RISK ASSESSMENT METHODOLOGY
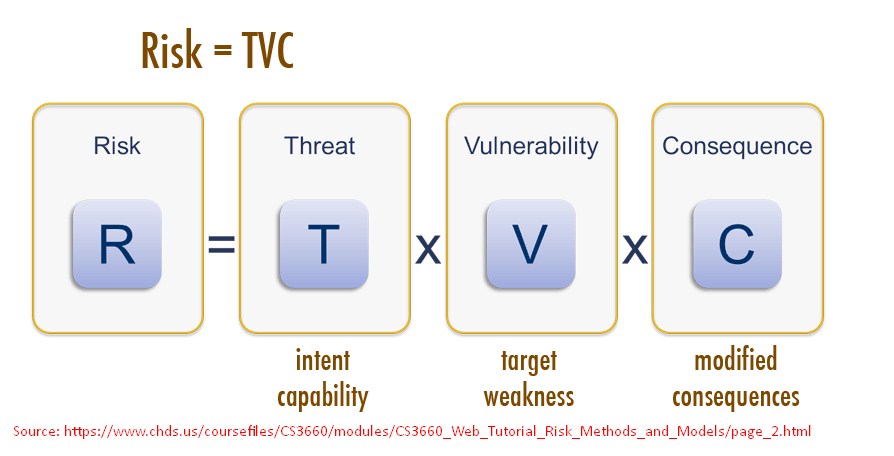
Risk Equation
Risk is often associated with losing a system, power, or network, and other physical losses.
However, Risk also affects people, practices, services, and processes. Although there seems to be unlimited possibilities and variations in the types of attacks that may be staged, unfortunately, the time and resources you can devote to securing an asset are not unlimited.
| Risk = Threats × Vulnerabilities × Consequences
|
|
|
|
By estimating the extent of the three factors comprising the Risk, you can determine the extent of the Risk, which will guide your decision to deal with it. For example, even though a particular vulnerability is easy to take advantage of and the threat of someone taking advantage of it is high, if the consequences are trivial or non-existent, you might deem the risk acceptable and prevention measures to be unnecessary.
On the other hand, if the vulnerability and threat are low, but the consequences are relatively high, you might deem the Risk unacceptable and choose to spend the time and effort to implement safeguards.
Risk is managed rather than outright eliminated. That is why risk management is a process of understanding what risks you can take, as long as the reward is worth the Risk.
Risk Management
Risk Management is an ongoing process; it is a cyclical process of identifying, assessing, analyzing, and responding to risks.
Risk Management identifies:
- The points where particular attention is required,
- Any arrangements to be put in place to reduce risk exposure
Risk Management is considered to be composed of:
|
Risk Management = Risk Assessment + Risk Treatment |
|
|
|
Risk Assessment: |
|
|
|
|
|
|
Risk Treatment: |
|
|
|
Risk Assessment
Risk assessment is a method for identifying and assessing risks for a given perimeter and period and putting them into a hierarchy. It defines the structure’s level of exposure to risks.
When part of an entity structure has been the subject of one or more risk assessments, these assessment results must be considered when defining the Business Continuity strategy.
The risk assessment is an essential part of the overall Risk Management process. During Risk Assessment, understanding the business information security requirements and identifying the risks to business assets and functions is vital.
The risk assessment process includes:
- Risk identification
- Risk analysis
- Risk evaluation
The risk identification phase includes the following activities:
- Identification of assets
- Identification of legal and business requirements
- Identification of significant threats and vulnerabilities
- Identification of existing controls
During the Risk Analysis phase, the following actions and activities are taking place:
- Valuation of the identified assets
- Assessment of the likelihood of the threats/vulnerabilities to occur
During the Risk Evaluation phase, the following actions and activities take place:
- Risk Calculation
- Evaluation of the risks
Risk Treatment
The Risk treatment plan shall address handling the risk. You should develop the Risk Treatment Plan that will:
- Define the treatment option for each identified Risk
- Select the appropriate controls
- Re-evaluate the Risk Level after the implementation of the controls
Risk Analysis Methods
The risk analysis methods used to calculate for exposure can fall into one of three categories:
Qualitative analysis
This method uses descriptions and words to measure the likelihood and impact of Risk. For example, impact ratings can be severe/high, moderate/medium, or low; and likelihood ratings can be likely, unlikely, or rare. Qualitative analysis is generally scenario-based. A weakness of qualitative risk analysis lies with its sometimes subjective and untestable methodology. The goal of qualitative assessment is to rank the risks.
