Security
--
Questions
--
Followers
Top Experts
Would like to know if following steps/documentations are meant
for Imperva WAF on-prem or Imperva WAF in Cloud? The
vendor said all the links/docs below the line ------ are meant
for Imperva WAF in the Cloud & not on-prem, is this true?
Need something (say actual on-prem's Imperva WAF's manual
or doc) to verify the vendor's claims.
Vendor advised us that "there are no out of the box functions for
CSP policy for on-premises Imperva WAF; it's only for Imperva
WAF in Cloud"
----------------------------------------------- extract ---------------------------------------------------------
Will need customised CSP directive; and to navigate into the client side protection
https://docs.imperva.com/bundle/client-side-protection/page/client-side-protection/advanced-csp.htm
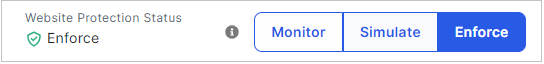
There has to be discovery (Monitor before Enforce) :
https://docs.imperva.com/bundle/client-side-protection/page/client-side-protection/scripts.htm
After you have reviewed the discovered services and assigned a status to each (allow or block), you can set the Website Protection Status to Enforce.
You can choose to enable enforcement for discovered web services, or only for the scripts that are run by those services.
https://docs.imperva.com/bundle/client-side-protection/page/client-side-protection/mitigation.htm
When you initially onboard a site, Client-Side Protection is operating in Monitor mode, and is not blocking any services.
After you have reviewed the discovered services and assigned a status to each (allow or block), you can set the Website Protection Status to Enforce.
At the top of the Client-Side Protection dashboard, click an option to change the website protection status.
Zero AI Policy
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Ok, noted Imperva on-prem WAF can't help.
We will have to accept the risk of our SharePoint's
pentest CSP (inline-eval & inline-...) issues as SharePoint is
known not able to be configured (like IIS, Apache) to fix
the CSP issues.






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
Security
--
Questions
--
Followers
Top Experts
Security is the protection of information systems from theft or damage to the hardware, the software, and the information on them, as well as from disruption or misdirection of the services they provide. The main goal of security is protecting assets, and an asset is anything of value and worthy of protection. Information Security is a discipline of protecting information assets from threats through safeguards to achieve the objectives of confidentiality, integrity, and availability or CIA for short. On the other hand, disclosure, alteration, and disruption (DAD) compromise the security objectives.