Citrix XenDesktop 7.6 Citrix Policies Disable Peripherals
Holistic technology infrastructure strategy, design, engineering and implementation that is highly scalable, secure, optimized, automated
Published:
Browse All Articles > Citrix XenDesktop 7.6 Citrix Policies Disable Peripherals
Citrix XenDesktop 7.6 Citrix Policies Disable Peripherals
Citrix XenDesktop 7.6 Citrix Policies Disable Peripherals
This article shows the settings I use to "lock down" the virtual desktop with Citrix Policies configured using the Citrix Studio.The policies apply to XenDesktop or XenApp.
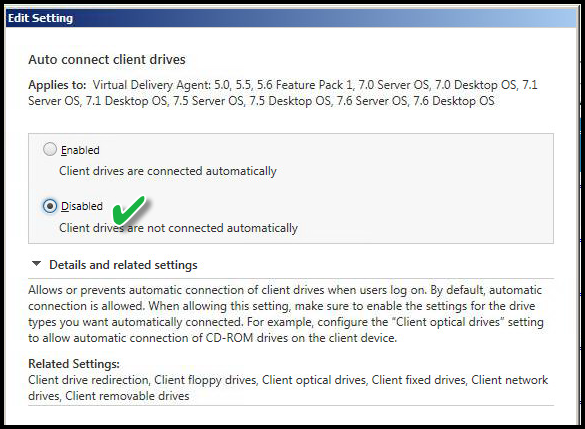
AUTO CONNECT CLIENT DRIVES
Value: Disabled
Value: Disabled
 Explanation:
Explanation:
This setting disables mapping the local workstation drives when logging on to XenDesktop. Otherwise, the user would open "My Computer" or "Explorer" in the virtual desktop and see both a C: drive and the V: drive mapped to C: drive of the workstation of origin. This will apply to all users at login.
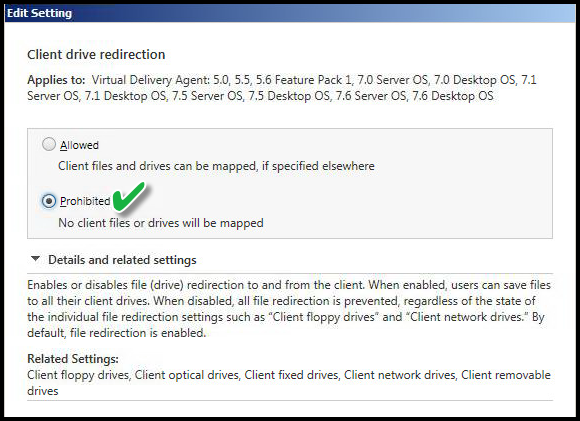
CLIENT DRIVE REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
Prohibited - This setting prevents users from saving files to the device of origin. The setting above disables the automatic drive mapping feature of Citrix to map client drives to different drive letters. That setting above does not prevent users from opening command prompt and manually mapping drives -- hard drives, USB drives, a CD Burner, Floppy drives, and so on. In addition, this disables "mapped drives" on the device of origin. The Virtual Desktop might reside in Active Directory Organizational Unit (OU) that blocks mapped drives having no impact on the workstation of origin. The workstation initiating the connection to the Virtual Desktop might have multiple drives mapped such as Home Drive, Group Drive, or Department Drives. This setting prevents any such drive mappings to carry forward. It does not prevent the user from switching back to their original desktop session and using those drives. It merely prevents the user from accessing those same drives in the Virtual Desktop session.
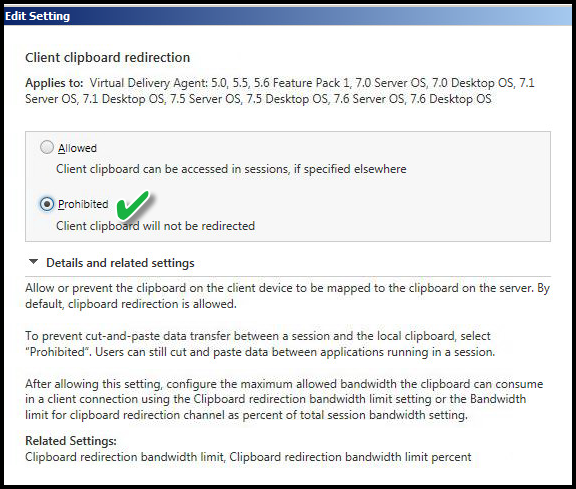
CLIENT CLIPBOARD REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables the ability to copy something on the client workstation of origin and paste in the virtual desktop and vice versa. This could be text, graphics or files. It does not prevent clipboard use in the Virtual Desktop session or the workstation of origin session.
