Cisco Firepower / Aruba InstantOn 1930 Networking issue.
I have a HP Aruba 1930 InstantOn L3 switch that i use for routing; in addition, i use a Cisco 1010 FTD for my edge. I have 3 interfaces in use on the Cisco; outside for wan, inside for lan, and inside_3 for voice. I have one static route set to obtain internet connectivity. At this point, i have an inside->outside any->any rule to allow all traffic for troubleshooting. I'm still unable to get out to the internet on the inside_3 interface.
ASKER
Yes, i do have a rule for inside_3 to reach the internet. Additionally, i do have static NAT/PAT rules as well.
Do clients on the inside_3 subnet use the L3 switch as their default gateway, or the FTD?
ASKER
The L3 switch
Ok, do you have a routed link between the FTD and the L3 switch, or does the FTD have an IP in the same subnet as the switch on the inside_3 VLAN?
ASKER
There is a routed link between the switch and the FTD...there currently two inside interfaces, one is for data, and one is for voice...the data interface is fine, however, we are unable to get to the internet viabthe voice interface.
Ok, not sure I completely understand your topology.
If there is a routed interface via the FTD why do you have two interfaces? Usually you'd have either an interface for each VLAN straight from the firewall and clients would use the firewall as their default gateway, or you'd have a separate routed interface from the FTD that terminates at the L3 switch and the clients would use the L3 switch as their default gateway on two separate SVIs.
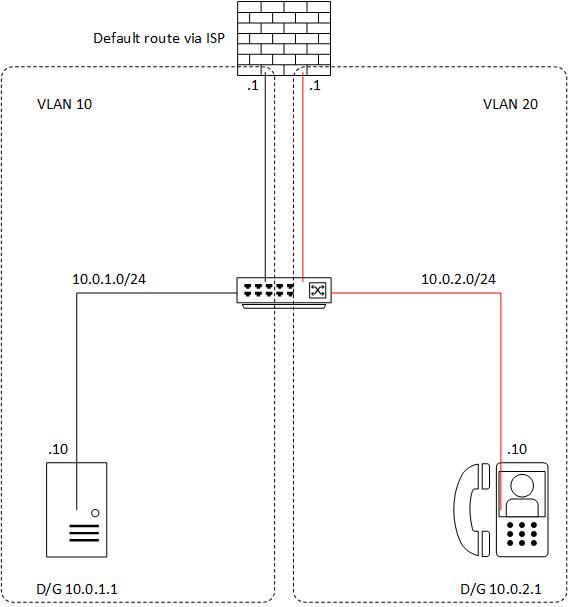
Here's a basic diagram showing the FTD as the default gateway for both VLANs. This is ok if there are no other VLANs at the L3 switch that need to be routed.
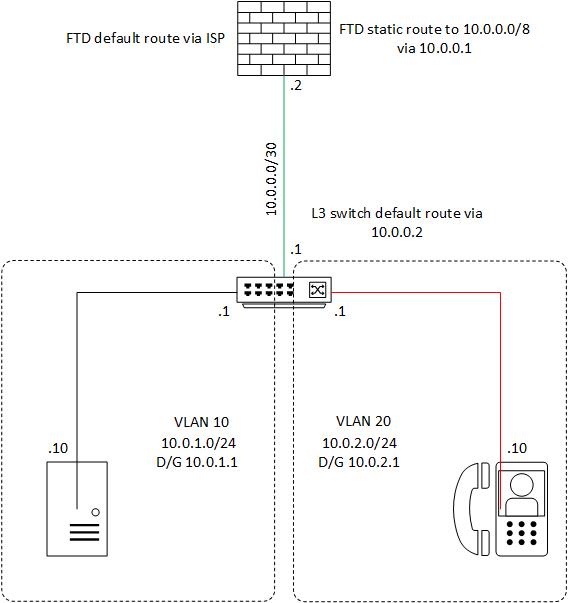
Here's an example of a routed link to the FTD, using the L3 switch to route traffic for both VLANs...
Which way do you have it?
If there is a routed interface via the FTD why do you have two interfaces? Usually you'd have either an interface for each VLAN straight from the firewall and clients would use the firewall as their default gateway, or you'd have a separate routed interface from the FTD that terminates at the L3 switch and the clients would use the L3 switch as their default gateway on two separate SVIs.
Here's a basic diagram showing the FTD as the default gateway for both VLANs. This is ok if there are no other VLANs at the L3 switch that need to be routed.

