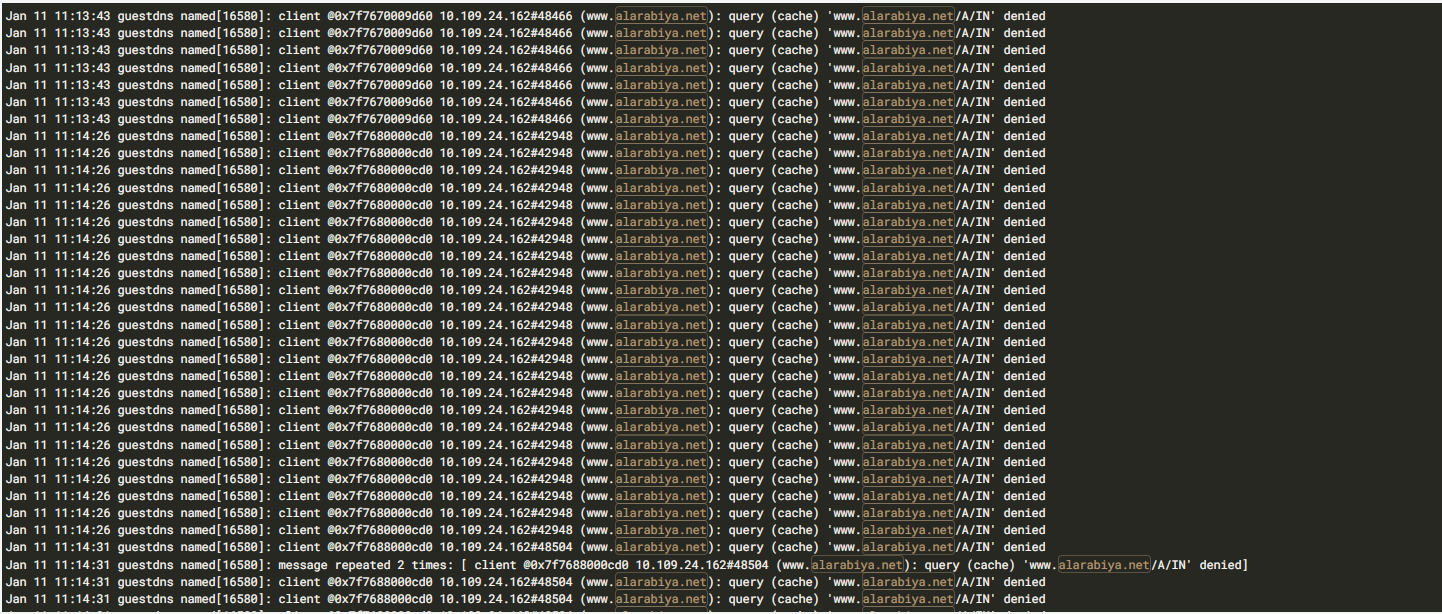
Bind: resolution requests denied
To little info to provide a definitive answer.
And... if adding allow-recursion, this suggests you're trying to use your NS server(s) as recursive servers... to the answer is, you'll have to leave allow-recursion in place.
The way I approach this it so avoid named altogether, as it's massively bloated for client machines + running an inhouse recursive server, is far more complex than you might imagine, as you must run several instances... all on separate networks... in case you have one network die or one NS instance die.
A more robust approach is to run dnsmasq on each machine (with no named anywhere), using a forwarder list like...
And... if adding allow-recursion, this suggests you're trying to use your NS server(s) as recursive servers... to the answer is, you'll have to leave allow-recursion in place.
The way I approach this it so avoid named altogether, as it's massively bloated for client machines + running an inhouse recursive server, is far more complex than you might imagine, as you must run several instances... all on separate networks... in case you have one network die or one NS instance die.
A more robust approach is to run dnsmasq on each machine (with no named anywhere), using a forwarder list like...
1.1.1.1
8.8.4.4
8.8.8.8
I wouldn't avoid bind. Allow recursion but use an ACL substituting the prefixes below for yours.
acl "trusted" {
192.168.0.0/16;
172.16.0.0/12;
10.0.0.0/8;
};
allow-recursion { trusted; };
acl "trusted" {
192.168.0.0/16;
172.16.0.0/12;
10.0.0.0/8;
};
allow-recursion { trusted; };
in bind config, there are 2 sections
allow-recursion should not be set any. If you set it to any, your server becomes a public DNS server, that anyone can use it for DNS resolution.
view "internal"
view "external" allow-recursion should not be set any. If you set it to any, your server becomes a public DNS server, that anyone can use it for DNS resolution.
There's no need to avoid Bind. I've been running our own name servers for decades
Or you can add your trusted IP's directly to your recursion list. You may even want to add localhost for good measure
allow-recursion {192.168.0.0/16; 172.16.0.0/12; 10.0.0.0/8; localhost;};
This would generally go at the top of your config file within your options parameters.
Or you can add your trusted IP's directly to your recursion list. You may even want to add localhost for good measure
allow-recursion {192.168.0.0/16; 172.16.0.0/12; 10.0.0.0/8; localhost;};
This would generally go at the top of your config file within your options parameters.