CLIENT COM PORT REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables the COM port redirection from the client device to the virtual desktop session. The COM port is rarely used, but I want to make sure it is prohibited.
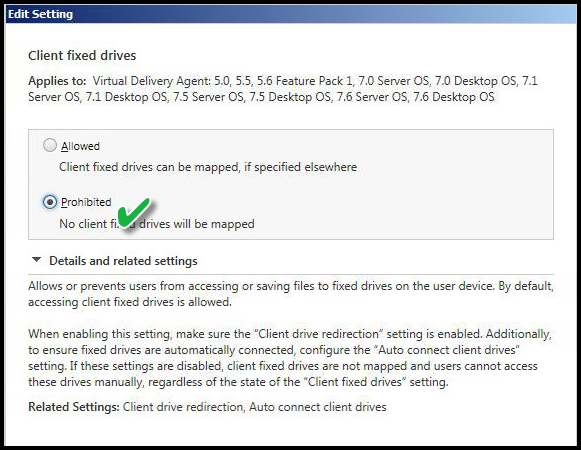
CLIENT FIXED DRIVES
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting is related to the previous one but is also an override specific to "fixed drives" such as physical hard drive in the workstation of origin. If this setting "Prohibited" it would not matter if "Client drive redirection" is "Allowed". "Auto connect client drives" would not function for fixed drives but would work for Network drives. Hence, using advanced configuration, I can prohibit C: / D: drive on the workstation of origin from being accessible but the mapped drives to network share are "Allowed".
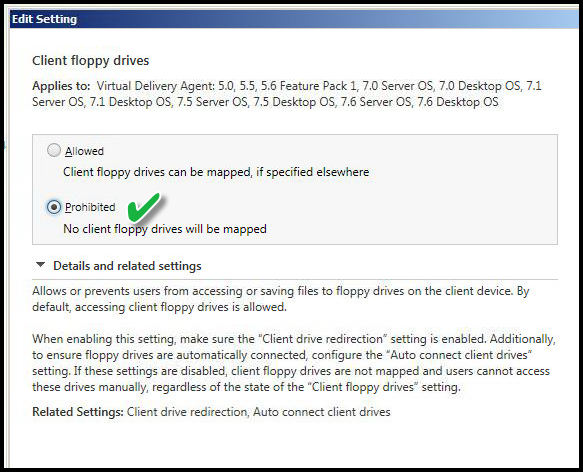
CLIENT FLOPPY DRIVES
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables access to the workstation of origin floppy drive. This is becoming less of a problem as floppy drives are phased out of new computers and is not a concern on Thin Client devices.
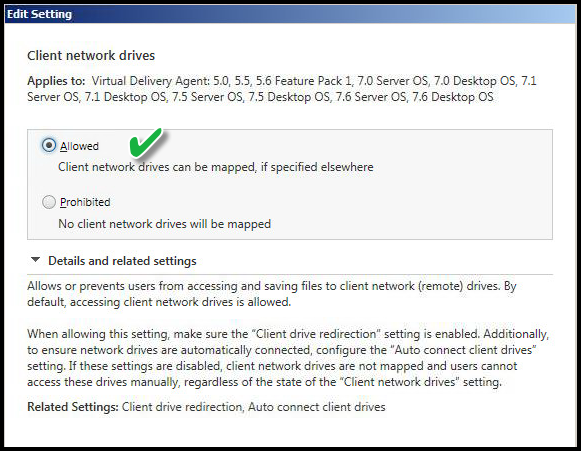
CLIENT NETWORK DRIVES
Value: Allowed
Value: Allowed
 Explanation:
Explanation:
This allows the workstation of origin "mapped drives" to traverse the connection for use in the Virtual Desktop session. The previous setting disabled mapping physical drives and floppy drives. This is an advanced configuration using Citrix Policies and helps to show the power of Citrix policies. This makes sense in a scenario where I do not wish to link Group Policy objects having specific drive mappings or run any login scripts during the Virtual Desktop login phase. These LAN-connected users already have Home drives, Group Drives and possibly custom mapped drives on their workstations of origin. This setting allows me to map all those client mapped network drives without running any login scripts or custom Group Policy Objects linked to the Organization Unit (OU) of the Virtual Desktops.