Quantitative analysis
This method is based entirely on numeric values. Quantitative analysis may be weak in situations where Risk is not easily quantifiable. The goal of quantitative analysis is to calculate the probable loss for every Risk.
Semi-quantitative analysis
This method exists because a purely quantitative risk assessment can not exist; A semi-quantitative analysis attempts to find a middle ground between the previous two risk analysis types to create a hybrid method.
Metrics for Risk Management
Assets can be identified and categorized into different groups and categories. Asset categorization depends on the asset's nature as different types of assets have different types of vulnerabilities and threats that might affect it.
The categorization of assets for the organization is as follows:
- Technology Assets
- Information Assets
- People Assets
- Physical and environmental Assets
- Intangible Assets such as reputation, knowledge, experience, Image, and brand
To apply protection for assets, it is necessary to assess their values regarding their importance to business and their potential values in different business areas.
To express asset values is to use Business Impact Analysis (BIA) by calculating the importance of the asset in case of being subject to unwanted incidents, which could be:
- Disclosure of information (Loss of Confidentiality)
- Unauthorized Modification (Loss of Integrity)
- Non-availability and/or destruction (Loss of Availability)
The assessment is based on a series of interview questionnaires distributed to the information assets owners to confirm the value and the criticality of the information assets.
At a later stage, assign the appropriate controls to increase security, considering that each impact could differently affect the asset. The impact is measured in terms of (CIA) Confidentiality, and Integrity, and Availability. The impact could be categorized into two types:
- Direct impact on the asset: when an incident affects the asset directly, it could cause a direct impact on the information asset in terms of loss of (CIA) confidentiality, integrity, and availability; so the consequence could be the destruction of the confidentiality, integrity and/or the availability of the information asset.
- Indirect impact on the asset: this scenario could happen when a loss of financial market share is encountered by Breaching the security of a particular asset.
The C.I.A scale will be from 1 – 5 scale regarding the below loss criteria: Scale for Confidentiality, Integrity, and Availability.
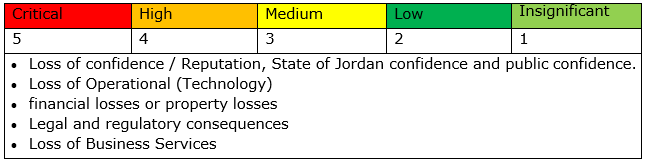
Business Impact Analysis (BIA) methodology: is based on a qualitative approach, and the impact is described in terms of Critical, High, Medium, Low, and Insignificant impacts. As shown in the example below:
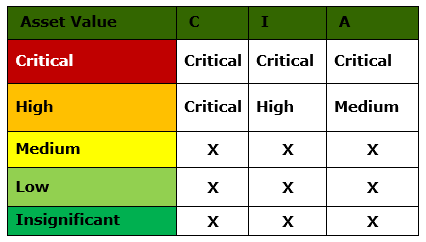
For each Asset, a rating is applied based on the impact of Breach of Confidentiality (C), Integrity (I), and Availability (A). The overall impact on an asset “Asset Value” is considered the AVERAGE value of the (C), (I), (A) values.
- Critical Assets: The asset has extremely high tangible or intangible value, and its compromise will have a very serious impact on the organization with an adverse effect on its critical business processes and Services.
- High-Value Assets: The asset has high tangible or intangible value, and its compromise will have an essential negative reputation, financial, operational, or legal consequences on the organization with an adverse effect on its critical business process and Services.
- Medium-Value Assets: The asset has moderate tangible or intangible value, and its compromise will have a noticeable negative reputation, financial, operational, or legal consequences on the organization with a medium effect on its critical business process and Services.
- Low-Value Assets: The asset has low tangible or intangible value, and its compromise will not have a significant negative reputation, financial, operational, or legal consequences on the organization.
