Information and Communication Technology (ICT): Risk Management, Compliance, and Audit Triangle
Introduction:
Information and Communication Technology (ICT) has become integral to the daily operations of many organizations. However, with the increasing reliance on ICT comes the risk of internal and external attacks, cyber-attacks, and breaches arising from inadequate business continuity planning for ICT systems and processes or poor processes relating to ICT change management. Organizations must implement effective ICT risk management, compliance, and audit practices to mitigate these risks.
Organizations continuously strive to improve their operations, ensure compliance with regulatory requirements, and enhance overall performance. Audits are critical in achieving these objectives by providing organizations with the tools and techniques to assess and manage internal controls, risk management, and compliance processes.
Every organization is increasingly aware of cyber risk and is seeking to manage it through:
- Policies, procedures, and other administrative controls
- Technology-based controls
- Insurance (aka, risk transfer)
- Risk acceptance
For example, cyber risk is an enterprise-wide risk management issue:
- It is much broader than the certification or compliance such as PCI DSS or HIPAA
- It is a business issue, not only a technology issue
The Risk Management, Compliance, and Audit Triangle is a framework organizations use to manage risks, ensure compliance with regulations and standards, and monitor business processes.
Risk management is a formal organizational process, and it is an integral part of strategic governance, which involves identifying and mitigating risks. Furthermore, risk management ensures the continuing security of any business operation. Compliance ensures adherence to laws and regulations. Auditing monitors and assesses business processes for effectiveness and compliance. These interconnected components help organizations achieve their goals while minimizing negative impacts.
Compliance
Compliance focuses on adhering to applicable laws, regulations, industry standards, and internal policies within the IT environment. It involves establishing and maintaining controls and practices that ensure compliance with legal and regulatory requirements, data privacy regulations, contractual obligations, and industry best practices.
Audit
Audit refers to systematically evaluating and assessing IT systems, processes, controls, and practices to ensure they operate effectively and efficiently and follow established policies and procedures. ICT audits are conducted to validate compliance, identify potential weaknesses or deficiencies, and provide assurance to stakeholders.
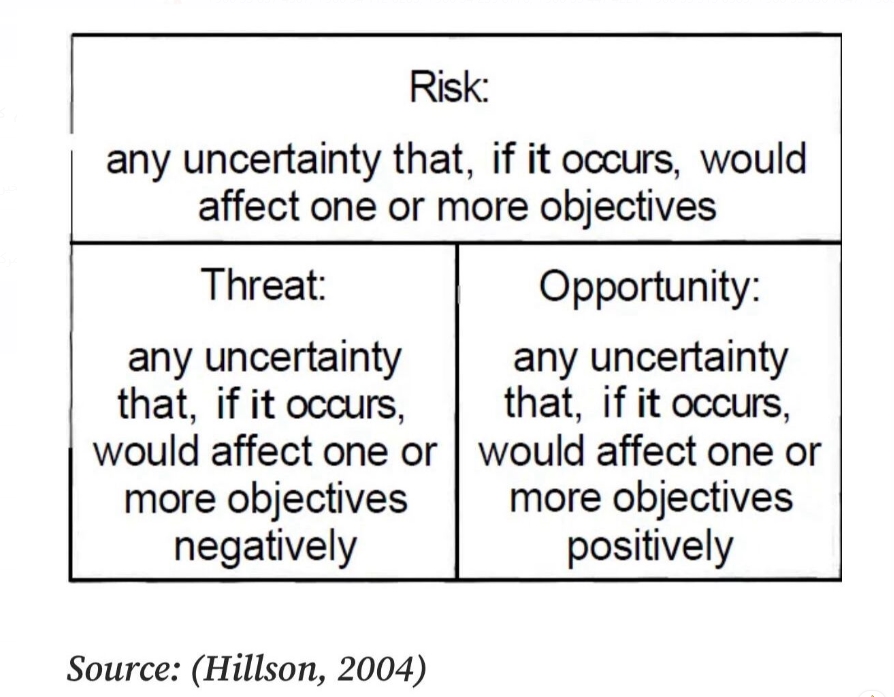
Risk
Risk is the likelihood of a threat agent taking advantage of the vulnerability and the resulting business impact. Risk is categorically bad in cybersecurity, but this viewpoint often conflicts with business operations that view risk as an essential component of growth and improvement. Risk constantly evolves and shifts due to many factors, such as changes in an organization's strategy, changes within the industry, changes by vendor partners, and changes in the software and platforms used daily. Due to the dynamic nature of risk, it must be continually managed.
