Is is best practice to use the same IP gateway on multiple virtual NICs?
I have multiple vlans, and I have a windows DHCP server with multiple scopes for the different vlans. I am trying to configure the DHCP server to hand out IPs for devices on the different scopes, but not sure what the best way would be to configure the server.
Running windows server 2019, it's a VM. I have added multiple virtual NICs, and then assigned IP addresses in each space for example:
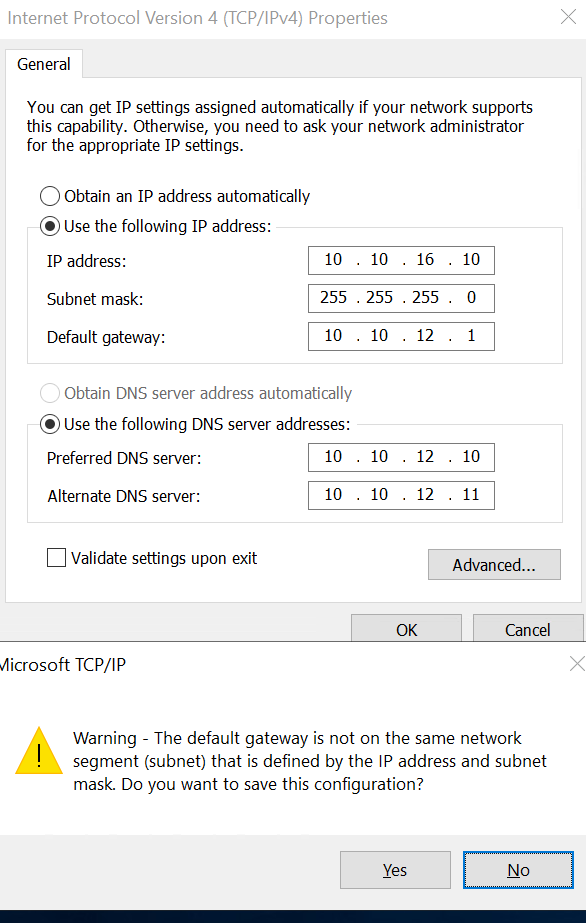
10.10.16.10 (IP)
255.255.255.0 (Mask)
10.10.16.1 (gateway)
That didn't work, no internet access and couldn't ping the IP from another device.
I then removed the gateway, and still didn't work.
I tried to add a team NIC and that failed as well.
Now, I added the gateway of my DHCP server, which is 10.10.12.1 and now that works, I can ping that specific IP from another device. So can I use the same gateway as the server for all my other NICs, as I keep on getting this error message, but not sure if that's going to cause issues on my network?
Each VLAN we set up gets its own gateway and routing rule set (we use SonicWALL devices here).
Once we set up the VLAN, it's zone, and the rules things just work ... so long as the VM is tagged with the correct VLAN tag, the switch ports are trunked and tagged VLANs are in place on each port, and the path(s) from those ports to the edge have the correct trunk and VLAN tags set up.
ASKER
The VM on host server is also set to trunk mode, it passes all vlans.
I guess I'm just struggling how to configure windows to allow or accept traffic on all the different networks, as my switch and host server is passing all traffic.
Each NIC will handle the subnet it is configured for on the VLAN it is tagged on. That works without any routing whatsoever because it is all layer 2.
Your "default gateway" is exactly that. You only need one because that is where packets get forwarded if there is no matching subnet in the routing table (such as no NIC on that subnet.) The NIC that you want to use for internet or other private subnets that don't have their own NIC (virtual or physical) should be the ONLY one with a default gateway.
If you need to reach the internet on one NIC, but reach a remote subnet on a totally different NIC, static routes are the appropriate solution. Multiple default gateways are NOT.
We have a lot of different VLANs set up here.
By default, when we set up the SonicWALL it sets all rules to ALLOW for the newly configured Zone/VLAN/Gateway. We are able to connect to servers on the new VLAN once they are set up and vica versa. We need to go in to the SonicWALL to lock things down.
If packets are not getting out of the VLAN to anywhere else, that's where I'd look.
