Best practice: hide machines in "Network Neighborhood" in (File Explorer) ??
Presently, in file explorer, expanding "Network" will show all the desktops will show all the desktops in that office location (NY desktops in NY office, Miami desktops in Miami office).
I presume that's because there's some "discovery" network setting.
Is there any reason why it's good to have the desktops visible?
if not, what's the easiest way to stop them from showing up?
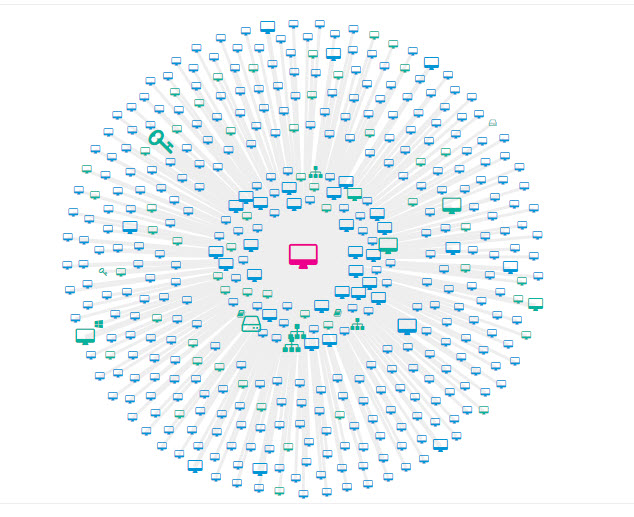
We use Cisco Stealthwatch and after seeing this connections graphic of all the machines talking to each other, I became concerned:
I presume that's because there's some "discovery" network setting.
Is there any reason why it's good to have the desktops visible?
if not, what's the easiest way to stop them from showing up?
We use Cisco Stealthwatch and after seeing this connections graphic of all the machines talking to each other, I became concerned:

ASKER
Thanks for the link on how to deploy changes to the network discovery setting.
I'm really trying to decide if I want to fuss with it by turning it off in some vague attempt to improve security.
I'm sure there's a bunch of things I'm not considering if I disable it. For example, could a user in a conference room Remote Desktop to his personal desktop in the office (or a different office)?
Regards,
Mike
I'm really trying to decide if I want to fuss with it by turning it off in some vague attempt to improve security.
I'm sure there's a bunch of things I'm not considering if I disable it. For example, could a user in a conference room Remote Desktop to his personal desktop in the office (or a different office)?
Regards,
Mike
We leave it off on Remote Desktop Session Hosts.
We don't enable it by default in all desktops that get deployed either. The user can choose to do so though it doesn't happen often.
It has to be enabled either by the user or via Group Policy that in turn allows the machine to be shown in the Network Neighbourhood.
We don't enable it by default in all desktops that get deployed either. The user can choose to do so though it doesn't happen often.
It has to be enabled either by the user or via Group Policy that in turn allows the machine to be shown in the Network Neighbourhood.
ASKER
If you can still Remote Desktop to a pc even if its discovery is disabled, I can't think of a compelling reason to enable it.
Can you Philip?
Thx
Mike
Can you Philip?
Thx
Mike
Security by Obscurity is never really security, but that being said, we don't enable it by default and tie that in to the Windows Firewall being set up via Group Policy to further limit the threat window on user and server endpoints.
EDIT: And direct to your question, no. Users get mapped drives for their network resources.
EDIT: And direct to your question, no. Users get mapped drives for their network resources.
I have used every version of Microsoft desktop OS since Windows 3.1. I don't even remember how to access what used to be called Network Neighborhood anymore. I don't want my users browsing. Workstations are on a separate subnet from servers. I don't want my users to know the names of servers, or to browse to them. I hide all shares anyway. Network browsing isn't needed for RDP, or even to connect to files shares or printers.
When people complain that they can't see all of the machines, I tell them to stop trying to access the network like it is the 1990s.
