Peer (or route) two local network gateways in Azure?
A network engineer I am not, so I am asking for step-by-step instructions to get this working until I can understand it better.
We have two current on-prem networks a) 10.10.x.x and b) 10.20.x.x. The goal is to VPN these networks into Azure so that both on-prem networks can talk to the Azure network. In Azure, we have a resource group containing a VPN gateway and two virtual networks. Virtual network A has a gateway subnet of 10.9.x.x and a VLAN subnet of 10.9.1.x where the Azure virtual servers are located. Virtual network B has a gateway subnet of 10.19.x.x and that is all. The two virtual networks are peered with the default settings.
The on-prem network A (10.10.x.x) can see and communicate with all assets in Azure. The on-prem network B (10.20.x.x) cannot communicate with anything in Azure - even though the VPN light is green and connected.
I originally just wanted a single virtual network in Azure and the ability to peer (or route) the two Azure local network gateways together using one VPN connection. All of the documentation I've seen only allows for the peering of two virtual networks.
Is there a way to the on-prem 10.10.x.x, the on-prem 10.20.x.x and the Azure 10.9.x.x networks to all communicate and play nicely together?
I know I'm close, but I just cannot figure it out. Frustrating!
If the on-prem network A can communicate with both Azure VNets then the peering is fine. There is a setting in the peering that is often missed.
Does the on-prem Network B connect to the same router as Network A?
If so, then as Mlanda says, the problem appears to be with the Local Network Gateway. This is the Azure object that represents on on-prem networks.
It's likely that you just need to add the on-prem Network B IP range to the Local Network Gateway. Go to the LNG in the Azure portal, click on 'Configuration'. There you can add the IP range of the on-prem network B, then click Save.
ASKER
So you have two on-prem networks, each connected to a different Internet connection (provided by different ISPs) and just the one router?
"and therefore have two separate public IPs that must use the Azure VPN Gateway."
In this case, I think you need to think of each of these networks as a separate site altogether. You would therefore need separate IPsec VPN tunnels.
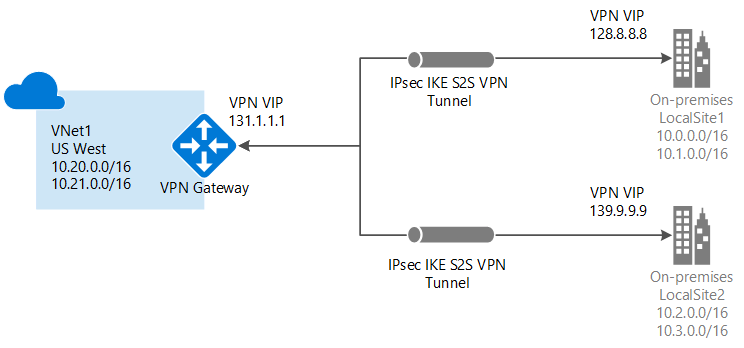 (Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/design)
(Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/design)
ASKER
Daryl - yes, two on-prem networks that come into two different ports on the firewall. From the firewall, we have rules to forward traffic (or certain types of traffic) to either on-prem or Azure resources. Could I simply develop a firewall rules to forward all traffic from one port to the other on the firewall and then send it up to Azure? Yes, but I'm trying not to upset the apple cart and rewrite all of the rules we have that are working now.
ASKER
Mlanda - this is almost EXACTLY where I am right now. This tutorial is what I tried doing over this past weekend. I have one Azure VPN gateway with two site tunnels and both tunnels are working.
In your example, I have 10.20.0.0/16 in a virtual network with the VPN gateway listed as a Connected Device and this is the virtual network that can talk to the on-prem assets. The 10.21.0.0/16 is also a virtual network, but does NOT have the VPN gateway listed as a Connected Device. This is why I tried peering and it didn't work. I need 10.20.0.0/16 to talk to 10.21.0.0/16 and we should be good to go.
We're very close to solving this, but the last piece of the puzzle just escapes me.
I'm thinking of the routing in terms of the Azure routing and your on-prem routing.
So does traffic from on-prem Network A go out on one public IP and the traffic from on-prem Network B go out on the other public IP?
Also...
For the two Local Network Gateways...
Does one have the public IP of Network A and ONLY the private IP range of Network A?
Does the other one have the public IP of Network B and ONLY the private IP range of Network B?
... or do both local network gateways have the private IP ranges of both on-prem networks?
ASKER
Daryl - yes. Network A goes out on one public IP and Network B goes out on another public IP. The firewall pushes both networks up through their public IPs to Azure through the S2S Local Network Gateways, but that is where the traffic dies.
Currently, the Local Network Gateways ONLY have the public IP and private ranges of their respective networks.
"Currently, the Local Network Gateways ONLY have the public IP and private ranges of their respective networks. "
That's how it should be.
Are the VPNs on your on-prem router set up as policy based or route based?
ASKER
Route based.
In your example, I have 10.20.0.0/16 in a virtual network with the VPN gateway listed as a Connected Device and this is the virtual network that can talk to the on-prem assets. The 10.21.0.0/16 is also a virtual network, but does NOT have the VPN gateway listed as a Connected Device. This is why I tried peering and it didn't work. I need 10.20.0.0/16 to talk to 10.21.0.0/16 and we should be good to go.