Simple test if there's more than one VM on that VLAN: See if they can ping and connect to each other. Even better, if there are two hosts with VMs on the same VLAN same test. If they are talking to each other, the block is definitely down the line.
ASKER
So I created 2 NICs, virtual NICs, assigned an IP, mask and default gateway to both. They are on separate networks.
I also configured the vlan ID for each network.
Everything works, just not sure if this is the best to configure them this way?
That's what the edge/router is for. Fire up its monitors and watch for blocked packets when the VM is only on its correct VLAN. Plus, there should be a gateway configured for each VLAN that is on the subnet usually it's assigned at and to the router.
ASKER
Yes, my core switch is configured correctly, I had a consultant double check, and I've tested everything, so far, the network and different vlans work fine. It's just getting the correct config on this server that was giving me issues, as I needed to to have multiple IPs in multiple networks configured on the DHCP server. I will need to duplicate this on my backup DC as well.
ASKER
The ports where my host servers are plugged in are trunk ports, passing all vlans.
The problem is, how do configure multiple IPs from multiple vlans on a single server correctly?
The way I did it works, just not sure if it's best practice or the correct way?
The Placement of the DHCP server can be located within Any VLAN, you just have to make sure that the DHCP/BOOTP.
not sure I understand what you mean, the IP 10.10.16.0/24 or 10.10.12.0/24 are they part of a defined VLAN?
Where is the inter vlan rules are set, ACLs on the switch, or on the firewall/router
Switch level 2 or level 3?
ASKER
VLAN are segments the server is not
Your setup is to provide a TRUNK to the Hypervisor, you can then setup on the virtual switch the mulitple VLANs to which the IP that the DCA and DHCP have.
I do not think it is possible for a Single IP to be a member of multiple VLANs.
TRUNKIng avoids switch port consumption.
Do you have multiple DCs and DHCP servers?
If you do, you can test with one, by configuring the VLAN on the virtual Switch to correctly tag the DC/DHCP server to be in a specific VLAN to which its IP belongs and confirm no changes in functionality..
ASKER
There is no virtual switch to configure. I can only configure the VM in the hypervisor, so my options are allow everything, all vlans, or a specific vlan only.
I will have only 1 DCHP server and 1 backup DHCP server where everything will replicate from my main server to the backup.
I currently have 3 DHCP servers, but will be decommissioning them soon.
I think if you tag your DHCP server's Network with the correct VLAN nothing should change.
Lets try this way, your car has a decal/marker that authorizes your travel in a covetted lane.
The HIghway has 5 lanes with 1 of those covetted lanes and four others, (Trunk)
When you enter the highway you navigate into the covetted lane. But unlike in the network, which your IP in a way binds you to the VLAN to which the IP belongs, the highway does not require you to travel in the covetted lane.
Can you setpup a test VM that is set by the network into a specific VLAN to see whether the IP it gets from the DHCP matches the VLAN to which the network interface is assigned?
Here's the PowerShell and CMD for migrating (backing up) DHCP:
# Migrate DHCP
# TODO Export
$OldDHCPServer = "MY-OldDC"
$Domain = "DOMAIN.Com"
Export-DhcpServer -File C:\DHCPdata.xml -Leases -Force -ComputerName "$($OldDHCPServer).$($Domain)" –Verbose
# TODO Import
$NewDHCPServer = "MY-TempDC"
$Domain = "DOMAIN.Com"
Import-DhcpServer -File C:\DHCPdata.xml -BackupPath C:\DHCP\ -Leases -ScopeOverwrite -Force -ComputerName "$($OldDHCPServer).$($Domain)" –Verbose
# Using CMD
netsh DHCP server export C:\dhcp.txt
netsh DHCP server import C:\Temp\dhcp.txthttps://social.technet.microsoft.com/Forums/en-US/7d76e12f-9e47-4cc4-a280-2f9695de0b11/single-dhcp-server-managing-multiple-subnets
Leads to: Support multiple subnets with one DHCP server by configuring DHCP relay agents
dhcp server should only be on one network with its corresponding gateway; having multiple interfaces and multiple gateways will add confusion and cause issues