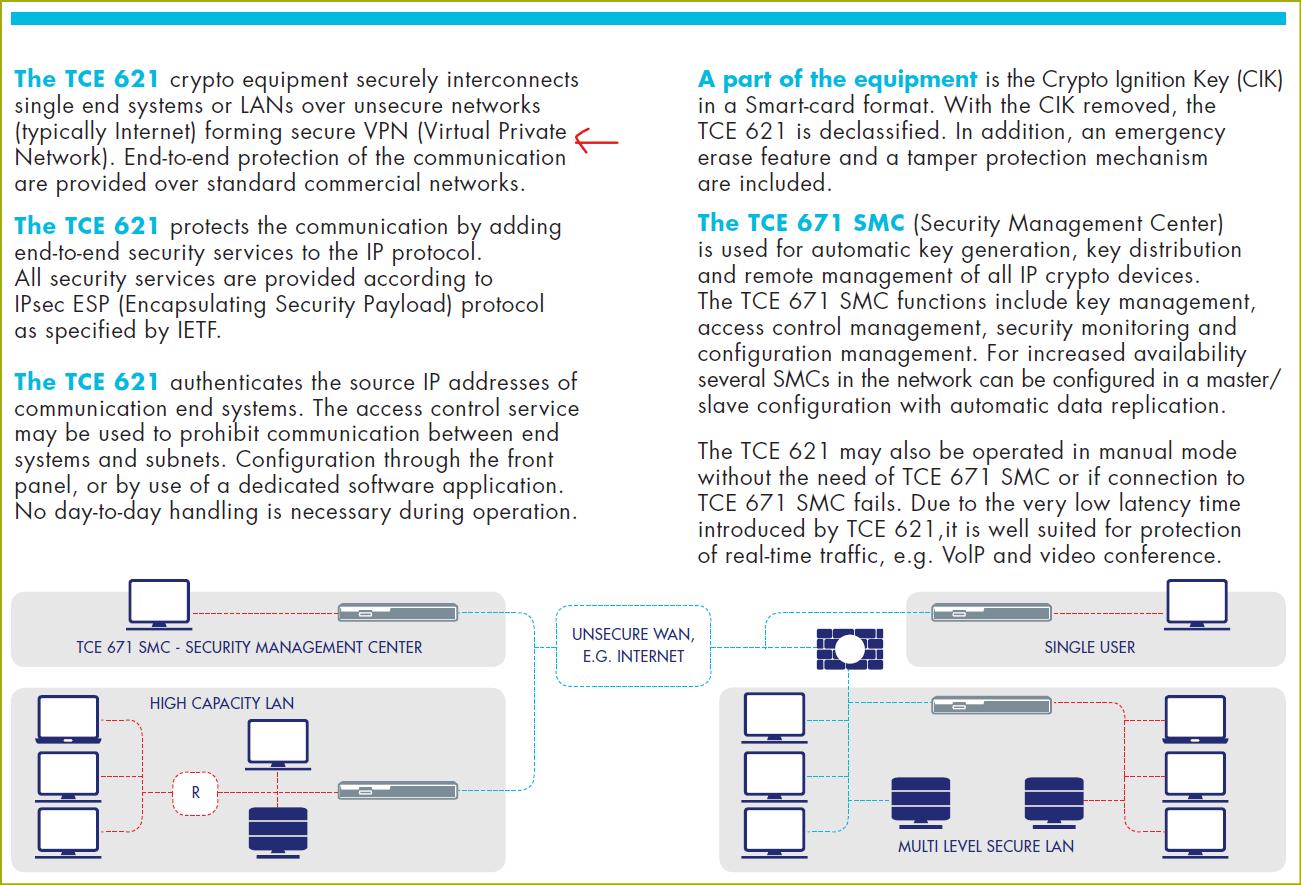
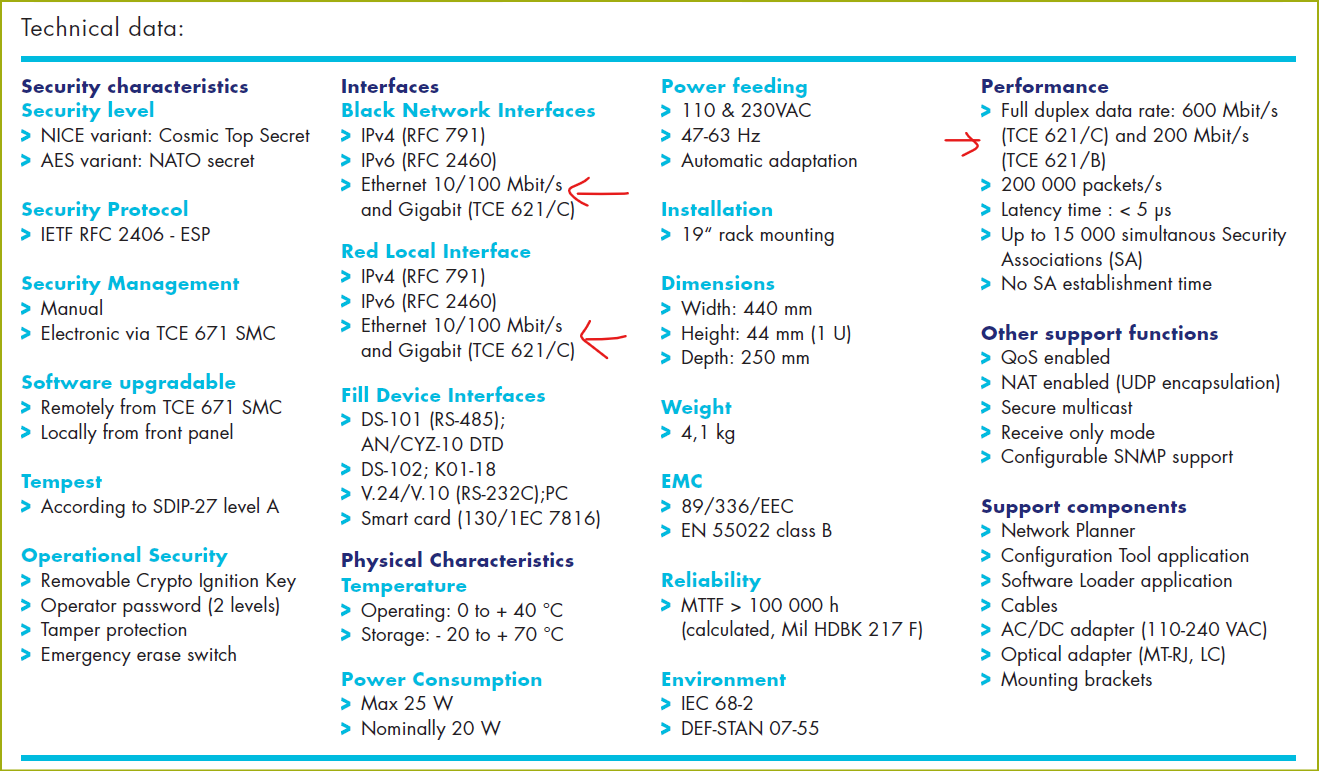
Cyber Security
--
Questions
--
Followers
Top Experts
can someone explain this device in friendly terms?
this seams justly ike a device that holds a VPN for the network.
“The TCE 621/C is a Gigabit IP encryption device approved for all NATO security levels. It is available both with electrical and optical Ethernet interfaces. This high grade, CCI crypto device utilizes a NATO Secret algorithm (Type A) and is fully interoperable with NICE (NATO IP Crypto Equipment). The TCE 621/C can be remotely managed from a TCE 671 (SMC) or locally from the front panel. TCE 621/C is software reprogrammable.”
https://www.ia.nato.int/niapc/Product/TCE-621-C_170
i find this interesting and wonder what it is and if someone can explain
Zero AI Policy
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Normally we called such device ip encryptor meaning it protect your traffic point to point to avoid other from tapping anywhere in the connection. It is point to point but not at layer 2 (data link layer), rather at layer 3 (IP layer such as IPsec). Hence not the typical TLS or certificate needed at Layer 4 above). Just ip level encryption that serves as another layer to protect the traffic from source to dest. Mostly such requirement can be across private network btw sensitive sites that may even be overseas. Or even unsecured commercial network
so like a macsec encryption device
I should clarify my last post it should be IP level layer 3 meaning this device is IPSec instead of layer 2 macsec, after I re-read the info on this specific device model.






