Video
![Using Mimikatz and NetExec in Windows Server 2022 [Educational Purposes Only]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80393/Using-Mimikatz-and-NetExec-in-Window_1_Feed.jpg)
Learn about the significance of dumping hashes from Mimikatz and utilizing them in NetExec. …
Video
![Update your Kali distribution to the latest [One-liner command]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80375/Update-your-Kali-distribution-to-the_1_Feed.jpg)
Update your Kali distribution to the latest [One-liner command]
Learn how to update Kali Linux to the latest version while keeping a backup of the older version. …
Video
![Hacking my lab Exchange 2019 with the ProxyToken Exploit [Educational purposes only]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80373/Hacking-my-lab-Exchange-2019-with-th_1_Feed.jpg)
Hacking my lab Exchange 2019 with the ProxyToken Exploit [Educational purposes only]
Learn about the ProxyToken exploit and its potential impact on your Exchange 2019 lab server. …
Video
![Learn how to assess the security of Exchange 2019 by running a vulnerability scan using Zenmap[NMAP]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80346/Learn-how-to-assess-the-security-of-_1_Feed.jpg)
Learn how to assess the security of Exchange 2019 by running a vulnerability scan using Zenmap[NMAP]
Learn how to use the NSE script in Zenmap to check if an Exchange 2019 server is vulnerable to …
Video

Find accounts that passwords are set to never expire in Active Directory
Active Directory is a powerful tool used by many organizations to manage their network resources and…
Video
![Using IISCrypto 3 3 with Exchange 2019 CU13 [Remove Legacy Security Protocols]](https://d22xog6qk9dtd5.cloudfront.net/encoded/80337/Using-IISCrypto-3-3-with-Exchange-20_1_Feed.jpg)
Using IISCrypto 3 3 with Exchange 2019 CU13 [Remove Legacy Security Protocols]
In this video tutorial, I will show you on how to use IIS Crypto 3.3 with Exchange 2019 CU13 and the…
Video

HOW TO: Runecast Analyzer versus VMware Skyline Advisor Pro 3.5
In this video, I will show you HOW TO: Runecast Analyzer versus VMware Skyline Advisor Pro 3.5, we …
Video

HOW TO: Deploy Runecast and Perform an audit of your VMware vSphere Inventory for Cyber Essentials Compliance
In this video, I will show you how to HOW TO: Deploy the Runecast appliance and perform an audit of …
Video

HOW TO: Select VMware vCenter Converter Standalone 6.2 or 6.3 to complete a P2V for Windows XP or Windows 2003 Server
In this video, I will show you how to perform a Physical to Virtual conversion of a Windows XP …
Video

HOW TO: FIX VMware vSphere Hypervisor (ESXi) Host vulnerability L1 Terminal Fault’ (L1TF) Speculative-Execution in Intel processors: CVE-2018-3646, CVE-2018-3620, and CVE-2018-3615
This video builds on the last videos in this series of Hancock's VMware Half Hour, where we continue…
Video

EE and Philip Elder Discuss MS Exchange HAFNIUM Mitigations
Philip Elder discusses his MS Exchange HAFNIUM Mitigations article…
Video

CRISC Domain 3 | Risk Response and Mitigation Preparation | Muneeb Imran Shaikh
CRISC Domain 3 | Risk Response and Mitigation
Video

Add custom colors and subjects to highlighters in free version of PDF-XChange Editor
This EE video Micro Tutorial shows a great feature in the free version of Tracker Software's …
Video

Certified in Risk and Information System Control - Domain 3 Risk Response and Mitigation.
This is one of my sessions that I conducted in 2019 to support in preparation of CRISC Exam.
Video

TLS in Exchange Server 2019 / 2016 | how to setup TLS | opportunistic TLS, Force TLS | Demo
Transport Layer Security (TLS) is a cryptographic protocol that is used to secure communication over…
Video

Patch your Servers: zerologon exploit part 3 (System down)
In the previous 2 videos in this 3 part series we showed you how a patched operating system is not …
Video
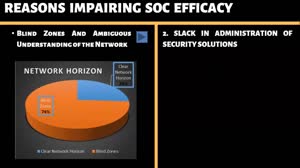
Challenges Impairing Cyber Security Operations in Threat Hunting | Muneeb Imran Shaikh
This video is part of the recorded Webinar from Muneeb Imran Shaikh, an expert in Information …
Video
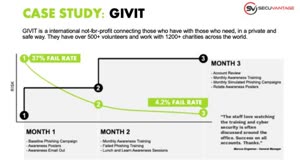
How to Reduce Human Risk with Security Awareness Training
Learn the steps to creating a culture of cyber security awareness within your organization.…
Video

Exchange 2019 - Re-create the exchange security groups in Active Directory
In this video we take a look at the steps to recover the Exchange Security Groups in AD. They could …
Video
![[Webinar] Cloud Killed the Firewall](https://d22xog6qk9dtd5.cloudfront.net/encoded/10004/2017-11-16-13.03-Cloud-Killed-The-Fi_2_Feed.jpg)
[Webinar] Cloud Killed the Firewall
When cloud platforms entered the scene, users and companies jumped on board to take advantage of the…


