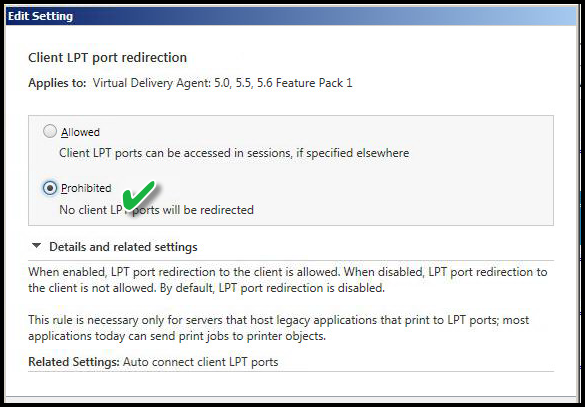
CLIENT LPT PORT REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables the ability to map workstation of origin printers attached to LPT ("parallel") port. This pertains to legacy printers and is rarely used, but some Terminal Emulation programs still use the technology.
Reference: https://en.wikipedia.org/w
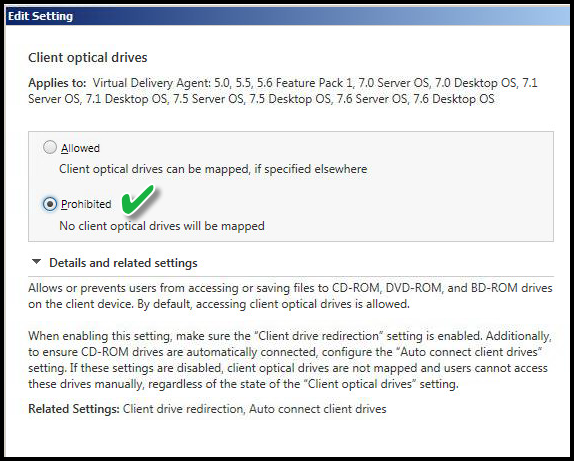
CLIENT OPTICAL DRIVES
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables or prevents the use of any optical drive by way of the workstation of origin. This prevents those type of drives in the Citrix Virtual Desktop session.
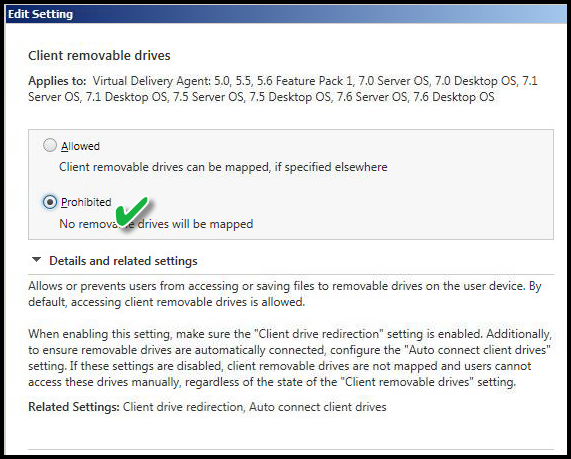
CLIENT REMOVABLE DRIVES
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This policy disables the ability to access any remote or removable drive such as USB connected drive.
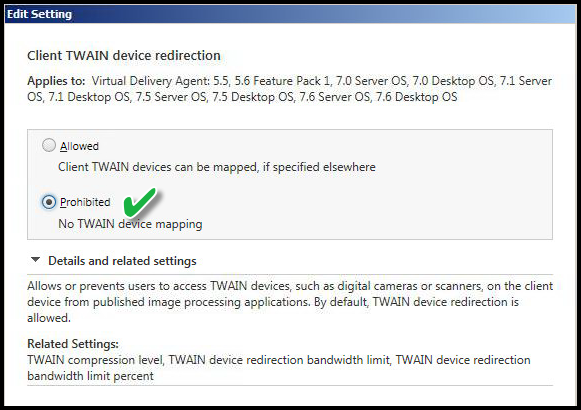
CLIENT TWAIN DEVICE REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables TWAIN devices such as cameras or scanner use while in the Virtual Desktop session. The end-user can still revert to their local session, but any such devices will not work in the Virtual Desktop session.
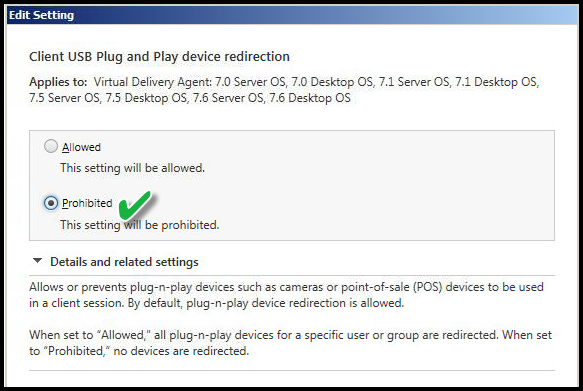
CLIENT USB PLUG AND PLAY DEVICE REDIRECTION
Value: Prohibited
Value: Prohibited
 Explanation:
Explanation:
This setting disables any activity related to adding or removing USB P&P devices from the workstation of origin. Example: Adding a new camera device to the workstation of origin might result in the local device installing a driver and software. If this were allowed in the Virtual Desktop session both sessions would cause the Virtual Desktop session to attempt installation as well.