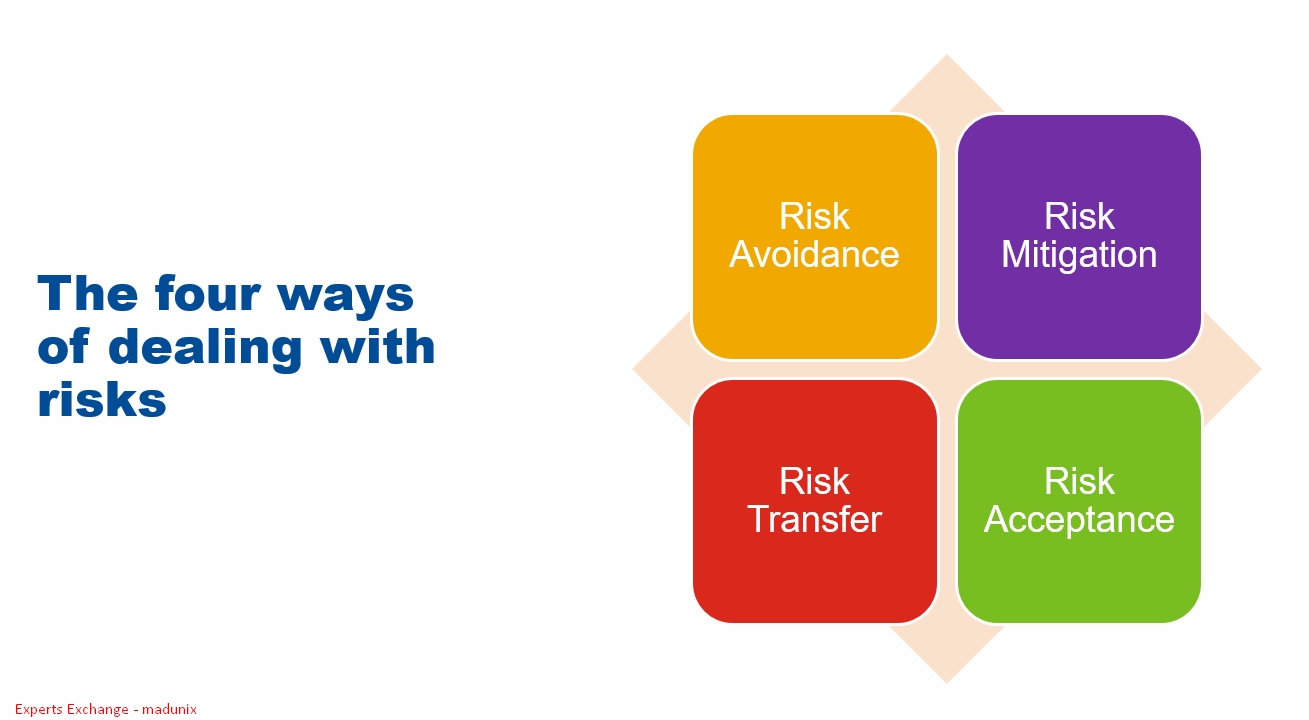
No matter what approach is used, the organization has to formulate a prescribed strategy to address each of its priority risks and decide how they will be handled. The four ways of dealing with risks are:
- Risk Avoidance
- Risk Mitigation
- Risk Acceptance
- Risk Transfer
Good risk management requires appropriate measures that accurately reflect the risk picture. The proper measurement depends on a set of references and tools that decision-makers rely on to decide how to manage risk, called the risk management framework. There are three risk management frameworks, namely:
- ISO 31000
- ENISA Risk Management/Risk Assessment(RM/RA) Framework
- NIST Risk Management Framework (RMF)
Risk Register
Risk management represents an organization's policies and processes to help it locate, describe, and rank risks consistently and repeatedly. One of the tangible outputs of risk management is the risk register. A risk register can be used to measure, at a high level, progress over time. The risk register not only identifies risks but also includes controls designed to limit the potential impacts of each risk item. The iterative process of risk management includes periodic reviews of the risk register to determine the implementation status of each item - for example, analyzing the extent to which the identified controls have been implemented since the last review.