Here's an example of a routed link to the FTD, using the L3 switch to route traffic for both VLANs...

Which way do you have it?
ASKER
My apologies for the delay, i'm using the second scenario:
I have a routed link between the FTD and Aruba; i have 2 VLANs on the Aruba:
FTD int = 10.20.32.2
10.20.32.254 = vlan 1
10.20.33.254 = vlan 10
i can browse the internet without an issue on vlan 1, but not vlan 10. The routing table is as follows:
0.0.0.0/0 10.20.32.2
10.20.32.0/24 directly connected, vlan 1
10.20.33.0/24 directly connected, vlan 10
There is one routed link from switchport #1 to FTD port 2
I have a routed link between the FTD and Aruba; i have 2 VLANs on the Aruba:
FTD int = 10.20.32.2
10.20.32.254 = vlan 1
10.20.33.254 = vlan 10
i can browse the internet without an issue on vlan 1, but not vlan 10. The routing table is as follows:
0.0.0.0/0 10.20.32.2
10.20.32.0/24 directly connected, vlan 1
10.20.33.0/24 directly connected, vlan 10
There is one routed link from switchport #1 to FTD port 2
No problem.
So you don't exactly have a routed link between the switch and the firewall. You have the firewall on VLAN1, which is the same VLAN as clients on the inside interface. A proper routed link would be as per my 2nd diagram. Notice the link between switch and firewall is not actually a VLAN.
You have two options here. Either:
1. Add a static route on the firewall to enable it to reach VLAN 10... 10.20.33.0/24 via 10.20.32.254
2. Create a dedicated link between the switch and firewall on a completely different VLAN (or use a proper routed link using an IP on an actual switch interface) and add routes pointing back at the switch for the two VLANs.
So you don't exactly have a routed link between the switch and the firewall. You have the firewall on VLAN1, which is the same VLAN as clients on the inside interface. A proper routed link would be as per my 2nd diagram. Notice the link between switch and firewall is not actually a VLAN.
You have two options here. Either:
1. Add a static route on the firewall to enable it to reach VLAN 10... 10.20.33.0/24 via 10.20.32.254
2. Create a dedicated link between the switch and firewall on a completely different VLAN (or use a proper routed link using an IP on an actual switch interface) and add routes pointing back at the switch for the two VLANs.
ASKER
Understood, option 1 is preferable...i'm configuring that route now. I'll update you shortly.
ASKER
I input the following static route on the FTD...

Looks good. Let me know what happens when it eventually deploys :-)
ASKER
Still no internet access from 10.20.33.0 subnet...
i can ping both vlan IPs when connected to the 10.20.32.0 network, but not when connected to the 10.20.33.0 network...see switch config below:
User Name:
Password:**************
Metro-SG250x#sh run
config-file-header
Metro-SG250x
v2.5.7.85 / RCBS3.1_930_871_059
CLI v1.0
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
!
unit-type-control-start
unit-type unit 1 network gi uplink te
unit-type-control-end
!
vlan database
vlan 10
exit
voice vlan id 10
voice vlan vpt 6
voice vlan oui-table add 0001e3 Siemens_AG_phone
voice vlan oui-table add 00036b Cisco_phone
voice vlan oui-table add 00096e Avaya
voice vlan oui-table add 000fe2 H3C_Aolynk
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone
voice vlan oui-table add 00e075 Polycom/Veritel_phone
voice vlan oui-table add 00e0bb 3Com_phone
voice vlan oui-table add 08000f Mitel
ip dhcp relay address 10.20.32.21
ip dhcp relay enable
bonjour interface range vlan 1
hostname Metro-SG250x
username **** password encrypted **** privilege 15
ip ssh password-auth
ip ssh-client username ****
encrypted ip ssh-client password ****
ip ssh-client server authentication
snmp-server location ****
snmp-server contact ****
ip name-server 10.20.32.21
ip telnet server
!
interface vlan 1
name Data
ip address 10.20.32.254 255.255.255.0
no ip address dhcp
!
interface vlan 10
name Voice
ip address 10.20.33.254 255.255.255.0
ip dhcp relay enable
!
interface GigabitEthernet2
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet3
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet4
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet5
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet6
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet7
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet8
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet9
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet10
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet11
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet12
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet13
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet14
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet15
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet16
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet17
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet18
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet19
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet20
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet21
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet22
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet23
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet24
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
switchport access vlan 10
!