- Insignificant Value Assets: The asset has a very low financial, technical, or legal value, and its compromise will not have any negative reputation, financial, operational, or legal consequences on the organization.
Identification of Threats and Vulnerabilities
Develop a centralized registry of IT risks, documenting their source and nature, area if impacted, response strategies, key risk indicators, and mitigating controls.
Classification and mapping of risk events to business risks and compliance requirements provide a full context for IT risks. Maintain a library of qualitative and quantitative assessment factors and relate them to the risks.
The threats identified could be categorized as follows:
- Human threats
- Environmental threats
- Technical and operational threats
- Cyber Threats
The threats could be produced from:
- Deliberate threats
- Accidental threats
The vulnerabilities identification identifies the weaknesses related to:
- Hardware, software, or Network equipment and facilities.
- Business operations and service delivery.
- Physical environment.
- Personnel, management, and administrative procedures and controls of security controls.
- Violation of Information System policy
- Lack of Security Assessment
- Lack of Awareness session for employees
- Systems vulnerability
- Lack of configuration standards
- Lack of top management support
Assessment of Threats
Risk assessments and computations based on configurable Risk evaluating methodologies and flexible what-if analysis functionality, enabling the organization to prioritize its response strategies for optimal risk/reward outcomes.
The organization shall utilize a library of risk assessment questions for conducting surveys, questionnaires, and interviews with the business as well as the technical owners of the information assets based on control statements and procedures that are mapped to various regulations, standards, and frameworks to driving robust Risk and compliance reporting.
Taking the following points into consideration:
- Understanding data comes from various levels of understanding of the risks.
- How vital information is to the organization versus individual level?
- How important from technical versus data. (If there is remote access with root or privilege escalation, that is more important than the data loss, but a user would not always understand that and how data is siloed/protected. Which servers accessible).
- Observer Feedback from stakeholders, do not ignore the user's inputs. For example, a particular company has been informed of a remote backdoor exploit for nearly a year with their VPN solution and has not fixed it.
Having understood the extent of potential threats, the next stage identifies just how likely such problems are to occur. Threats and vulnerabilities identified shall be assessed and rated according to the probability/likelihood and the Impact/Harm that it might cause to the asset.
To calculate the actual value of the threat, the following threat factors shall be identified and evaluated:
- Impact: the impact on the asset by being exposed to the mentioned threat.
- Probability: the probability of that threat affecting the asset.
The impact should be calculated in terms of (CIA) and should have more value than the threat's probability.
The overall value of impact and probability is categorized in the following table:
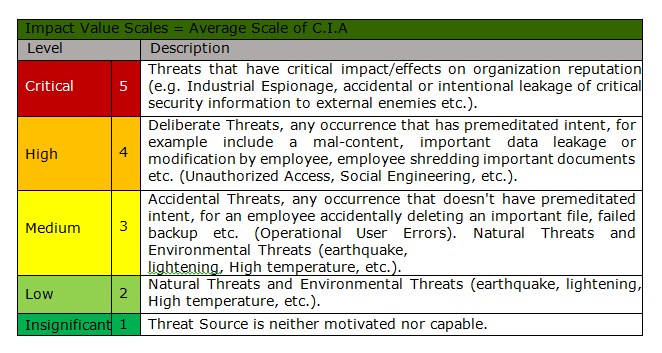
Likelihood of Occurrence
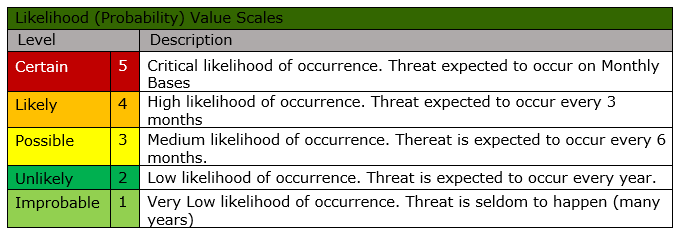
Risk Calculation and Evaluation
The risks are calculated from the combination of asset values expressing the likely impact resulting from a loss of Confidentiality, Integrity and/or Availability, and the assessed likelihood and impact of related threats and vulnerabilities to come together and cause an incident. The calculated risk levels provide a means to rank the risks and identify those risks that are most problematic for organization.