DIRECT CONNECTIONS TO PRINT SERVERS
Value: Disabled
Value: Disabled
 Explanation:
Explanation:
I disable this setting because I'm enforcing the Universal Print Driver for all Virtual Desktop sessions.
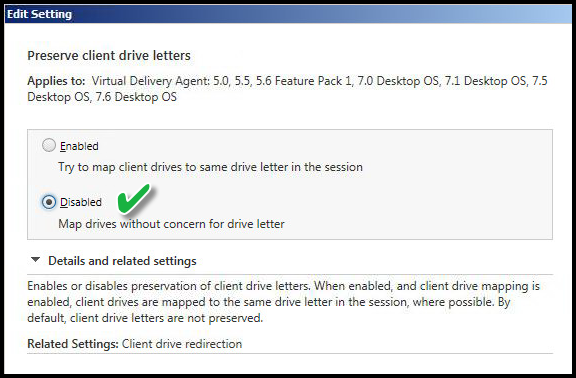
PRESERVE CLIENT DRIVE LETTERS
Value: Disabled
Value: Disabled
 Explanation:
Explanation:
I disable this setting as part of the overall "drive mapping" settings. If client drive mappings were allowed it refers to the workstation of origin and attempts to use those same "drive letters" to the Virtual Desktop session.
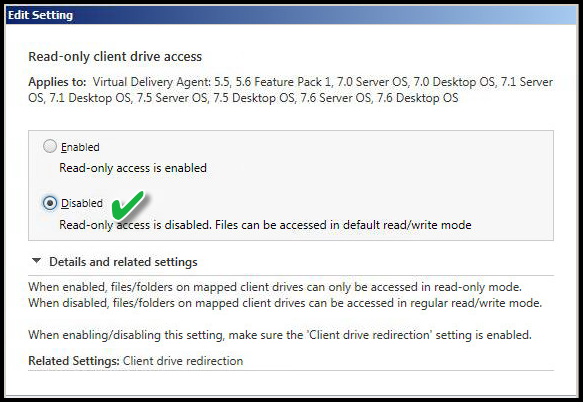
READ-ONLY CLIENT DRIVE ACCESS
Value: Disabled
Value: Disabled
 Explanation:
Explanation:
This setting is not applicable but is shown here for demonstration purposes. If I have enabled fixed or removable drive redirection, the default is read/write, but this is not a NTFS or share permission. This policy is enforced between the Citrix client and server. So if this is "Enabled", it would allow only read access, and writing files would be disabled regardless of local, direct attached, or removable drives on the end-user device.
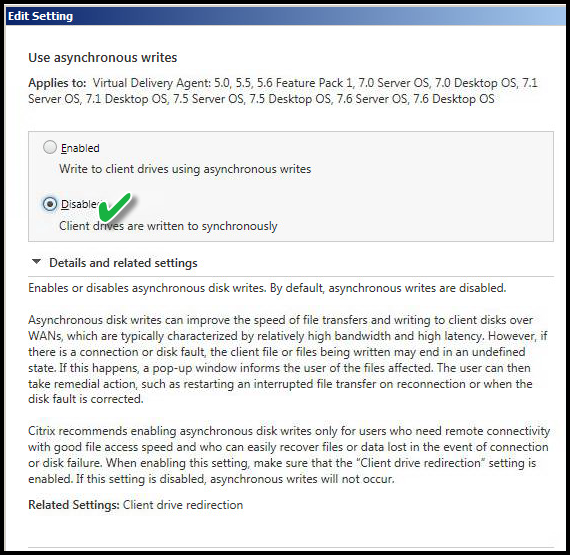
USE ASYNCHRONOUS WRITES
Value: Disable
Value: Disable
 Explanation:
Explanation:
This setting applicable if I allowed drive mappings from workstation of origin to the Virtual Desktop session. This is an example of a setting applied to the specific use case.
SUMMARY
Disabling peripherals demonstrates the power of Citrix policies. Citrix is inherently secure and through proper use of advanced policies is a built-in lockdown utility. Using priority and custom policies I can increase or decrease security footprint using Delivery Groups, Active Directory security groups and other criteria.
ACKNOWLEDGEMENT
Does this shared knowledge provide value? If this article has value, please click on "Good Article" button to your right. Knowing this knowledge is valued by others is motivation to continue sharing. Your support is greatly appreciated.

Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)