Risk Management
Risk management is the cyclical process of identifying, assessing, analyzing, and responding to risks. This process is not meant to end; as long as information exists, it will need protection. Therefore, without risk management, your security will be passive. Securing your ICT passively will leave you vulnerable to internal and external attacks, including cyber-attacks. These breaches may arise from inadequate business continuity planning for ICT systems and processes or poor processes relating to ICT change management.
Because cost is always a factor in business decision-making, a precise specification of the maximum degree of acceptable risk is necessary to guide decisions about the degree of risk the organization is willing to underwrite. A specification of the maximum level of acceptable risk drives the tradeoff process that requires making a real-world planning decision about risk acceptance for each specific conclusion about the degree of risk will also drive the decision about the practice form of the monitoring process. Consequently, the risk management planning process usually involves the formation of a substantive, usually resource-based, map between each risk and the various options for mitigating it. The actual response will typically be referenced to the risk's practical acceptability level.
Risk management is identifying and assessing risk, reducing it to an acceptable level, and implementing the proper mechanisms to maintain it at that level:
- Threat Event
- Threat Impact
- Threat Frequency
- Recognition of the Uncertainty
- Risk Mitigation
- Annualized Cost
- Cost or Benefit Analysis
Risk Management steps:
- Understand business environment
- Identify threats, vulnerabilities
- Identify existing controls
- Test effective of existing controls to detect and mitigate identified risks
Risk management is a complex organizational function that aims to underwrite the organization's obligation to identify and mitigate project risks. It is an information-gathering and decision-making function. It focuses on understanding all feasible forms of risk, then classifies and assesses those risks to determine their importance.
Risk management ensures that there is sufficient knowledge about each relevant threat available for decision-making. And then, risk management takes the necessary steps to react to and mitigate all priority risks. Risk management also monitors the effectiveness of those mitigations once they have been put in place. Therefore, the performance of a threat assessment is a prerequisite to implementing a formally executed risk management operation.
Nevertheless, the primary purpose of risk management is to sustain a disciplined and systematic set of controls that will respond to the risks that the organization considers a priority throughout the business operation.
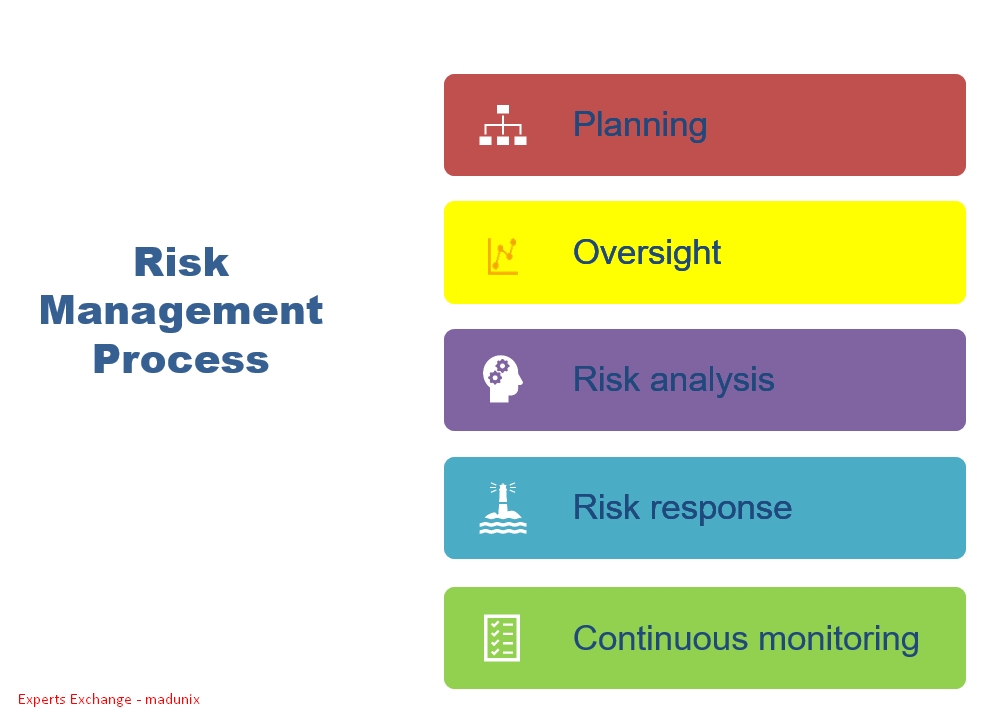
The risk management process typically involves five generic steps:
- Planning
- Oversight
- Risk analysis
- Risk response
- Continuous monitoring
Planning
All of the operational steps of the generic risk management process have to be planned; that is, every one of the day-to-day activities that comprise the organization's explicit risk management strategy has to be scheduled right down to the who, what, when, and where of the execution of each practice.