After calculating the value of the Risk and based on the effectiveness of the existing controls, addressing all gaps. The vulnerability's value will be reduced to reflect the improvement (reduction in risk) that the organization is gaining.
The risk shall be calculated on a Zero Control approach; that is calculating the value of the risk without considering the controls implemented by assigning the vulnerability a value of 5 (Critical) to measure the real value of the risk exposed to.
The risk shall be afterwards evaluated by assigning the real value of the vulnerabilities, the value of vulnerability should be measured against the existence of controls and its level of implementation, the criteria for evaluating the vulnerability is as follows:
The value of vulnerability should be measured against the existence of controls and its level of implementation:
- The controls not addressed: The control does not exist and needs to be developed.
- The control is partially implemented: the control selected to address such threat is either implemented, but there is no documentation of implementation or guidance for other users to implement this control (Lack of Policy and/or Procedure); or the control is documented but not implemented: the required documentation exists but not implemented by the organization.
- The control implemented and effective: the control is implemented, and relevant Policies and Procedures exist, and the effectiveness of the control is measured and evaluated to make sure that the control selected is reducing the Risk.
The following formula shall explain the method of Risk calculation (MoR: Measurement of Risk):
Risk = Impact x Likelihood of Occurrence
The Risk Level shall be calculated according to the following table:
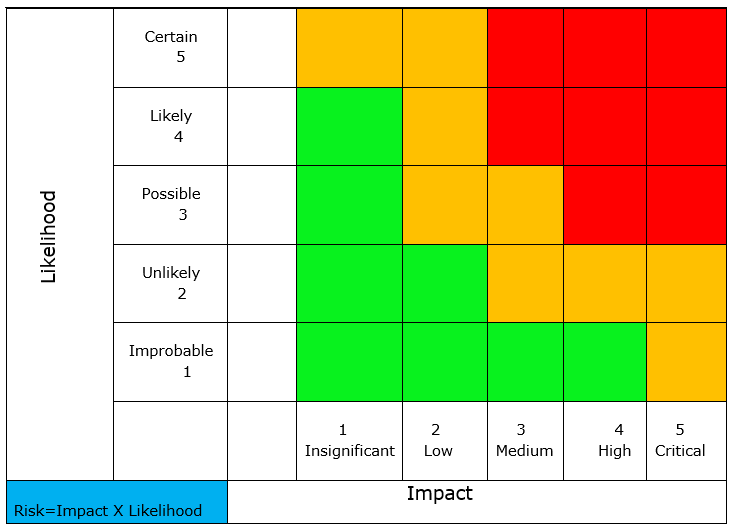
The risk, afterwards, is ranked according to the following table:
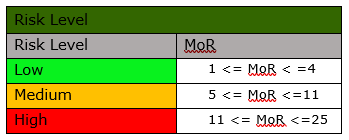 The organization can mitigate the risks faced within its infrastructure according to the following criteria:
The organization can mitigate the risks faced within its infrastructure according to the following criteria:
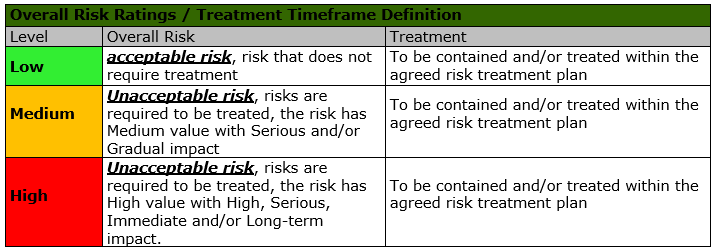
Risk Response Techniques
Once risks are identified and prioritized:
- Controls to mitigate those risks needs to be defined.
- Controls shall be associated with relevant policies and procedures.
- Develop assessment plans to evaluate and ensure the controls' effectiveness and assign to owners the act of implementing the selected controls based on their roles and responsibilities.
The organization, through the risk and compliance committee, took the decision that they will decide the acceptable risk level based on the approved risk appetite (e.g., rate "Low"); risks with a value above the acceptable level of risks needs to be addressed and mitigated depending on the value of the Risk and the available controls to be implemented.
