive info back from all those black list maintainers.
- One of your other servers has been compromised and is sending out spam/phishing mails
- Bounce misconfigured. You're sending bounce messages to honey pots.
Hope you have SMTP in and outgoing logs on, because you'll need it to trace back what happened when your receive info back from all those black list maintainers.
ASKER
@Seth - I have two entries in the SPF record, 1 for the www server, and the other for the mail server. The MX record for the domain points to the mail server. The www server sends mail from itself, and does not use the mail server as a relay. However, let me as a question. If the www server is compromised, and is sending spam email, will the mail server get flagged since it's identified in the MX record, or would the www server get black listed instead?
@Kimputer - Where do I go to analyze the logs? Should I focus on the outgoing logs, or focus on the receiving logs as well? Any idea what I should be looking for? Does exchange have any statistics tools that I could use to identify how many emails are sent out per mailbox on a daily/weekly basis?
@Kimputer - Where do I go to analyze the logs? Should I focus on the outgoing logs, or focus on the receiving logs as well? Any idea what I should be looking for? Does exchange have any statistics tools that I could use to identify how many emails are sent out per mailbox on a daily/weekly basis?
it is possible that the domain could be blacklisted if your web server is sending out crap
a blacklist entry would be for your domain, not for a specific server that is sending it
a blacklist entry would be for your domain, not for a specific server that is sending it
ASKER
Seth, how does one determine the trigger source of a blacklist? I tried reaching out to various DNSBL sites, but so far, the only information I received is the following:
The only thing I was able to ascertain from this information is that the blacklist is still active as of the 19th, unless you see something that I overlooked??
Also, we have one user that is forwarding all of their email from their mailbox to a gmail account. Could google be viewing this as a relay action? If too many spam emails are forwarded to the gmail account, could google blacklist the server?
./traceforIP x.x.x.x
0003B67A.transcript.xml:<gbu time='20210619070330' ip='x.x.x.x' t='Ugly' b='1' g='0'/>
0003B67A.transcript.xml:<gbu time='20210619070333' ip='x.x.x.x' t='Ugly' b='15' g='0'/>
0003B67A.transcript.xml:<gbu time='20210619070330' ip='x.x.x.x' t='Ugly' b='1' g='0'/>
0003B67A.transcript.xml:<gbu time='20210619070333' ip='x.x.x.x' t='Ugly' b='15' g='0'/>The only thing I was able to ascertain from this information is that the blacklist is still active as of the 19th, unless you see something that I overlooked??
Also, we have one user that is forwarding all of their email from their mailbox to a gmail account. Could google be viewing this as a relay action? If too many spam emails are forwarded to the gmail account, could google blacklist the server?
Did you check in mxtoolbox?
https://mxtoolbox.com/blacklists.aspx
https://mxtoolbox.com/blacklists.aspx
ASKER
@MAS - That was my default response. Once we received the first rejection email, I checked mxtoolbox and saw that the IP was flagged on 4 other sites as well. Again, detecting the problem was easy, but finding the root cause it proving to be extremely difficult.
Please enable protocol logging on connectors so you will see what is happening and from where it is coming. i.e. the source of the email.
https://docs.microsoft.com/en-us/exchange/mail-flow/connectors/configure-protocol-logging?view=exchserver-2019
https://docs.microsoft.com/en-us/exchange/mail-flow/connectors/configure-protocol-logging?view=exchserver-2019
You should also go to each blacklist through their official URL and do a lookup. Because during those steps, you get to see the exact reason (usually the headers of the offending emails, or at least a timestamp). Along with your SMTP logs, you may be able to trace the origin of the problem.
ASKER
@MAS - It looks like protocol logging is already enabled for all connectors except Receive HubTransport, and Receive Client Frontened Transport.
