From Crisis to Prevention: Managing Data Breaches Effectively
Data Breach
The term “Breach” in the digital world can be used to describe a privacy violation, particularly when personal data is improperly disclosed. It may also indicate a violation of the organization's defenses, security measures, policy or obligations, among other things.
In addition to digital computer data, “data” can refer to information in different formats, operating systems, applications or simply the “data content.”
Data Privacy
The term “Data Privacy” in the digital world describes the collection of rules, guidelines and practices organizations use to safeguard the private and sensitive data of their clients, staff members and other stakeholders. In accordance with relevant laws, rules and industry standards it entails the appropriate handling, processing, storing and sharing of data.
Data privacy encompasses various aspects, such as:
- Collection
- Storage
- Usage
- Sharing
- Retention
- Compliance
- Transparency
- Governance
- Individual Rights
- Data Protection by Design and Default
- Accountability
Verizon's Data Breach Investigations Report
The recent analyses show that cybersecurity failures leading to data breaches and ransomware (for example, from IBM, Verizon, Cisco, etc.) continue to accelerate alarmingly. The rising number of data breaches is evidence that we are facing a cybersecurity crisis-and it is time for a change.
A significant contributing factor to these breaches is not external hacking attempts but insider threats, often resulting from successful phishing attacks. This highlights the importance of employee awareness regarding cybersecurity risks.
In today's increasingly digital world, we depend on passwords to keep us secure while conducting business online or accessing the organization's critical applications while working remotely.
In 2023, according to Verizon's Data Breach Investigations Report:
- 67% of application attacks result from compromised passwords.
- 82% of data breaches involve stolen credentials and phishing.
Based on these findings, it is obvious that compromising or stealing passwords is relatively easy, making them the weakest link in security.
In 2024, according to Verizon's Data Breach Investigations Report:
- 24% of breaches involved stolen credentials.
- 32% of breaches included ransomware and extortion, with a 23% share from ransomware alone.
The human element was a factor in 68% of breaches, including phishing and social engineering.
15% of breaches involved third-party systems. Exploitation of vulnerabilities increased by 180%, driven by zero-day attacks. The report highlights the continued dominance of human-related risks and vulnerabilities in driving breaches.
Equifax Case Study
Equifax is one of three major Credit Reporting Agencies (CRAs) primarily serving the U.S. market. As a CRA, they maintain business relationships with banks, credit card organizations and other lenders and financial institutions. Equifax maintains records of individuals' financial history and personal details such as name, age, Social Security number, personal addresses, phone numbers and work history. They collect this data from lending institutions with whom they have a relationship and from public records.
Later, in 2017, Equifax was the target of a hack and data breach that exposed some or all of the stored information for approximately 148 million individuals (~44% of the U.S. population), including some in Canada and the UK. Equifax became aware of this breach on July 29, 2017 and publicly announced the breach on September 7, 2017. After an investigation into the breach, a report by the House Oversight Committee concluded that Equifax had failed to take basic precautions to secure the data. The systems were old and outdated, the practices and policies were sub-par, data was kept unencrypted and the breach was entirely preventable.
Effectively Managing Data Breaches
Organizations lose sensitive data due to outsider attacks or insider actions. Data breaches must be responded to well by affected parties and reviewed thoroughly.
External threats do not solely cause data breaches. Internal errors, negligence or deliberate actions by employees or partners also play a significant role. Accidental data sharing on unsecured platforms or malicious disclosure for financial or personal motives can lead to breaches. Insider threats are particularly challenging to detect and address due to their familiarity with organizational vulnerabilities.
For an organization today, data is the most valuable asset. It drives innovation, enables customers’ personalized experiences and forms the basis of decision-making. As data becomes more useful, it is increasingly at risk of a breach. It is something we have seen more of in recent years and it is something that threatens organizations of all shapes and sizes.
Organizations don’t realize how much work is involved in dealing with a data breach because there are many tasks, responsibilities and obligations to consider and deal with to make things right.
The Enormous Damage Potential of Data Breaches
Data breaches can hurt the bottom line and weaken customer and partner confidence. Fixing a data breach takes weeks or months and can use many resources, which can be costly. When an organization loses sensitive information, it can cause them to lose money and reduce their ability to compete.
Many organizations’ competitive advantage stems from their Intellectual Property (IP). If this information is leaked to the wrong person and they use it first, they’ll improve their product or service.
If a data breach is made public, these third parties will ask how much data they lost. However, providing clear answers during a breach is challenging, as the full extent may not yet be known.
If organizations' data gets lost, it could hurt their trust with customers, business partners or even their own employees, which is a significant reputational hit.
