Workstations delete from AD still let you log in
Something has changed. At this point I have two customers. One with a 2019 Standard Server and the other with a 2016 Standard Server. Both have Windows 10/11 workstations that have been deleted from the AD yet none of the delete computers give an error when rebooting and logging in to the domain. I thought it use to give to a trust error and wouldn't let you log in. Has something changed?
ASKER
"it use to be that it would give you a trust relationship broken and not let you log on"
This is what is supposed to happen.
Run SET LOG from a command prompt and see if the name of the domain controller comes back.
ASKER
Search for the computer object to confirm.
Dcdiag /v /e ...
This way it is unaware the object was deleted..
ASKER
ASKER
you may have to look at the objectID on the system and then locate it in the AD.
"Yes. In both cases it returns LOGINSERVER=\\SERVERNAME"
SERVERNAME is a domain controller?
ASKER
and see how many you have versus how many you have.
If the object is deleted, it should not authorize from the AD.
https://learn.microsoft.com/en-us/powershell/module/activedirectory/get-adcomputer?view=windowsserver2019-ps
ASKER
ASKER
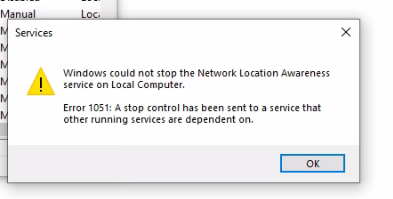
ASKER
The first time it asks for credentials, have you considered restarting the server where the share is whether it is the one that has the cached token?
I've not run into this.
look at the Settings, accounts , access work or school to see whether those credentials are added there.
ASKER
To see your cached credentials, start a "Run" command, and run this:
rundll32.exe keymgr.dll,KRShowKeyMgr
ASKER
I think you are working on a theory that it is using your Admin domain credentials versus matches his own domain credemtial.
Test this out, have the user open a specific file someoddlynamedfile.txt.
then access the shahred sessions which user is being reflected as accessing this file.
Is it being access by your account, administrative or the person's?
you can test it out in a subfolder you create as a test, blockadminfromaccess, add an explicit deny to your account to it. Then see whether that user has the ability access it or gets a denied access do to the restriction.
A deny rule supersedes everything.
To delete, you would have to go through the parent folder, one above and reassert Parent Folder rights rights on the subfolders.
i.e. in \\server\sharename\create_
and on the fakechildfolder add a deny to your account, the account you think is cached.
I think MS's sysinternals has a tool that may help as well to look who is using the file if the above are not something you want to pursue i.e. the tool can reflect who is using/accessing a specific file.
The issue might not be cached credentials, but the user has the same password with the same account.
create a new test user, see if this test user will persist in having access post logout and does not have the net use reflect a retention of the reference.
It is a rabbit hole, but ...
ASKER
As mentioned above Microsoft spent most the day on it yesterday and was totally mystified. @PAul MAcDonald that command did not show and cached credentials. By far the easiest thing to do would be to simply delete this users profile. I am sure that would do the trick but I have this happening at a couple different customers and it really needs to be addressed.
Do you use 802.1x to authorize system's access to the network?
when the user logs in, he uses cached credentials into the workstation. then the network connection is reestablished and the user has access to the resources.
The alternative, change the AD password for the user or set the user account to require to change password and see if the user gets a prompt to change their password.
ASKER
Then, when the user logs in, the user credential authenticate the system past the 802.1x requirement.
The other possibiliy, the object being deleted is not deleted, but is present within the AD somewhere else. or is not by the name.
YOur assumption that the worstation is deleted may be the issue.
the workstation name is somebox, but the object in the AD is anotherbox.
You need to see whether the AD objectIDs that you have in AD can be matched to each station.
objectsid/sid
This may help locating the SID of the computer/system at issue
https://social.msdn.microsoft.com/Forums/en-US/88c2cce6-7c53-4553-81a6-6bc4c59226fa/how-to-find-out-objectid-or-deviceid-via-device?forum=WindowsAzureAD
i.e. someone mistakenly renamed the computer account in the AD under the impression that it will update the computer name.
or something did not go right with a rename of a system....
now using the ObjectID from the registry, see if this objectid exists in the AD. get-adcomputer
ASKER
ASKER
The other is to use a user account that could never have been loged into this workstation and see whether it can login.
If the system, workstation try the rename computer name, it shold correspond with the change of the account in the AD.
There must be something obvious
Domain trust?
ASKER
As mentioned several times no other user can log in. They get the trust broken error.
As mentioned there is no computer in the AD
Microsoft has been at this for days. They agree is should not be happening but have not found a solution.
This is why the user is allowed to login. and then the USER has rights to the environment. what is the end goal?
you can login, revert the workstation to a workgroup, or rejoin it to the domain to reestablish the trust.
you would need to make sure you have the local admin login if you remove it from the domain.
ASKER
Someone deleted the object on the AD. as far as the workstation is concerned it is part of the AD while not having any rights on boot to access netlogon/sysvol or any GPOs.
only a user who previously logged in will have access.
I believe I suggested sometime ago to change the user's password in the AD and see whether while the user will be able to login into this ghost/zombie system, will the user still have access to the domain resources.
If it was a different test, the person in possesion of the system will need to know the credentials that were successfully used before. i.e. if it is a laptop that is lost, in the AD the objected is disabled or deleted, .....
Are these machines on the same network as a domain controller? If not, they may be using cached credentials. Otherwise, see what domain controller authenticated the user and see if that domain controller is replicating properly.
Can these users actually access resources on the domain, or can the users simply log in to the machine?