Lost Network Connections to File Server and NAS After SonicWall Firewall Installation
Hi,
I recently installed a SonicWall TZ270 Firewall in my home office environment. I have four different "zones" set up. The work zone has my main work PC, a Windows 2012 file server, a NAS device, and a network printer in it. I am having several problems with mapped networked drives that just started after installing the SonicWall and may be due to its configurations and policies.
First, I have three mapped drives on my Windows 2012 Server: G-drive, L-drive, and O-drive. When I boot up my work PC and open explorer all three drives have a red X through them and the following error message:
An error occurred while reconnecting G to \\myserver\G-drive
Microsoft Windows Network: The local device name is already in use. The connection has not been restored.
I tried disconnecting the drive and remapping to no avail. I am having issues accessing my Sonic Firewall (see other question), but am pretty sure I did not set up any policies allowing or blocking any Work zone to Work zone services.
I am also having problems mapping my NAS drives. I have four different drives on my NAS mapped on my work PC. I recently upgraded my work desktop from Windows 7 to Windows 10. After the upgrade, I needed to manually map each drive when I booted my work desktop. I posted a question about this in June and followed advice from arnold and solved this with a bat file that runs on startup and got around this by writing a I have a small bat file on startup that contains:
@echo off
net use [drive[: /delete
net use [drive]: \nas\sharename /persistent:no
Everything worked fine until the TZ270 firewall was installed. Now when the cmd window opens it asks me to enter my username and password for each of the four network drives every time after boot up.
1. Is all of this because the 270 is blocking some service(s) between different computers on the same Work Network?
2. If yes, which services should I create a policy for to allow Work to Work communication?
3. If not, how do I solve these problems?
Thank you!
ASKER
Each ethernet port on the TZ270 firewall is in fact assigned a different zone. And none of the zones should be able to talk to each other in any way. My problem is with devices in the same zone. The firewall ethernet port that is assigned to "Work" is connected to a Dell unmanaged switch that is then connected to all of the devices. The server, desktop, NAS and printer are all using static IP on this one network. Do I need to create rules for allowing services in the same zone? For example, allow DNS between Work and Work? If so, what services do I need to allow?
ASKER
Does my problem sound like something caused by my firewall or could it be something on my server? I checked the server and all the AD services are running. However, when I look at my NIC on my work PC it is saying I am connected to "Network 3, a private network". It is not showing my domain name. When I am logged into the server and looking at its NIC, it says it is connected to MyDomain.local. Does this help diagnose the problem?
Even though all the services are running, would it be worth the try to restart my file server in an effort to resolve this AD/DNS issue?
ASKER
Normally when I've seen this I've had to unregister the PC from the domain, clear all DNS records from the DC, and then rejoin the domain.
That makes some sense to me. What do you think? How do I do this exactly?
Enable smbv1 on the Windows 10 as described in the link, if your nas does not gave an option to enable smbv1 support.
The problem, you made many changes to what you have, drive mappings for a user are within the user profile.
Disjoining the system from a domain does not alter user profile settings as you will be reading it on rejoin, unless you rename the user's folder.
My understanding you have one zone on the sonicwall feeding an unmanaged switch to which all your devices are connected, correct?
The wife's and son's internet access is going through the other interfaces. Correct?
But the operation of the office, relies on these servers?
As the user, regedit hkey_current_user\softwate
I think it is under this or the Windows nt stracture of the same path.
What you are looking for is mountpoint2 key where the mapped drives/UNC mappings are.
Misread/misinterpreted your disjoin/rejoin related question. Post reared.
The server setup is shielded from accessing the Internet?
Confirm IP on the workstation does it use DHCP to get an ip or is it static as well?
Deals with whether it has a path to the IPS of the server/Nas.
The domain designation on the network is Aitomatic, discovery when a domain based system boots and looks to locate the DC to process GPO that is when it determines whether it is domain based, or determines classification public or work/private.
Work/private even public will not interfere with traffic outgoing from the workstation to access server, or nas.
A quick fix to try, set a static ip on the workstation in the same range as the one on the server and see if access is restored.
What do you get when you run
Nslookup -q=SRV _ldap._tcp.dc._msdcs.mydom
Do you get your server as a response?