Third-Party Risk Management
IT vendor and third-party risk management have become major concerns for organizations. There is an increased reliance on products and services offered by third-party vendors, which increases the probability of security incidents, data breaches and other risk exposure. Many of the most significant data breaches in recent years originated through vendor access to enterprise networks. Increased risk exposure from IT vendors requires organizations to take an active role in managing and mitigating third-party risk before negative impacts are faced by their customers or operations. Best practices in managing risk from IT vendors include:
- Performing risk assessments on all potential IT vendors before awarding contracts.
- Including right-to-audit clauses in all vendor contracts.
- Providing the minimum access required to vendors.
- Maintaining an accurate inventory of all IT vendors and the level of access provided.
- Removing vendor access when the relationship ends.
- Monitoring and certifying all IT vendors regularly.
Addressing a data breach requires substantial internal resources and efforts from cyber specialists. Their work involves data analysis, communication with stakeholders and implementing damage control measures, often with the assistance of external experts like IT forensic professionals, crisis managers and lawyers. Beyond the disruption of operations, organizations face fines and the costs associated with external services, all of which add up to significant expenses.
Data Breaches Often Remain Undetected for Long Periods
Data theft can happen in various ways: due to an outside Internet attack, a lost USB stick, hitting “reply all” on a misdirected email or insider action. Insider threats are especially worrisome as employees or ex-employees use their knowledge about network settings and vulnerabilities against the organization.
External attacks often start with breaches through zero-day exploits or social engineering tactics like phishing, leading to credential theft and system access. Attackers escalate privileges to get access to vital systems by moving laterally throughout the IT network. Since attackers want to go undetected and leave no evidence behind, data exfiltration can go unreported for a long time.
Key Steps in Addressing a Data Breach
Best practices in addressing a data breach include:
- Locate and Contain the Breach: Identify affected information systems and the breach entry point quickly. Mobilize IT forensic experts to analyze the attack and contain its spread.
- Analyze Exfiltrated Data: Conduct forensic investigations to evaluate the scope and impact of the stolen data. This step can be resource-intensive and time-consuming.
- Notify Authorities and Affected Parties: Notification must detail the nature of the violation and include specific information about affected data and individuals.
- Inform Stakeholders: Communicate transparently with affected individuals and stakeholders to restore trust and demonstrate accountability.
- Utilize Technology for Data Review: Utilizing (AI) Artificial intelligence and (ML) machine learning in e-discovery systems to analyze vast volumes of data, identify sensitive information and speed up the repair process.
Key Steps in Preventing a Data Breach
Strong measures should be put in place to stop incidents from happening and be ready if something occurs (incident readiness or data breach readiness). Organizations must recognize the complex nature of data breaches and respond promptly during events. Best practices in preventing a data breach include:
- Security Awareness Training: It helps employees ensure they have adequate protections and safeguards for the data they handle.
- Unified threat management (UTM): Implementing UTM’s web filtering can prevent users from seeing websites with a bad reputation or URLs. This is done by stopping user's browsers from loading the pages from those sites onto their devices. UTM can be configured to target certain sites according to organizational objectives.
- Data Loss Prevention (DLP): Implementing DLP prevents data loss and exfiltration. It typically sits between the internal network and the Internet, inspecting all traffic flowing in and out of the organization. DLP can help prevent data breaches by identifying sensitive data and blocking attempts to send it outside the organization. The DLP solution can be attached to a UTM appliance to enable the user to detect and prevent data breaches and exfiltration attempts.
- Privileged Access Management (PAM): Deploy a PAM solution to manage and monitor privileged accounts. Justification and approvals are required for elevated access, which can be granted temporarily for specific tasks. Log and audit all privileged actions to ensure transparency and accountability.
- Security Protocols: Outdated protocols are a major risk, leaving the organization prone to security incidents and data breaches. For example, mismanaged certificates- Failure to properly manage, issue, renew or revoke digital certificates greatly impacts organizational security. Expired certificates can lead to unexpected outages and be gateways for bad actors to move laterally within an organizational network, leading to data breaches that impact an organization's security and compliance posture. Keep using the latest security protocols.
- Identity-as-a-service (IDaaS): Refers to identity and access management (IAM) services provided through the cloud on a subscription basis. Identity-as-a-Service (IDaaS), offered by cloud service providers, delivers digital identity solutions through out-of-band cryptographic systems (hardware or software). It offers advanced authentication methods, such as MFA, which can enhance security and reduce the risk of data breaches through compromised credentials. Before selecting an IDaaS provider, organizations should conduct a thorough risk assessment and evaluate the provider's reputation and compatibility with their organizational business and security needs.
- Encryption: Industry experts agree that organizations must take control of sensitive data wherever it resides—whether in transit or stored on a server, on or off organization premises. Encryption can reduce or eliminate the impact of a data breach, should it occur. Modern encryption standards, such as AES-256, TLS 1.3 and end-to-end encryption, should be prioritized.
