Windows OS
--
Questions
--
Followers
Top Experts
Anyone know how to DISABLE bitlocker on Windows 11 Home? (The idiots at Microsoft turn it on by default for W11 Home and seem to have made it impossible to turn off)
For the record, I wouldn't touch bitlocker with a bargepole. I use encrypted drives all over the place and the only system I trust is Veracrypt (the successors to Truecrypt)
But I bought this laptop for a client and found I couldn't install the Rollback which I routinely install. The reason turns out to be that Bitlocker is running.
I have tried about a dozen options spelt out here
and here
https://windowsreport.com/disable-bitlocker-windows-11/
first, you don't get gpedit on home editions, so I had to download that from github.
and second the Bitlocker policy paths indicated on that page do not exist for W11 Home
If you're optimistic enough to believe anything from Microsoft and
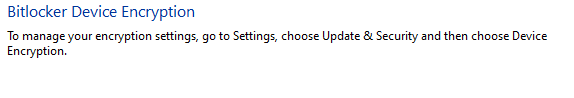
find your way to "Manage Device Encryption" you get to a form with this gem on it:
if you go looking for "Update & Security" it doesn't exist on W11 Home
but you can find your way to "System and Security" where you will find "Device Encryption"
click on that, and you get back to the form above.
Allegedly, you can right click on a drive in Explore and should see a Bitlocker option (or "More", then the Bitlocker option) there. Nope.
The command line option (run from sys32)
manage -bde -off c:
doesn't work
And the Powershell option
Disable-BitLocker -MountPoint 'C'
is equally useless.
The only obvious route I haven't yet tried is editing the Registry but I can't find any reference to the appropriate registry settings.
Anyone?
Zero AI Policy
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Just another thing, bitlocker gets enabled if you use an M$ account, if you setup a local account it's less likely to happen.
The pain with Win11 home... It does stuff without you knowing, then hides how to fix it, when what it did becomes a problem. Frustrating. I also agree bitlocked drives are not a good thing -- especially boot drives. It can vastly complicate recovery, when issues inevitably arise. And it does little to protect data, while the drive is installed on the PC. -- Just my 2 cents on one of my pet peeves.
Rindi,
its much less neat than that!
For Windows 11 HOME users (at least - haven't yet had to fight with PRO but it should be easier) the bitlocker is enabled by default and, as you can see from the above conversation, Microsoft has done its best to hide the means of disabling it. The ONLY relevance of the Microsoft account in this context is that for those "normal" users who don't know how to avoid being bullied into signing up for (or into) a Microsoft account in order to complete their Windows 11 setup, then not only is the Bitlocker enabled whether you like it or not, but the recovery key is automatically copied to the Microsoft cloud - without notification and without your permission.
Which tells you all you need to know about how genuinely secure bitlocker is...
For that and dozens of other reasons I train all my clients to avoid Microsoft accounts like the plague.






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
Fred, your comment appeared just after I posted my reply to Rindi. As you can see, we obviously agree!
And, more generally, I agree with your comment about the complications raised by encrypting system drives. I have had to do that in some scenarios, (like holding sensitive data on laptops in a temporary location with thousands of punters wandering in and out) and we've used Truecrypt/Veracrypt to do the job properly (you can't even start the OS until you've unlocked the drive) but that is a PITA which users resent so we try to avoid that.
Moving data away from the System drive and Encrypting data drives, especially removable ones, on the other hand, is pretty routine, but who in their right mind would trust Microsoft to take care of that? Its not a competence question, of course. I'm sure they know HOW to do it properly. They're just not allowed to! Or, more precisely, they're obliged, by the CLOUD ACT to comply with secret demands from the US Authorities to hand over any data they've got access to.
/soapbox off
As far as I know, bitlocker isn't enabled by default either on Windoze 10/11 home or pro, as long as there isn't an M$ account setup. The problem is that M$ makes it very hard for you to setup a PC with just a local account (that is for both, home or pro). To make sure you don't have to setup such an account, you must make sure there is no internet connection during the installation or setup process, & you also have to click away some nag screens which warn you about the "Limited User Experience" you get with a local account, along with additional reboots during the process.