In addition to providing the information that helps guide strategic decision-making about risks, risk management planning also ensures that a commonly accepted and systematic set of policies and procedures are in place to handle known risks.
A risk management plan is a high-level document detailing the overall approach employed to control the risks the enterprise deems worth addressing. The plan conceived, organized, and managed that set of controls.
The risk management plan shapes the risk management process. The primary role of the risk management plan is to create the framework for the detailed policies and procedures that will comprise the risk management process for that particular organization. The top-level risk management plan provides the context needed to ensure that the organization's overall business objectives and goals are understood and then factored correctly into the decisions about risk. In that respect, the comprehensive risk management plan needs to be crafted in broad, organization-wide terms with the specific details of the approaches to be adopted left to lower-level operational plans. This high-level document must define the comprehensive processes and interrelationships needed to build a complete picture of the organizational risk situation. The ideal would be to create a road map to let executive managers develop the strategies they need to address existing risks.
First, the risk management plan should document the roles and responsibilities of the essential risk management team. The assignment of responsibility should be stated at a high enough level to allow the people on the risk management team to respond flexibly to situations covered in the plan. Nonetheless, the risk management plan has to assign specific authority to the team to act on those situations that are the responsibility of the risk management process. Assigning high-level roles and responsibilities also ensures that the routine supervisory and budgetary authority needed to conduct the process as a regular part of the business is expressly delegated to the team's members.
Environmental considerations are the factors that must be understood to include the risk management process in the overall operating circumstances of the organization. Every risk management process must be designed to fit its particular environment. Accordingly, the design should describe all technical and environmental factors that might impact the risk management process. In that respect, the plan must ensure that the process is correctly aligned with the context of the organization's environmental, sensitivity, and security requirements.
Oversight
The overall purpose of the risk management function is to establish and maintain an appropriate set of controls. All factors that comprise that organizational context be identified and understood to design a practical set of controls. A formal oversight process has to be in place to sustain the security strategy. This process aims to monitor and effectively report the organization's risk situation. An oversight process should be created to continuously and reliably depict the current status of identified risks.
Risk Analysis
The analysis of the probability and consequences of known risks:
- Prioritizes risks and calculates the cost of safeguards
- Compares the cost of protection and the cost of loss
- Identifies and prioritizes high-impact risk factors
- Integratesbsecurity program objectives with business objectives
The type of approach to risk analysis will be decided based on the risk analysis team, management, risk analysis tools, and the culture of the organization.
Quantitative Risk Analysis:
- Requires complex calculations
- Provides credible cost/benefit analysis
- Shows clear-cut losses that can be accrued within one year
- It is challenging to make a decision based solely on quantitative assessment
- It is used for the financial values of tangible assets
Qualitative Risk Analysis:
- Requires a high degree of guesswork
- Provides opinions of the individuals who know the process well
- It does not provide sufficient data to make financial decisions
- It can be used for the priority values of intangible assets.
The organization must deploy and maintain a comprehensive risk analysis function to effectively understand risk. The wall purpose of the risk management process is to mitigate risk. Risk analysis is the information-gathering function that provides the necessary understanding of the nature of all identified risks. Risk analysis identifies and evaluates each relevant risk, determines that risk's potential impact, and itemizes the controls that will be used to respond appropriately. Risk analysis is a prerequisite to implementing the risk management function. That is because a systematic risk analysis can precisely direct the prioritization of the organization's steps to manage risk.
The risk analysis function should also be able to conduct qualitative and quantitative analyses of any newly identified or emerging risk event. The risk analysis function should also be able to perform all necessary analyses to confirm that presently operational risks are fully characterized and contained. The outcome of the operation of the risk management function should be to confirm that the risks that the organization considers priorities are identified, agreed on, and addressed and that any emerging risks will be recognized and dealt with as they appear.