When people complain that they can't see all of the machines, I tell them to stop trying to access the network like it is the 1990s.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I hide shares because I don't want anyone to know or care about where the share is located. All access is through DFS Namespace. It reduces that chance that someone will link directly to a real share.
ASKER
I used the term "Network Neighborhood" to communicate the Network section in file explorer; I felt Network was too generic of a term :-)
BTW, even with DFS, aren't the \\server\c$ etc. shares still one password away from being accessed? (assuming default user=administrator ?
BTW, even with DFS, aren't the \\server\c$ etc. shares still one password away from being accessed? (assuming default user=administrator ?
Nothing being discussed impacts the fundamental Windows security model and security of network shares.
Yes, all shares are still just a Kerberos ticket away.
Yes, all shares are still just a Kerberos ticket away.
The fact that network discovery is turned off, does not prevent anyone from reaching a network PC, if they know its name. Just type \\PCName01 into file explorer address line and you see all its shared resources. So eliminating the discovery just de clutters the network tab and prevents folks from poking around indiscriminately. Its up to the target PCs to secure their resources. Windows does a decent job of that, but any user (admin level) can share out a folder tree that can be accessed by others on the same network -- regardless of if discovery is turned on. .
ASKER
Very true.
Getting back to the JPG in my original post, I don't know if these connections are made possible by network discovery, or if it's just pinging around indiscriminately on the same subnet.
Aside from the graphic reminding me of covid-19, I'm not a fan of what that represents :-)
Getting back to the JPG in my original post, I don't know if these connections are made possible by network discovery, or if it's just pinging around indiscriminately on the same subnet.
Aside from the graphic reminding me of covid-19, I'm not a fan of what that represents :-)
I believe Cisco would not use MS network discovery.
Do the clients have Cisco software on them?
Aside Yes much a covid looking hopefully not a variant...
Do the clients have Cisco software on them?
Aside Yes much a covid looking hopefully not a variant...
The original graphic doesn't convey any meaning to me.
Yep, striking similarity :)
We enable the Windows Firewall for all three profiles with logging and pop-up for new protocols via Group Policy at all client sites.
By default logging is set to log DROP not an accept. You can enable it to do so to get a good view of what's going on.
AFAIK, the default for Windows Firewall is to respond to ICMP (PING) on the same subnet while configured with the Domain/Private profiles.
If you don't like that, then hammer down ICMP to your PAW/Management Jump Server(s) and domain controllers. That's it.
By default logging is set to log DROP not an accept. You can enable it to do so to get a good view of what's going on.
AFAIK, the default for Windows Firewall is to respond to ICMP (PING) on the same subnet while configured with the Domain/Private profiles.
If you don't like that, then hammer down ICMP to your PAW/Management Jump Server(s) and domain controllers. That's it.
ASKER
Yes @65td, the clients have Cisco Umbrella Client (fancy DNS protection).
I'm not sure if the Umbrella client would be reaching out to others on the same subnet; it's basically fancy DNS protection.
Cisco Stealthwatch monitors connections . The graphic represents data exchanged between the center computer and other machines. The bigger the machine, the more data. I can't imaging it would be DNS related.
I'm not sure if the Umbrella client would be reaching out to others on the same subnet; it's basically fancy DNS protection.
Cisco Stealthwatch monitors connections . The graphic represents data exchanged between the center computer and other machines. The bigger the machine, the more data. I can't imaging it would be DNS related.
ASKER
Thanks everyone for the replies.
What is proper Expert's Exchange etiquette in a situation like this where pretty much everyone agrees, and offered a slightly different take.
Am I supposed to split points across everyone?
What is proper Expert's Exchange etiquette in a situation like this where pretty much everyone agrees, and offered a slightly different take.
Am I supposed to split points across everyone?
Its to split it among those with good replies.
ASKER
Thanks everyone!
https://www.technig.com/enable-network-discovery-via-group-policy/