exit
ip default-gateway 10.20.32.2
i can ping both vlan IPs when connected to the 10.20.32.0 network, but not when connected to the 10.20.33.0 network...see switch config below:
User Name:
Password:**************
Metro-SG250x#sh run
config-file-header
Metro-SG250x
v2.5.7.85 / RCBS3.1_930_871_059
CLI v1.0
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
!
unit-type-control-start
unit-type unit 1 network gi uplink te
unit-type-control-end
!
vlan database
vlan 10
exit
voice vlan id 10
voice vlan vpt 6
voice vlan oui-table add 0001e3 Siemens_AG_phone
voice vlan oui-table add 00036b Cisco_phone
voice vlan oui-table add 00096e Avaya
voice vlan oui-table add 000fe2 H3C_Aolynk
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone
voice vlan oui-table add 00e075 Polycom/Veritel_phone
voice vlan oui-table add 00e0bb 3Com_phone
voice vlan oui-table add 08000f Mitel
ip dhcp relay address 10.20.32.21
ip dhcp relay enable
bonjour interface range vlan 1
hostname Metro-SG250x
username **** password encrypted **** privilege 15
ip ssh password-auth
ip ssh-client username ****
encrypted ip ssh-client password ****
ip ssh-client server authentication
snmp-server location ****
snmp-server contact ****
ip name-server 10.20.32.21
ip telnet server
!
interface vlan 1
name Data
ip address 10.20.32.254 255.255.255.0
no ip address dhcp
!
interface vlan 10
name Voice
ip address 10.20.33.254 255.255.255.0
ip dhcp relay enable
!
interface GigabitEthernet2
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet3
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet4
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet5
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet6
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet7
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet8
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet9
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet10
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet11
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet12
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet13
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet14
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet15
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet16
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet17
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet18
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet19
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet20
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet21
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet22
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet23
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
!
interface GigabitEthernet24
switchport mode general
switchport general allowed vlan add 10 tagged
switchport general allowed vlan add 1 untagged
switchport access vlan 10
!
exit
ip default-gateway 10.20.32.2
Are you wanting to firewall access between VLAN 1 and VLAN 10? If not, disable the inside_3 interface at the firewall and try again.
ASKER
At this point, I'm just trying to get to the internet from the 10.20.33.0 subnet...I'm not understanding why 10.20.32.0 with a 10.20.32.254 gateway can get out to the internet, but the 10.20.33.0 network with a 10.20.33.254 gateway can't...I'm wanting the switch to handle all of the routing, with the firewall simply serving as a hop in this scenario
ASKER
Also, the inside_3 interface has been disabled to no avail.
ASKER
Also, i can ping both VLAN IPs from the firewall...so it appears to be a switch routing issue...please advise.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Just to confirm, should i replace my existing link to the firewall?
FTD Port 2 -> Switchport 1 (VLAN 1 10.20.32.254) [Link 1]
existing link
FTD Port 3 -> Switchport 24 (VLAN 10 10.20.33.254) [Link 2]
new link
Also, if i leave both links in place, do the following static entries on the firewall make sense? I'm curious as to why i need to use the new link instead of the existing one...
10.20.32.0/24 via 10.20.32.254 (link1)
10.20.33.0/24 via 10.20.33.254 (link 2)
FTD Port 2 -> Switchport 1 (VLAN 1 10.20.32.254) [Link 1]
existing link
FTD Port 3 -> Switchport 24 (VLAN 10 10.20.33.254) [Link 2]
new link
Also, if i leave both links in place, do the following static entries on the firewall make sense? I'm curious as to why i need to use the new link instead of the existing one...
10.20.32.0/24 via 10.20.32.254 (link1)
10.20.33.0/24 via 10.20.33.254 (link 2)
If you want to use the switch as the router, yes you need to replace the existing link to the firewall. You only need one link and it shouldn't be on VLAN 1 or VLAN 10, as per my last response.
If you leave both links in place, the firewall should do the routing, not the switch. This means you should use the firewall's IP as the default gateway for all devices, so clients in VLAN 1 use 10.20.32.2 as their gateway and clients in VLAN 10 use 10.20.33.2 as their gateway.
If you leave both links in place, the firewall should do the routing, not the switch. This means you should use the firewall's IP as the default gateway for all devices, so clients in VLAN 1 use 10.20.32.2 as their gateway and clients in VLAN 10 use 10.20.33.2 as their gateway.
ASKER
Thank you sir!
Have you configured NAT overload for the traffic coming from the inside_3 interface?