Risk Response
Once the analysis function is established and operating, the organization's chosen responses to facilitate significant risk must be designed and deployed. The response to each considerable risk should always be a substantive and correct set of operational procedures supported by the appropriate technology. Because the whole organization is involved, the response should be feasible and understandable to the general constituencies of the organization. The response should be shown to mitigate the predictable impacts of any identified risk provably.
Since most projects have infinite risks, the risk response targets must be precisely established within every organization. Essentially, this is a scoping process. It answers two different but highly related questions for the organization's decision-makers. The first is: "What is the certainty of each identified risk occurring?" The second is, "What is its anticipated impact if it does occur?" The answer to those two questions is typically conveyed to decision-makers as an appraisal of the loss, harm, failure, or danger for every identified risk. The assessment results will then guide the deployment and subsequent conduct of the risk response process.
Once the risk response is appropriately targeted, optimum risk management policies can be defined and implemented. The risks are analyzed as they are identified, and the priority the mitigation ought to receive is determined. This is normally dictated by the danger of the risk and the resources required to ameliorate it. Then, once the risk mitigation decision has been made, the prescribed mitigations are designed, developed, applied, and then continuously evaluated to determine whether progress has been made toward the proper mitigation of the risk.
Continuous monitoring
The organization also must regularly monitor the changes in the operational risk environment. The monitoring can be done through systematic testing and reviews. It can also be carried out during day-to-day execution.
The organization must also regularly survey the existing risk environment. That is necessary to identify and mitigate any new threats that might arise. Formal testing and reviews and periodic audits of the security function typically underwrite the monitoring. Continuous monitoring must apply uniformly across the organization. Therefore, it is established through a strategic planning process. The strategic planning for risk management develops and implements the organizational policies about risk. These are documented in a detailed risk management plan. The plan is then utilized to organize and run a rational risk management operation. In most cases, that planning process will dictate specific actions to produce the desired outcome for every significant risk. Those outcomes are prioritized in terms of their criticality.
The strategic planning process for risk monitoring aims to maintain an effective set of formal controls to manage each risk. Along with those controls, strategic risk management planning is also responsible for assigning the specific employee roles and responsibilities required for managing each risk. Finally, the plan describes the process that will be used to evaluate and improve the overall risk management function, including how to use the lesson learned to change the form of the response.
Takeaways
Information and communication technology (ICT) security risks are a journey unique to your organization. Have a comprehensive risk management process to identify, measure, evaluate, monitor, report, and control or mitigate all ICT risks:
- Determine the risk appetite for ICT and security risks in accordance with the risk appetite of the organization;
- Identify and assess the ICT and security risks;
- Define mitigation measures, including controls;
- Monitor the effectiveness of these measures as well as the number of reported incidents, and take action to correct the measures where necessary;
- Report to the management body on the ICT and security risks and controls;
- Identify and assess whether any ICT and security risks resulting from any significant change in the ICT system or ICT services, processes, or procedures and/or after any significant operational or security incident.
References
- https://www.enisa.europa.eu/topics/risk-management/current-risk/business-process-integration/the-enisa-rm-ra-framework
- https://www.experts-exchange.com/articles/36691/IT-Risk-Management.html
- https://www.experts-exchange.com/articles/35333/RISK-ASSESSMENT-METHODOLOGY.html
- https://www.experts-exchange.com/articles/37671/Audit-Plays-a-Vital-Role-in-Risk-Assessment.html
- https://www.experts-exchange.com/articles/34811/The-Principles-Of-Information-Cybersecurity-CIA-Triad.html
- https://www.experts-exchange.com/articles/33451/Building-a-Robust-Security-Awareness-Program.html
- https://www.iso.org/iso-31000-risk-management.html
- https://csrc.nist.gov/Projects/risk-management
- https://www.iso.org/obp/ui/#iso:std:iso-iec:27002
- https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/final
- https://csrc.nist.gov/publications/detail/sp/800-39/final
- https://www.cdc.gov/phlp/publications/topic/hipaa.html
- https://www.pcisecuritystandards.org/
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.




Comments (0)