You could look through the ARP table on the sonicwall to determine which zone this PC is in versus where the server is. And then setup the inter zone access rule.
I.e. Allow the PC to access the other zone by specific rules ....
Often, when the workstation is booted before a DC is available it would fall into a classification commonly public, but when manually changing classification, the option is provided to make the new choice the default when connecting to hew networks.
Can you bring the ssg5 back?
Not sure the significance of the port speed limit on the ns5.
Depending on what you have, the 100 MB connection to the internet should be sufficient the internal communication will be at the switch level, direct communication between servers, nas, and computer if they are within the same zone.
100MB limit will not impact anything since (if I remember your question) you do not have any inter zone communication.
depending on what your upstream feed is, reconnecting the NS5 as it was provided the sonicwall has been configured to use the prior IP ranges.
if the upstream can have two ethernet ports, the ssg5 and the sonicwall can both be connected to the upstream feed.
then you can work with both connected, the Wife's and Son's feeds can be left on the sonicwall, while the rest reestablished, and reworked.
ASKER
You gave me a lot of info to absorb. I will be looking at this and posting some questions and follow-up in the next 6 hours or so. Thank you!
ASKER
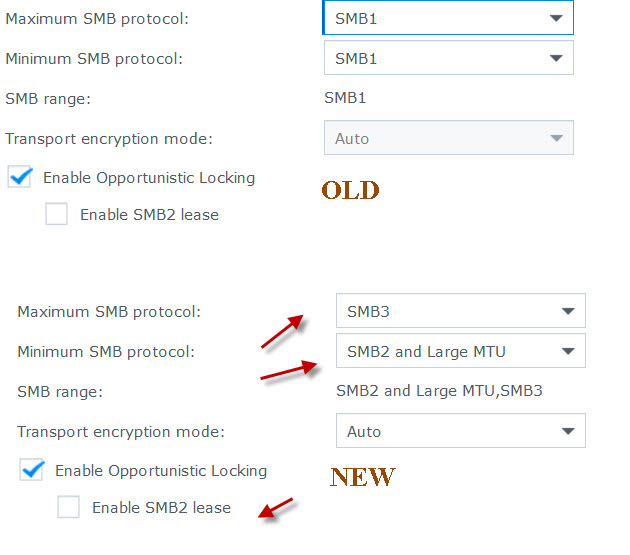 Note Enable Opportunistic Locking was previously checked. Now that I am accepting SMB2, should the "Enable SMB2 lease" box also be checked?
Note Enable Opportunistic Locking was previously checked. Now that I am accepting SMB2, should the "Enable SMB2 lease" box also be checked?I also modified my W10 desktop by turning off SMB 1.0/CIFS Automatic Renewal and SMB 1.0/CIFS Client. Here is a pic of how my W10 desktop is now configured.
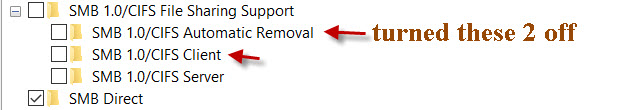 Since these two changes, I noticed some improvement. When I reboot I still do not see my server of NAS drives. When I go to map the first server drive, I need to enter my username and password for the domain. Once I do that for the first server drive, I can now map the other two drives without entering my credentials. The same thing is true for the three NAS-mapped drives. I enter my domain username and password for the first mapped NAS drive and it remembers it for the other two mapped drives.
Since these two changes, I noticed some improvement. When I reboot I still do not see my server of NAS drives. When I go to map the first server drive, I need to enter my username and password for the domain. Once I do that for the first server drive, I can now map the other two drives without entering my credentials. The same thing is true for the three NAS-mapped drives. I enter my domain username and password for the first mapped NAS drive and it remembers it for the other two mapped drives.I am now going to move on to try and figure out why it cannot remember my credentials in the first place. I think the key reason is that the PC cannot contact the domain controller to authenticate the request.
Something makes the auto detection of the LAN whether it is as you not inability to talk to the DC.......
Not sure about large MTU, minimum option should be minimal.
Smbv2 lease, not sure test with both modes. Lease suggests it will add overhead to periodically refresh the connection/access
ASKER
Post the next question here after you open it.
I'll take a look if possible, or know the subject ....