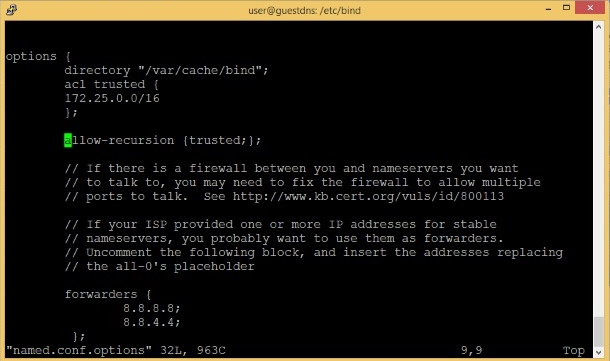
You forgot a semi-colon
allow-recursion {
172.25.0.0/16;
};
allow-recursion {
172.25.0.0/16;
};
ASKER
@Yujin Boby
do you thing your suggestion can be the solution for the other issue I am descussing here:
https://www.experts-exchange.com/questions/29231261/Forward-all-resolution-requests-other-than-added-manually-to-forwarder.html ?
here is my named.conf.local content :
//Forward Zone
zone "abc.com.sa" IN { // Domain name : abc.com.sa
type master; // Primary DNS : master
file "/etc/bind/forward.abc.com.sa"; // Forward lookup file
allow-update { none; }; // Primary DNS set : "none" ;
};
//reverse zone
zone "1.168.192.in-addr.arpa" IN { //Reverse lookup name, should match your network in reverse order
type master; // Primary DNS : master
file "/etc/bind/reverse.abc.com.sa"; //Reverse lookup file
allow-update { none; }; //Primary DNS set : "none;" ;
};
would you give me more details about what exactly should be added ?
do you thing your suggestion can be the solution for the other issue I am descussing here:
https://www.experts-exchange.com/questions/29231261/Forward-all-resolution-requests-other-than-added-manually-to-forwarder.html ?
here is my named.conf.local content :
//Forward Zone
zone "abc.com.sa" IN { // Domain name : abc.com.sa
type master; // Primary DNS : master
file "/etc/bind/forward.abc.com.sa"; // Forward lookup file
allow-update { none; }; // Primary DNS set : "none" ;
};
//reverse zone
zone "1.168.192.in-addr.arpa" IN { //Reverse lookup name, should match your network in reverse order
type master; // Primary DNS : master
file "/etc/bind/reverse.abc.com.sa"; //Reverse lookup file
allow-update { none; }; //Primary DNS set : "none;" ;
};
would you give me more details about what exactly should be added ?
The ACL belong above the options.
always check your config first:
named-checkconf -z -t /var/named/chroot /etc/named.conf
or without chroot
named-checkconf -z /etc/named.conf
always check your config first:
named-checkconf -z -t /var/named/chroot /etc/named.conf
or without chroot
named-checkconf -z /etc/named.conf
it is working after I added:Recursion is that the DNS server goes out is way to find the infor for you (starting at the root servers).
allow-recursion { any; };
in options file
but what {any} is referring to?
I saw some settings configure as allow-recursion { trusted; };
any means all internet addresses are allow to do this. You want to prevent misuse, so only allow from your LAN (or addresses you trust to not abuse the resource).
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Obvious it works with any as ACL,,, you now also allow MY systems to use your DNS server as resolver.... aka you just became an Open-Resolver.
https://www.radware.com/security/ddos-knowledge-center/ddospedia/open-dns-resolver/
https://www.openresolver.com/?__cf_chl_f_tk=ABsoBVsjVqVU1IX2N0xK4RWuS3qCTQCCWu2sbG6I.sc-1642251833-0-gaNycGzNCJE
How large is your bandwidth? Can you handle several thousands of addresses resolution requests / seconds?
How does you ISP treat customers that offer services to reflected DNS attacks? (ie. people asking DNS translation with fake source IP so your system seems to attack the target (which is mentioned as source.
Please do YOURSELF a favour and use a fitting ACL... if your IP address inside is:
192.168.1.0/24 -> use { 192.168.6.0/24; }
Alternative ly use:
https://www.radware.com/security/ddos-knowledge-center/ddospedia/open-dns-resolver/
https://www.openresolver.com/?__cf_chl_f_tk=ABsoBVsjVqVU1IX2N0xK4RWuS3qCTQCCWu2sbG6I.sc-1642251833-0-gaNycGzNCJE
How large is your bandwidth? Can you handle several thousands of addresses resolution requests / seconds?
How does you ISP treat customers that offer services to reflected DNS attacks? (ie. people asking DNS translation with fake source IP so your system seems to attack the target (which is mentioned as source.
Please do YOURSELF a favour and use a fitting ACL... if your IP address inside is:
192.168.1.0/24 -> use { 192.168.6.0/24; }
Alternative ly use:
acl trusted {
192.168.1.0/24;
}
option {
...
allow-recursion { trusted; } ;
...
}

ASKER
allow-recursion { any; };
in options file
but what {any} is referring to?
I saw some settings configure as allow-recursion { trusted; };