If Encryption is enabled & you have an M$ account, the bitlocker key at least is stored online at your M$ OneDrive location, & with it you can then access the locked disk (but that of course means the user needs to know his OneDrive credentials, which isn't always the case, as "Home" OS Users often don't even know they are using an M$ account to logon to their PC, & as has been mentioned, M$ does it's best to hide as much as possible from all.
Classically, what we're seeing here is the result of absolutely typical Microsoft Obfuscation.
Last time I encountered it this obviously was after I learned that Microsoft was claiming end to end encryption for Skype about 4 years before they actually did it for real (in a very limited manner for a max of 2 users, speech only). The way I learned it was by suggesting a means of achieving it and they were obliged to reply that my suggestion couldn't be implemented because what they described as E2EE was actually User>>Microsoft>>User encryption. i.e. they actually designed a middle man attack into their Skype implementation - following their abandonment of the original Skype P2P model (which, though a weak home grown E2EE implementation, was considerably more secure than going through a middle man!).
I have no firm evidence but I would place a tidy wager that the Microsoft model was, at least, "strongly advocated" by the US TLAs with whom they've long had, and continue to maintain a close relationship. And, stupidly, because I didn't think I'd ever need it, I didn't retain the correspondence. Oh, and I should mention that their excuse for this arrangement was that, for some connections, like Skype>>Phone, ONLY user>>Microsoft>>Phone would permit encryption - which sounds plausible until you learn about Whatsapp, Signal and a few others... But even with that excuse, the model would only be justified for the Skype>>Phone connections, not Skype to Skype.
I got involved in an argument with an (ex) colleague when I was pressing for the need to keep some of our sensitive business discussions confidential and insisting that, for that reason, we couldn't use Skype and the pillock kept insisting that Skype was true E2EE. So I went looking for 3rd party confirmation of what I already knew. It was amazingly difficult. Microsoft continued to obfuscate. Their typical phraseology was never as blatantly false as "we have implemented true E2EE in Skype - and here's the Trusted 3rd Party security audit to prove it" but more along the lines of "Your conversations on Skype are safe because they're encrypted" (without mentioning their man in the middle status) . All the "commercial" sources seemed to be swallowing the Microsoft line, while most of the serious geek sources were routinely scornful of Microsoft claims although only a minority were aware of the User>>Microsoft>>User arrangement. So you could effectively find support for any position you chose to take.
I can see very similar results in the searches for "Is Bitlocker enabled by default on Windows 11 Home?" There are sites claiming it's not even possible! Others which tell us that the Home version has to be enabled with the aid of an MS account, but that its a kind of "Bitlocker-lite" (what an encouraging prospect that is!), and others that confirm, as I've found to my cost, that it most certainly IS (though I don't know and don't care whether it was the "lite" version) and then there are sites like this one, arguing (with, apparently, a straight face) that mandatory Microsoft Accounts might be a good thing BECAUSE "BitLocker will be enabled by default on all Windows 11 PCs" (and we don't want the great unwashed losing access to their machines because they've not got the nous to look after their own keys)
All I can tell you is that.
a) I know how to avoid the MS account entanglement and routinely do, and did for this system; and
b) despite that, and prior to any connection to the web, Bitlocker was enabled on the brand new laptop we bought, with Windows 11 Home on it.

Get a FREE t-shirt when you ask your first question.
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Yes, I have seen bitlocker enabled on new win 11 home laptops.
Yes, I always recommend not to use M$ accounts to logon on your PC.
As I said earlier bitlocker is pretty much worthless except for the situation where the drive is removed. And it can seriously complicate recovery from a variety of issues that will arise down the road.
Windows OS
--
Questions
--
Followers
Top Experts
This topic area includes legacy versions of Windows prior to Windows 2000: Windows 3/3.1, Windows 95 and Windows 98, plus any other Windows-related versions including Windows Mobile.