How an organization reduces or removes Risk is based on the thresholds established for different
risks, and it is entirely dependent on the risk appetite of the organization. The following
describes the four possible approaches to risk response.
- Avoid the Risk
This means that Risk has been reduced to zero. This strategy cannot be applied to all risks. Total risk avoidance is virtually impossible in any enterprise, as it would necessitate that you remove many vital systems that your business requires to function. At the end Risk is nearly never reduced to zero, merely lowered or shifted.
- Transfer the Risk
Moves the responsibility for managing Risk to another organization, such as an insurance company or an outsourcing provider. They may be better at it, and there is a price also.
It also opens you up to new risks, previously not factored in. (At least doubles your risk of information privacy, fraud or other transferred information/processes) and lowers your control of security of your information.
- Mitigate the Risk
Proper controls should be implemented to reduce the risks to the level that has been identified by the organization management as acceptable. Security requirements must be considered related to that particular Risk (i.e., the threats and vulnerabilities, legal and business requirements) at the time of control identification. After the risk treatment plan(s) have been implemented, there will always be risks remaining. It should be assessed to know how much the risk treatment plan helped reduce the Risk and the residual risk value that remains after the mitigation. Residual Risk is difficult to assess, but an estimate should be made to ensure that sufficient protection is achieved (considering the results of internal audits and metrics).
- Accept the Risk
Not all risks can be avoided; likewise, not all risks can be transferred or mitigated. The organization must decide what level of Risk is unlikely or does not have enough potential for harm to warrant the extra effort and cost in your organization. Some risks will likely exist for which either the organization can not identify controls or the cost of implementing controls outweighs the potential loss through the Risk occurring. In this situation, a decision shall be made to accept the Risk and live with the consequences if the Risk occurs. The organization should document these decisions to be aware of its risk position and knowingly accept the Risk.
Risk and control assessment issues and findings shall be communicated to the appropriate personnel for mitigating through remediation action plans. As deficiencies are addressed through corrective actions, residual risk scores shall be updated regularly to reflect the true risk level.
When mitigating risks, several options shall be explored to identify the best approach and the most effective method of mitigating and designing the appropriate action plan to treat the risks.
Risk Reviews and Re-Assessments
Risk activities and results shall be reported in risk reports to enable the Risk Management Team to follow up with such risks and the status of implementing the suggested action plan. Those reports shall provide clear visibility into key risk indicators and event data for the management.
Technical and executive reports shall be generated by collecting data relating to technology assets, third-party products, and assessments for various processes for a comprehensive view of the organization's IT risk profile.
Implemented security controls should be regularly monitored and reviewed. The activities include:
- Checking of log files
- Modifying parameters to reflect changes and additions
- Reviewing controls and compliance with them
- Updating controls, policies, and procedures with new versions
The results from security risk assessment and management review need to be regularly checked for changes. Re-Assessment should be conducted whenever:
- There is a new business function (New Information Assets)
- Significant changes to existing information assets
- New regulations and legislations
- Changes in the vulnerabilities and threats values
- New risks identified.
- Measure the effectiveness of controls implemented.
An Action should be taken as a result of monitoring, reviews, and audits. These actions need to be independently verified to ensure that they:
- Relate to the identified root cause and appropriately address the problem
- Have been implemented within the assigned time frame
- Are effective in preventing recurrence of the problem
Key factors for success
The following points are considered as factors for a successful Risk management program:
- ongoing, visible support of senior management, relayed by management at all levels,
- allocation of the resources required to conduct the campaign,
- consultation of some target personnel when developing the campaign,
- consideration of other planned awareness-raising initiatives to avoid saturation,
- maintenance of the training and awareness-raising effort over time (repetition principle).
References
- ISO/IEC 27001:2013
- ISO/IEC 27002:2013
- ISO/IEC 27003:2017
- ISO/IEC 27004:2016
- ISO/IEC 27005:2018
- ISO/IEC 27000:2018
- ISO 31000
- https://www.isaca.org/resources/isaca-journal/issues/2017/volume-3/it-asset-valuation-risk-assessment-and-control-implementation-model
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (2)
Commented:
Commented: