Troubleshooting Solution
does anybody know what to put in the pop3 and smtp host server in any kind of e-mail client for …
Article

Strong (but Easy-to-Remember) Passwords
You need passwords for many websites and you know that it's unwise to use the same password …
Video

Setup Mikrotik routers with OSPF… Part 1
After creating this article…
Post
Charter has upgraded their Internet speed from 60MB/s to …
Charter has upgraded their Internet speed from 60MB/s to 100MB/s recently for residential customers.…
Troubleshooting Solution
ISCSI connectivity problems
I have 2x ESX hosts (DL360 Gen9s) Running vSphere 8, Each has 2x 10Gbps NICs
I'm direct cabled (DAC
…
Article

Improve Network Security – Separate DNS from Active Directory
While deploying Active Directory with integrated DNS makes managing a domain easier, it does come with security risks. Separating out DNS can actually improve security and make things harder for a threat actor.
Troubleshooting Solution
127.0.0.1 Blocked
Hello. I am trying to download data from a third party server via Putty and local ip 127.0.0.1. My
…
Troubleshooting Solution
Install DNS server on Switch or Windows
Hi,
I have Windows environment with DC.
My question is about DNS. Some of colleagues like network
…
Post
Whoa, whoa, whoa... Apparently in West Virginia, being a …
Whoa, whoa, whoa... Apparently in West Virginia, being a State Senator is a part time job. Which …
Article
Troubleshooting Solution
How connect laptop to wi-fi in car
Hi
I have a business laptop that has Cisco VPN to connect to Corporate Netowork.
I always use my Home
…
Article
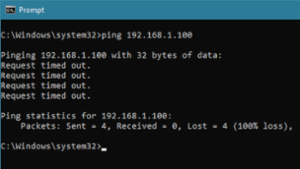
Test IP Addresses with PING
An Experts Exchange member requires a utility that accepts a file with a list of IP addresses and PINGs each of the addresses in the list. If there are any failures, the utility sends an email containing the IP addresses and error messages of all the failed PINGs. This article presents a solution.
Troubleshooting Solution
not able to ping another device on same vlan
I can't ping a server from another server on the same VLAN.
Server-netcrunch-IP-10.10.14.70 (windows
…
Post
Join (https://www.battleforthen
Join Experts Exchange in our support of a user's …
Troubleshooting Solution
Confusing Double NAT
I have been having problems with VoIP phones losing connection. The phone provider suggests that
…
Troubleshooting Solution
Check if it was an internet connectivity issue.
Hi Experts,
I am running a program that would give me the message "Finished", regardless if it really
…
Video

How to use PRTG for Bandwidth Monitoring using NetFlow or Packet Snifffing
In this tutorial you'll learn about bandwidth monitoring with flows and packet sniffing with our …
Video
![Learn how to assess the security of Exchange 2019 by running a vulnerability scan using Zenmap[NMAP]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80346/Learn-how-to-assess-the-security-of-_1_Feed.jpg)
Learn how to assess the security of Exchange 2019 by running a vulnerability scan using Zenmap[NMAP]
Learn how to use the NSE script in Zenmap to check if an Exchange 2019 server is vulnerable to …
Tutorials

Network+ Exam N10-006
The Network+ certification was introduced by CompTIA in 1999 and was designed to do for Network …

Practical Implementation of How to Filter routes from the Routers
In this course the viewer will learn important skill of how to filter routes that are unwanted from …
















