Security
--
Questions
--
Followers
Top Experts
I am a college student in China, and I want to contact foreign technical forums and articles in order to improve my professional skills and English ability. Do you have any recommended websites, articles or videos? My area of interest is mainly developing security products in python, security scripts.In the future, I want to become a security R&D engineer, developing waf, vulnerability scanning and other security products. If you have relevant suggestions for me, I would be most grateful!Because my English is not very good, so the appeal content is translated, if there is any ambiguity, please forgive me
Zero AI Policy
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
- Coursera - Online courses on Python and cybersecurity
- Cybrary - Cybersecurity training and community resources
- Infosec Institute - Learning paths in Python and cybersecurity
- DEV Community - Articles and community for developers
- Snyk - Security best practices for coding
- Python.org Forums - Official Python community forums
- GitHub - Open-source repositories on Python security
- DeepSource - Code security analysis and best practice articles
- Aptori.dev - Security cheat sheets and tips for developers
It's great that you're looking to enhance your skills in security development. Here are some recommendations tailored to your goals:
Websites & Forums:
Stack Overflow: An excellent platform for Python and security programming questions.
Security Stack Exchange: Perfect for discussing security concepts and challenges.
GitHub: Check out open-source security projects and contribute to improving your skills.
BleepingComputer: For security news and technical articles.
Videos & Articles:
YouTube Channels:
"HackerSploit": For free Python security programming, WAF, and vulnerability scanning tutorials.
"John Hammond": An excellent resource for hands-on security scripting and understanding security concepts.
Experts-Exchange:
Expert-Exchange: The community has valuable content on security and development. You can follow experts like Madunix for curated articles and insights: Experts-Exchange.
Technical Certifications:
CompTIA Security+: An excellent foundation for security concepts and practical skills.
CompTIA Cloud: To understand security in cloud environments.
ISC² CC (Certified in Cybersecurity): Great for starting in security with a focus on essential knowledge.
CISSP (Certified Information Systems Security Professional): For more advanced Security.
Python:
Check out Dr. Lerner's Python Courses
https://store.lerner.co.il/advanced-python-bundle
https://store.lerner.co.il/live-classes.
Check the following links to improve your security skills:
https://www.offensive-security.com/blog
https://nakedsecurity.sophos.com
http://taosecurity.blogspot.com
https://www.linkedin.com/learning/
https://www.pluralsight.com/learn
Stay in touch with your local InfoSec community and to hear the latest in technical wizardry, industry intelligence, and thought leadership that include security. Join their mailing list and events
https://www.sans.org/get-involved/
https://www.sans.org/mlp/community-night-events/
Learn insights from PyPI infrastructure and operations, including the creation of a new “PyPI Safety & Security Engineer” role.
https://blog.pypi.org/tags/#security
Appreciate the Software supply chain security community - shared goals of improving software supply chain security and codifying best practices for development, deployment and governance
Articles, White Papers, Technical Write-Ups and more authored by members of the GreySec community.
https://github.com/greysec-security-forums
Going for associate level skill build up
https://owasp.org/www-project-application-security-curriculum/
https://hackerassociate.com/owas-offensive-web-attack-security/
https://learn.snyk.io/learning-paths/security-for-developers/
https://www.isc2.org/certifications/associate






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
There are really great answers above. An additional piece of advice that I would give is to get some schooling inside of the US on an education VISA. This is going open a large number of doors for you. Leveraging your multilingual skills would be wise as well. You can likely find opportunities that require the ability to speak both your language, and ours. That puts you in a fairly narrow pool.