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
aw so all it really is is a dedicated VPN for a network if I am understanding correctly?
after much research it seems to be VPN box.
hmmm. could i make a device similar to this HAIPE device? one that is portible?

Get a FREE t-shirt when you ask your first question.
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
High Assurance Internet Protocol Encryptor (HAIPE) is of similar calibre of network security hardware device. I would think it is non trivial from hardware and need to assemble and make the box common criteria based. Users of such tends to be those of need for high security hence software based using open source like openssl, open vpn would not be sufficient using software alone. There is also the performance and concurrent tunnel needed to support etc. Overall I think production grade need further rigor in certification which companies would have invested alot in for production grade boxes.
aw, I see. is there any open source way I can build one of these devices? I wonna try to make one of my own. for experimental purposes, of course, it's not making a commerical just my own little thingq
maybe start simple to even setup ipsec server before going into appliance. included some that you probably need to more research and explore further
OPNsense® is an open source, feature rich firewall and routing platform, offering network protection






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
I know how to setup VPN servers, I've done it before. but isn't this device just a single purpose VPN server basically? or would it be a single purpose VPN client
That is why I say non trivial as hardware and performance tuning is involved. Encryptor are appliance based, and even portable version still need motherboard and embedded os to run within.
aw.
I've set up things like VPN servers and clients, allbeit in the cloud and not server on prem….

Get a FREE t-shirt when you ask your first question.
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Which is why requirement for such device tends to be on premise rather than virtual
I know it is on prem, there is only an on prem solution mentioned.
but I think physical appliances are almost the same as virtual without the cloud
there is software and hardware. the openvpn and the link shared speak on those






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
yeah but as far as i'm aware, these are PFSense boxes and aren't like the TCE621/C, which is a deddicated encryption device.
I could utilize them as such, but it'd be almost useless as it has only that value, not using the wifi or Ethernet….
Perhaps it can have services disabled functions not needed like stripped selinux and agree to go close to encryptor you probably need to have crypto chip used that perform bulk encryption at wire speed.
can you give me example of a, crypto chip? do you mean like a hardware security module?

Get a FREE t-shirt when you ask your first question.
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Better referred as crypto processor. It may be ASIC, FPGA based but will perform dedicated cryptographic procesesnlike encryption etc. Not hsm which is a package of crypto chip, network interfaces, embedded harden os, etc
https://semiengineering.com/knowledge_centers/semiconductor-security/crypto-processors/
interesting. I always thought HSMs and crypto processors were the same
HSMs are specialized devices that securely store and manage cryptographic keys for cryptocurrencies. They act like a vault for your private keys, protecting them from hackers and unauthorized access. The crypto processor, I see it more of the chips etc but of course industry may say HSM is a specialised processor etc etc…strictly speaking, I see latter as a chip that does crypto stuff and a 'body' that cab be hardened tamperproof box, PCIe attached with that chip.






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
intresting. so basically strip it down to a VPN (i'm guessing a VPN like IPSec) with selinux policies and such, put in a cryptoprocessor and you essentially have a TCE621/c of your own
yup i am not hardware guy (: that should be the simpler i can see from the main ingredient. and of course such boxes also has tamper-proof, tripwire to prevent and immediate erase once tamper, and even shielding from side channel attack etc - but i see it left for seriously harden boxes..
when we say, seriously hardenedm, besides the crypto processors and tamper protections and stuff, what, hardening, are we talking about ? becdies, of course, maybe some services disabled like ssh, and (maybe) colonel hardening and such.

Get a FREE t-shirt when you ask your first question.
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
I just meant appliance security and what u listed to harden the os should be done as well
-audit logging
-alarm detection and logging
-supports up to multi-factor authentication (smart card, password)
-tamper resistant chassis
-anti tamper detection
yeah.
also, alarm, logging? does that mean if something happens a fire alarm will go off or something?
I think the box yet to be so so smart as it is still just IT device. But typically it is put in server room that has the cctv, smart card entry etc, and if room has sense smoke or fire, there should be building system to trigger response.
The logging is for audit trail and alarm more of logs sent over to SOC for monitoring on unauthorised access to the encryptor box.






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
o. I thought you meant if someone triggersa security event it would trigger a fire alarm or a breach alarm, as in the cloud 120db fire alarm system.
nevertheless, that'd actually be an interesting experiment…
speaking of, I have to ask.
is there any way to make this box portible, as in make it go on a hotspot, like the inseego mifi X pro 5G
interesting to have portable encryptor. saw in the industry but not ventured into it
https://www.stengg.com/en/cybersecurity/products/wiz-knight/
Cyber Security
--
Questions
--
Followers
Top Experts
The cyber security specialization covers the fundamental concepts underlying the construction of secure systems, from the hardware to the software to the human-computer interface, with the use of cryptography to secure interactions. Cyber security refers to the protection of personal or organizational information or information resources from unauthorized access, attacks, theft, or data damage. This includes controlling physical access to the hardware, as well as protecting against the harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures.
Create your account and start contributing!