Article
Article

Keyboard shortcuts (hotkeys) to move mouse in multi-monitor configuration - AutoHotkey Script
In configurations with multiple monitors, it can be difficult and time-consuming to move the mouse pointer to a particular monitor. This article presents a script written in AutoHotkey that defines hotkeys — such as Alt+Ctrl+1, Alt+Ctrl+2, etc. — to move the mouse easily and quickly to any monitor.
Article

Acronis Cyber Infrastructure 3.0 released!
Meet modern IT demands with a scale-out, cost-efficient and multi-purpose solution for the Edge.
Article

Enterprises Gain Enhanced Cyber Protection with Acronis Backup Support for SAP HANA
Enterprise organizations are now responsible for more data than ever before. In fact, more data is
…
Article

How to move all windows on one monitor to another monitor with one keystroke - AutoHotkey Script
An EE member wants to move all open windows at once (not one window at a time) from a primary monitor to a secondary one by pressing a hotkey. Bonus: another hotkey that goes in the other direction — move all windows from the secondary to the primary monitor. This article presents such a solution.
Article

BootSafe - The "easiest" way to Boot Windows into Safe Mode
Review of a small standalone freeware utility that is designed to remove the guesswork in trying to get Windows 10 (and all other versions of Windows) to boot into various Safe Mode configurations. Includes a short interview with the author of the program.
Article

Microsoft : Support Resources that Microsoft provides for Free.
I am providing the resources that Microsoft Provides as support to its community. A lot of it is technical and may be beyond what an average user might need. But for a site such as Experts Exchange, I thought it might be a good guide to what Microsoft has available.
Article

Acronis Active Protection takes the fight to cryptojacking
While there were several headline-grabbing ransomware attacks during in 2017, another big threat started appearing at the same time that didn’t get the same coverage – illicit cryptomining.
Article

How to Convert Outlook Express DBX to Outlook 2016 - Ultimate Guide
How to convert Outlook Express DBX to Outlook 2016, 2013, 2010, 2007. The article explains a quick manual trick to easily migrate from Outlook Express to Microsoft Outlook with attachments. It also suggests a professional solution to convert DBX to PST in quick time without loss of email formatting.
Article
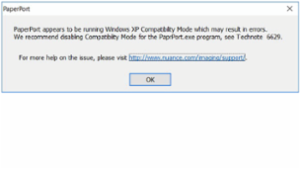
How to fix: PaperPort appears to be running Windows XP Compatibility Mode, see Technote 6629
Nuance's PaperPort may display this error message:
PaperPort appears to be running Windows XP Compatibility Mode which may result in errors. We recommend disabling Compatibility Mode for the PaprPort.exe program, see Technote 6629.
This article provides a possible solution to the problem.
Article

How to create an on/off toggle to mute the system audio/sound with a single mouse click or single keystroke
In a question here at Experts Exchange, a member was looking for "a little app that would allow sound to be turned OFF and ON by simply clicking on an icon in the system tray". This article shows how to achieve that, as well as providing the same OFF/ON audio muting toggle via a single keystroke.
Article
Security updates for Microsoft End of Life operating systems..
This article provides a convenient collection of links to Microsoft provided Security Patches for operating systems that have reached their End of Life support cycle. Included operating systems covered by this article are Windows XP, Windows Server 2003 and 2008 - Both 32 and 64 Bit installs.
Article

How to Fix Bootloader Problem for Windows 10
When you start your Windows 10 PC and got an "Operating system not found" error or just saw "Auto repair for startup" or a blinking cursor with black screen. A loop for Auto repair will start but fix nothing. You will be panic as there are no backup of your document. How can you fix the problem?
Article

The world is on the move: Electronic commerce to Connected commerce
For both online and offline retail, the cross-channel business is the most recent pattern in the B2C trade space.
Article

For Windows: Here are top 10 Duplicate File Finder Tools that you need to know
Today, still in the boom of Apple, PC's and products, nearly 50% of the computer users use Windows as graphical operating systems. If you are among those users who love windows, but are grappling to keep the system's hard drive optimized, then you should read this article.
Article

Is Your Personal Computer Really At Risk Of Virus Threats?
Operating system developers such as Microsoft and Apple have …
Article

How to Resolve PDF Error – "The File is Damaged and Could Not Be Repaired"?
Are you looking for the perfect solution to fix the error message "The File is Damaged and Could Not Be Repaired"? Then, go through this post and know the step by step process to resolve the error message.
Article

AutoHotkey - Getting Started
AutoHotkey is an excellent, free, open source programming/scripting language for Windows. It started out as a keyboard/mouse macros product, but has expanded into a robust language. This article provides an introduction to it, with links to additional resources for EE members who want to learn more.
Article

Scanners and Cameras Applet in Windows 7, Windows 8, Windows 10
In Windows XP and Vista, the Scanners and Cameras applet was in Control Panel. In Windows 7, 8, and 10, it is no longer in Control Panel. However, it is still on the system. This article documents its location and discusses creating a shortcut for it, thereby providing an easy way to run it.
Article

Upgrade Windows XP to Windows 7
April 8, 2014 Windows XP will lose support…

















