Article
Article

Best Practices guide for Exchange DAG
In this article, we will discuss the best practices to follow, while installing the Microsoft Exchange Server with a Database Availability Group (DAG), for replication and business continuity.
Article

Forward emails to external address in Exchange server.
This article will help you forward emails coming to a mailbox to an email address external to your organization in Exchange 2013, 2016 and 2019
Article

Migrate Hosted Exchange to Exchange Online (Office 365)
Migrating mailboxes from a Hosted Exchange server to Exchange Online (Office 365) can be a daunting task, and several offerings try to ease the task. Kernel Migrator for Exchange Express Edition is one, and - for once - it deserves the label "express".
Article

Azure AD Connect Password Synchronization not working.
A description of how I fixed an Azure AD Connect password synchronization error.
Article

HOW TO SYNC CLOUD USER TO ON-PREMISES AD ?
This article details the possibility of migrating a cloud user to Exchange On-premises in a hybrid model.
Article

Enable or disable Outlook Anywhere (RPC-HTTP/MAPI-HTTP) in Exchange Server.
This article will help to do the below tasks.
1. Disable Outlook Anywhere for single mailbox.
2. Disable Outlook Anywhere for all mailboxes in the organization.
3. Enable Outlook Anywhere for single mailbox.
4. Enable Outlook Anywhere for all mailboxes in the organization.
Article

How to Stop emails to onmicrosft.com (O365) domains from External World
This article discusses the needs to block emails to onmicrosoft.com (O365) domain IDs and the available options.
Article

Microsoft Exchange Database Portability
In this article will discuss what Microsoft exchange database portability is and how we can use it to restore email services along with mailbox data in case of Exchange Server failures.
Article

Securing your Email Infrastructure and your Brand
This article describes the Email relay concepts and the possible road blocks and solutions to certain email security scenarios.
Article

How to Add Additional SMTP proxy address to multiple users
A quick guide on adding multiple SMTP proxy addresses to Users for Office 365
Article
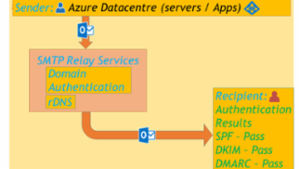
Azure SMTP Restrictions & Resolution with SMTP Relay Services
This post explains how Microsoft has strengthened Azure platform security against unauthenticated SMTP traffic to maintain Azure IP stack reputation and how 3rd party SMTP API can be used to overcome these restrictions.
Article

Step by Step Procedure to Change IMAP to POP3 Accounts
You can use IMAP or POP3 protocol to configure your Gmail account in MS Outlook. However, after
…
Article

Exchange Database failed due to Exchange 2013 Logs Drive Full
Check the reasons why Exchange Database failed due to Exchange 2013 Logs Drive Full?
Article

How to Extract Exchange Mailbox from Exchange Backup File
It is a known fact that if an organization stresses on following a strict backup regime, it always has sufficient material to bounce back from even severe Exchange disasters.
Article

Count Mailboxes in your Exchange Organization.
Get count of mailboxes in your Exchange Organization.
Article

After a database crash, How to mount the Exchange database?
If there is anything erroneous with Exchange Database, it causes a significant effect on email communication till the user remounts the database. Further, database crash directly affects Outlook users due to which they are unable to access their emails.
Article

Move Mailboxdatabase and other logs to different drive in Exchange 2013/2016/2019
This article explains how to move an Exchange 2013/2016/2019 mailbox database and logs to a different drive.
Article

Deal with Exchange Server Failure: Stellar Exchange Toolkit
There’s hardly a doubt that Business Communication is indispensable for both enterprises and small businesses, and if there is an email system outage owing to Exchange server failure, it definitely results in loss of productivity.
Article

Error Solved: Exchange Server Jet Error Code 1601 & 1605
Microsoft Jet database engine errors can crop up out of nowhere to disrupt the working of the Exchange server. Decoding why a particular error occurs goes a long way in determining the right solution for it.


