If a company is working on an outsourcing software development to 3rd party, you have to ensure that robust security measures are in place to protect sensitive data and code. Check ISO 27001 is an Information Security Management Systems (ISMS) standard. It helps secure data and intellectual property management when applied to an offshore development context.
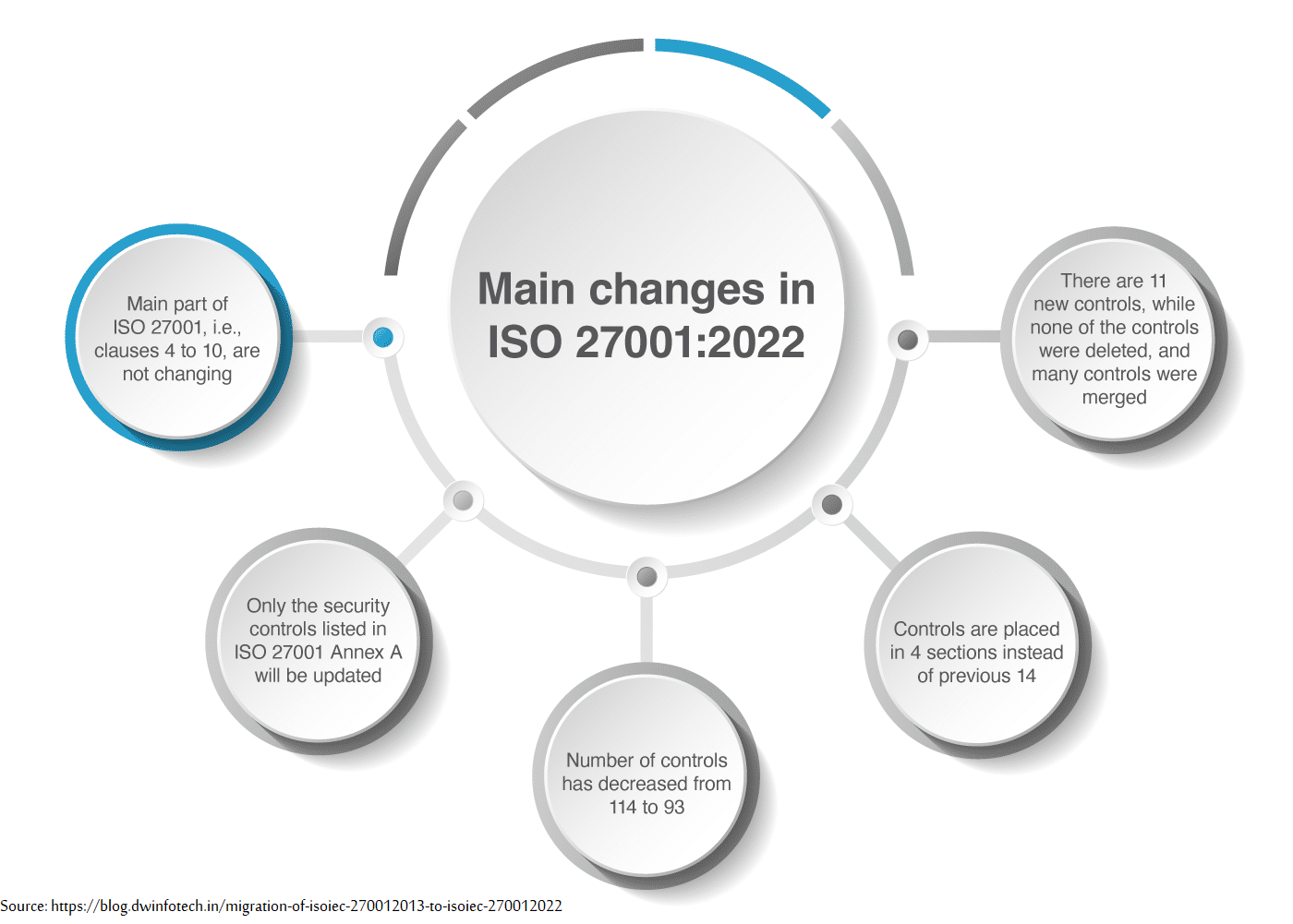
Here are some ways ISO 27001 relates to offshore development:
Risk Management: To detect and evaluate potential security threats, ISO 27001 requires a risk assessment. This is essential in offshore development because several dangers include unauthorized access, IP theft, and data breaches.
Security Controls: Annex A of ISO 27001 lists 114 security controls [Annex A of ISO 27001: 2013 comprises 114 controls] [Transitioning to ISO 27001:2022 - The first significant change is the ISO 27001 controls list, previously 114, they are now 93 in the 2022 standard. Of the 114 controls, 35 remain unchanged, 23 have been renamed, 57 are grouped into 24 (for clarity), and 11 new security controls have been created]. When put into practice, these controls can aid in safeguarding information assets in an offshore development scenario.
Vendor management: In an offshore development project, the vendor or outside development company is an additional team member. Guidelines for managing the security of assets accessed by suppliers are provided by ISO 27001.
Data protection: Handling sensitive data is a standard part of offshore development. Organizations are required by ISO 27001 to have data protection measures, data life cycle, and data classification in place to guarantee the privacy, accuracy, and accessibility of data.
Business Continuity: ISO 27001 mandates the preparation of business continuity plans. This is relevant for offshore development as any disruption can lead to significant project delays.
Legal Compliance: Offshore development might involve dealing with data across multiple jurisdictions with varying protection laws. ISO 27001 can help ensure compliance with these legal requirements.
Trust and Credibility: An ISO 27001-certified offshore development center can offer clients confidence in their information security practices, which can be crucial in building trust.
https://csrc.nist.gov/Projects/ssdf
https://www.iso.org/standard/27001
https://www.itgovernance.co.uk/blog/iso-27001-the-14-control-sets-of-annex-a-explained
https://www.itgovernance.co.uk/iso27001-and-iso27002-2022-updates
https://www.experts-exchange.com/articles/37731/Information-Technology-Audit-in-Nutshell.html
https://www.experts-exchange.com/articles/37693/Zero-Trust-Begins-With-Identity.html
https://www.experts-exchange.com/articles/37654/Guidelines-for-Adequate-Cyber-Hygiene.html
https://www.experts-exchange.com/articles/37631/Transform-From-Trust-to-Zero-Trust.html
https://www.experts-exchange.com/articles/35333/RISK-ASSESSMENT-METHODOLOGY.html
https://www.experts-exchange.com/articles/33451/Building-a-Robust-Security-Awareness-Program.html
https://www.experts-exchange.com/articles/33288/Secure-SDLC-Principles-and-Practices.html
https://www.experts-exchange.com/articles/33330/Threat-Modeling-Process-Basics-and-Purpose.html
https://www.experts-exchange.com/articles/39303/ISO27001-From-Compliance-to-Certification.html
Security
--
Questions
--
Followers
Top Experts
Security is the protection of information systems from theft or damage to the hardware, the software, and the information on them, as well as from disruption or misdirection of the services they provide. The main goal of security is protecting assets, and an asset is anything of value and worthy of protection. Information Security is a discipline of protecting information assets from threats through safeguards to achieve the objectives of confidentiality, integrity, and availability or CIA for short. On the other hand, disclosure, alteration, and disruption (DAD) compromise the security objectives.
Create your account and start contributing!