Ah, thanks. If I understand correctly now, this means that we do not have problems on-premise. We now just want to have multiple vNets on the Azure side? This is a hub and spoke architecture. Something like this diagram right (this time your on-premise networks are on the left)? You want to have a hub in the middle, have your on-premise connections reach this hub (whicih is where your VPN Gateway will sit), then you peer across multiple vNets. Some shared services can also be hosted within the hub vNet and you peer to another vNet. [I like diagrams, clearer than text]
ASKER
Mlanda - LOL! Well you just added a whole bunch of question marks above my head. I was all good reviewing and following this tutorial until it got to the "deploying vWAN ARM" step. Are all of these service account steps necessary if we aren't using Fortinet?
Oh no. Not saying user fortinet. But the basic pieces are there. An focusing on the architecture and had just been looking for something with a diagram that captures it nicely. Azure Virtual WAN, vNets, etc.
ASKER
Mlanda - no matter what I try, the multi-site VPN using the VWAN is not working. Have you tried one of these before? It doesn't allow for public IP's and therefore will not allow for VPN connections from the on-prem firewall. It is near impossible to set up connections in the group because it wants to completely unhook everything in Azure to become active. I'd like to run this thing as a test in case it doesn't work, but I am not having any success.
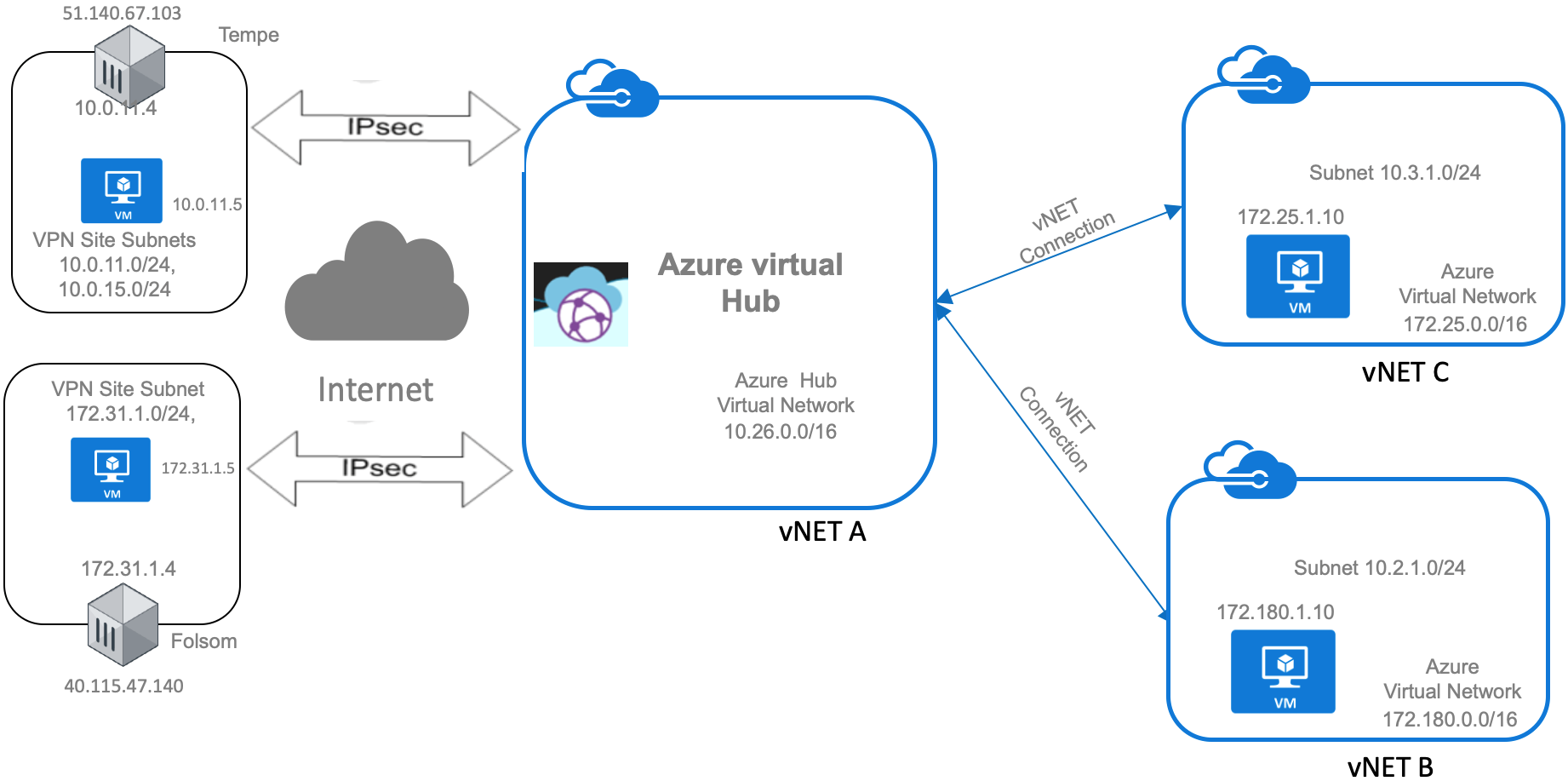
A more comprehensive description of your setup would provide more clarity. Are you using ExpressRoute? Site-to-Site VPN?
1: What is the configuration of your local network gateway? You might just need to add more prefixes:
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-create-site-to-site-rm-powershell#code-try-22
Open in new window
2: On your Site-to-Site VPN Gateway configuration, check the Client Address Space:
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-site-to-site-classic-portal