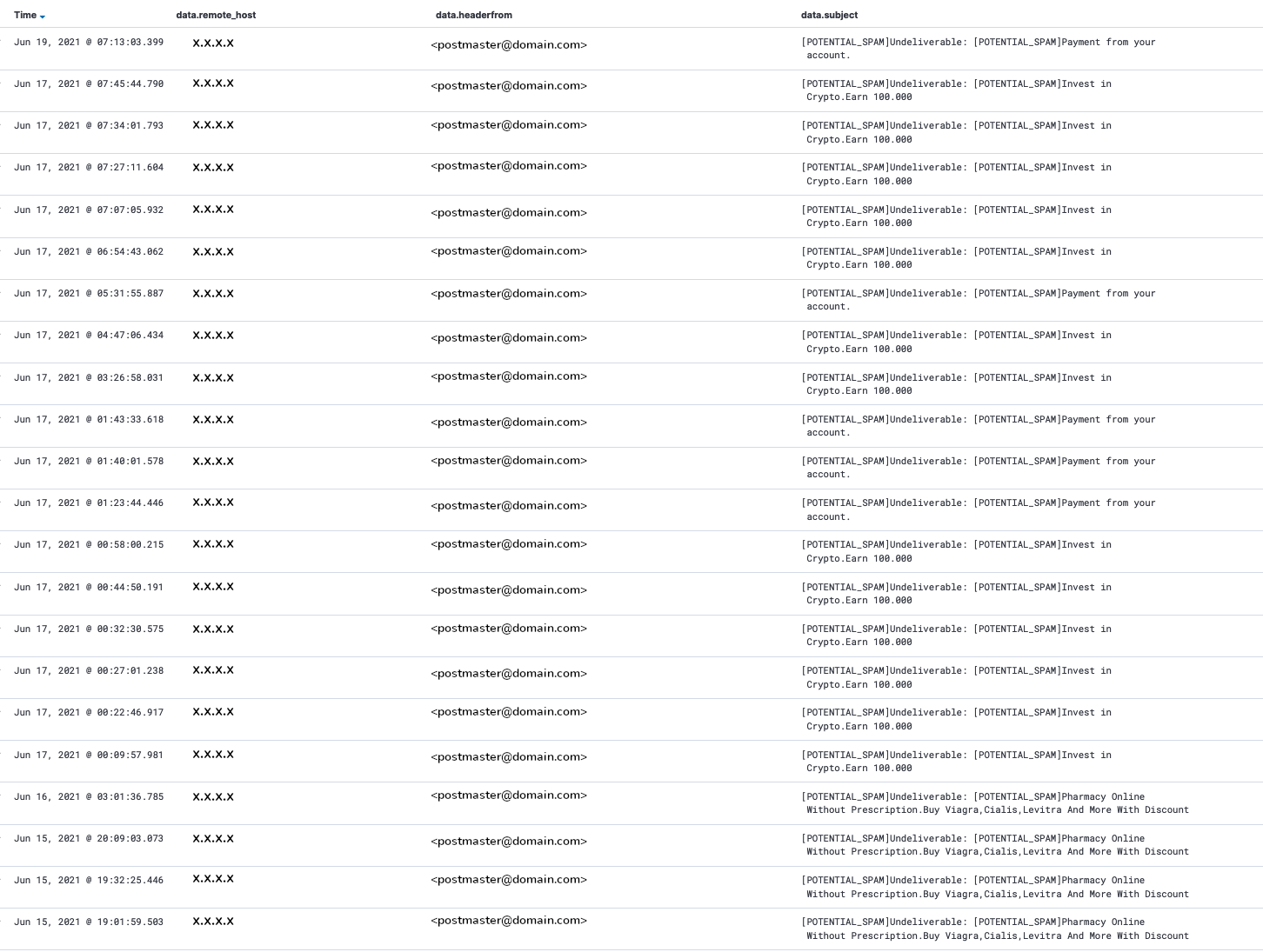
@Kimputer - I did reach out to the blacklist sites directly, but did not get any valuable information. However, anubisnetworks just sent me a screenshot this morning, showing that this was a SPAM rejection issue (I attached the image, but masked the IP / domain information).