Security Protocols
Maintaining up-to-date and appropriate protocols is critical. Here are key categories to consider:
- Cryptographic Protocols: TLS (Transport Layer Security), SSL (Secure Sockets Layer), IPsec (Internet Protocol Security), PGP/GPG (Pretty Good Privacy / GNU Privacy Guard) and Code-Signing Certificates.
- Email Security Protocols: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting and Conformance).
- Web and Internet Security: HTTP Strict Transport Security (HSTS), DNSSEC (Domain Name System Security Extensions), SFTP (Secure File Transfer Protocol) and STARTTLS (Start Transport Layer Security).
- Identity and Access Management: OAuth2 / OpenID Connect, Kerberos, SAML (Security Assertion Markup Language), Zero Trust Protocols and LDAPS (LDAP over SSL/TLS).
- Wireless and Network Security: WPA2/WPA3 (Wi-Fi Protected Access), MACsec (Media Access Control Security), OpenVPN, WireGuard, RADIUS (Remote Authentication Dial-In User Service) and NTPsec (Network Time Protocol Secure).
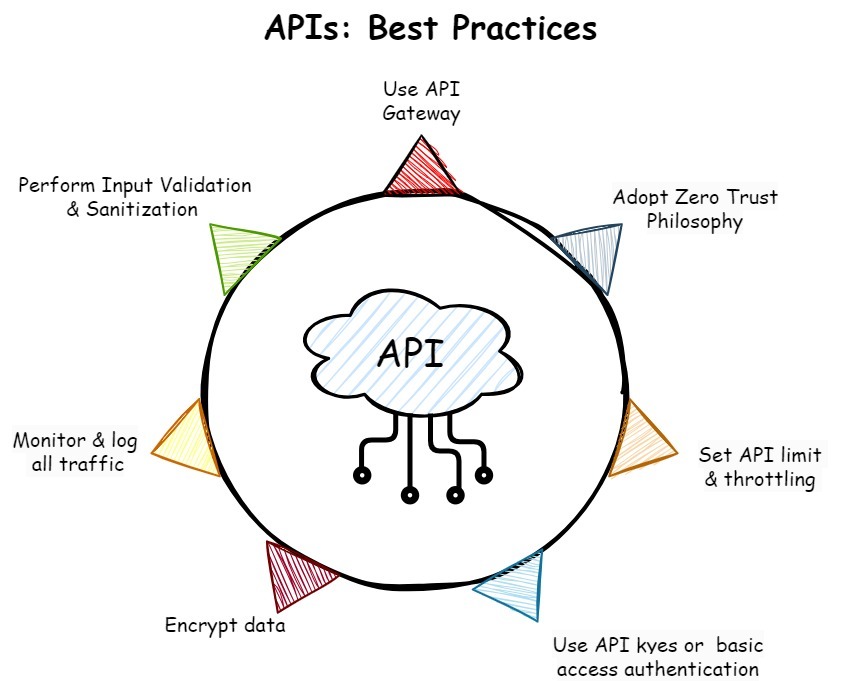
API Security Best Practices
A strong security posture requires adhering to API security best practices. These methods consist of:
- Use API Gateway
- Adopt Zero Trust
- Set API Limits and Throttling
- Use API Keys or Basic Access Authentication
- Encrypt Data
- Monitor and Log All Traffic
- Perform Input Validation and Sanitization
Conclusion
Considering the importance of data, organizations need to implement strong plans that incorporate both proactive and reactive actions. Strong IT security system implementation, preparedness process maintenance and frequent staff training are examples of proactive measures. Quick decisions backed by cutting-edge technology and outside knowledge are essential to resolve a breach effectively. Organizational and technological measures can be balanced to help organizations effectively control the risks and consequences of data breaches.
References
https://www.verizon.com/business/resources/reports/dbir/
https://www.experian.com/data-breach/knowledge-center/reports-guides/data-breach-industry-forecast
https://www.experts-exchange.com/articles/37693/Zero-Trust-Begins-With-Identity.html
https://www.experts-exchange.com/articles/36691/IT-Risk-Management.html
https://www.experts-exchange.com/articles/37631/Transform-From-Trust-to-Zero-Trust.html
https://www.experts-exchange.com/articles/35333/RISK-ASSESSMENT-METHODOLOGY.html
https://www.experts-exchange.com/articles/39277/Zero-Day-Exploits-The-Invisible-Threats.html
https://www.esecurityplanet.com/trends/the-best-security-for-wireless-networks/
https://www.bl.uk/home/british-library-cyber-incident-review-8-march-2024.pdf/
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (0)