Our spam program that runs on the mail server will alter the Subject of the email to include the prefix [POTENTIAL_SPAM] before delivering the email to the mailbox. Based on the screenshot, I think this is what happened (please correct me if I'm wrong):
1) The mail server received the email.
2) SPAM program flagged it as SPAM and altered the Subject with [POTENTIAL_SPAM] and releases it for delivery
3) The mail server sees that targeted mailbox does not exist
4) The mail server tries to send the email back to the source, based on the From field
5) The From field is spoofed, so some are returned to random mailboxes, and others are rejected and sent back to postmaster.
6) SPAM program flagged it as SPAM and altered the Subject a second time with [POTENTIAL_SPAM] and releases it for delivery
If this seems accurate, is there a way to redirect flagged spam to a junk mailbox in order to prevent this email bouncing to occur and thus black list the server? In the meantime, I will try to cross reference the Subject and dates with the logs on the server to see if I can extrapolate any additional information
@Kimputer - I did reach out to the blacklist sites directly, but did not get any valuable information. However, anubisnetworks just sent me a screenshot this morning, showing that this was a SPAM rejection issue (I attached the image, but masked the IP / domain information).
Our spam program that runs on the mail server will alter the Subject of the email to include the prefix [POTENTIAL_SPAM] before delivering the email to the mailbox. Based on the screenshot, I think this is what happened (please correct me if I'm wrong):
1) The mail server received the email.
2) SPAM program flagged it as SPAM and altered the Subject with [POTENTIAL_SPAM] and releases it for delivery
3) The mail server sees that targeted mailbox does not exist
4) The mail server tries to send the email back to the source, based on the From field
5) The From field is spoofed, so some are returned to random mailboxes, and others are rejected and sent back to postmaster.
6) SPAM program flagged it as SPAM and altered the Subject a second time with [POTENTIAL_SPAM] and releases it for delivery
If this seems accurate, is there a way to redirect flagged spam to a junk mailbox in order to prevent this email bouncing to occur and thus black list the server? In the meantime, I will try to cross reference the Subject and dates with the logs on the server to see if I can extrapolate any additional information

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
@Kimputer - We use Bitdefender Gravityzone to provide Exchange protection. I reached out to them for suggestions with this issue. However, in the meantime, I enabled the builtin Exchange anti-spam, along with recipient validation on all external mail:
Unless you suggest any additional steps to further prevent the backscattering, I will wait to see if this helps to prevent future incidents.
[PS] C:\Windows\system32>Get-RecipientFilterConfig | Format-List Enabled
Enabled : True
[PS] C:\Windows\system32>Get-RecipientFilterConfig | Format-List RecipientValidationEnabled
RecipientValidationEnabled : True
[PS] C:\Windows\system32>Get-RecipientFilterConfig | Format-List ExternalMailEnabled
ExternalMailEnabled : TrueUnless you suggest any additional steps to further prevent the backscattering, I will wait to see if this helps to prevent future incidents.
ASKER
My mail server has been removed from all blacklisting sites. Sorbs did suggest that I update the mail server config so that any NDRs do not quote the original message. Can anyone point me to an article that describes how to do that with Exchange 2016?
Hi Robet,
This has turned into a new question.
Appreciate if you close and ask a new question. We will be more than happy to answer and you get better response.
Rgds
MAS
This has turned into a new question.
Appreciate if you close and ask a new question. We will be more than happy to answer and you get better response.
Rgds
MAS
Check for any virus infection on server.
If possible try to do an outbound filtering if you have a good 3rd party spam filter in place. so you are covered for the time being.
Then change your current IP to a different IP to resume your mail flow.
Configure a policy in your firewall to block all port 25 traffics except from Exchange server.